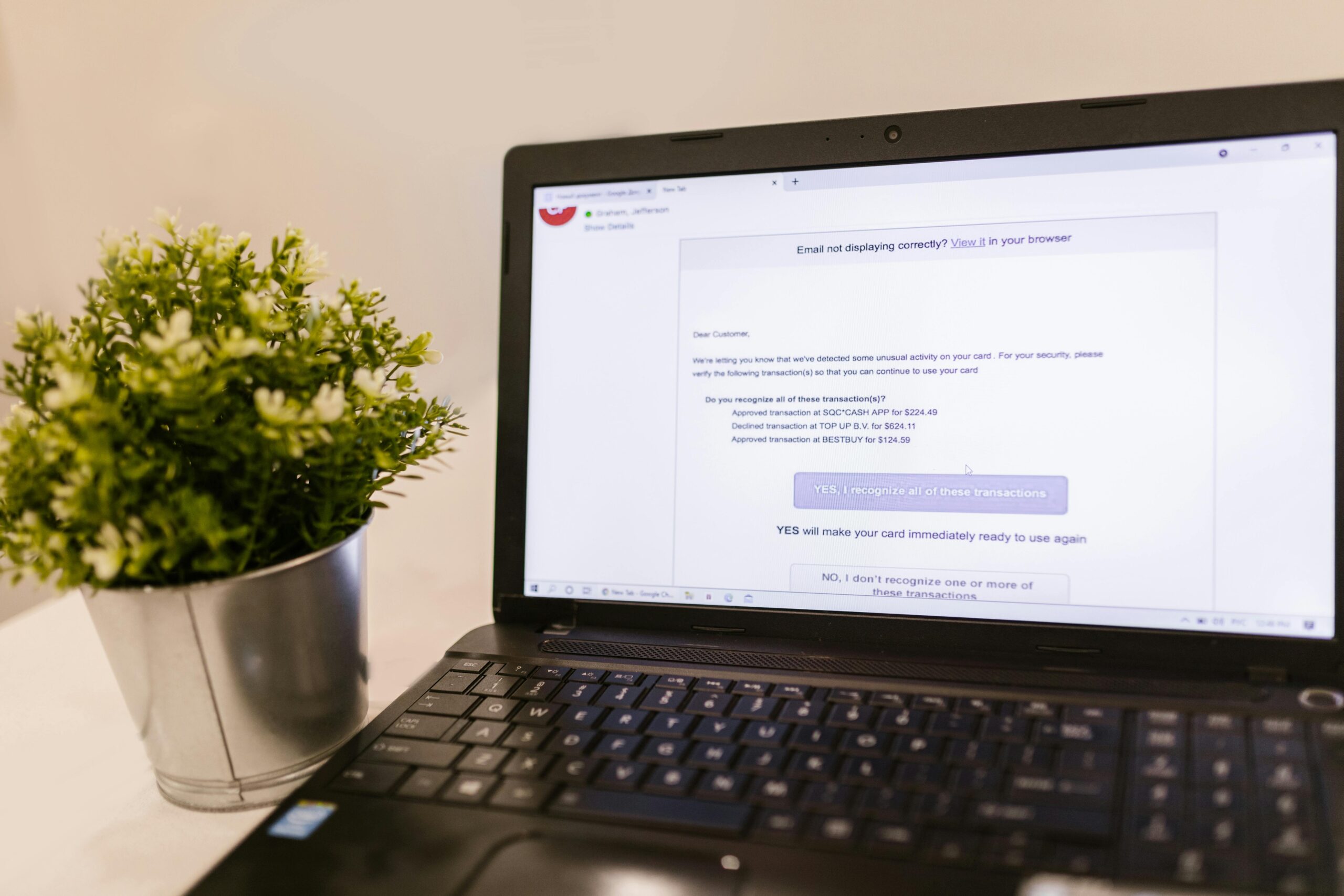
Criminals are rapidly weaponizing AI, deepfakes, and automation to scale tech scams against consumers and businesses. The FBI’s Internet Crime Complaint Center (IC3) logged $12.5 billion in reported cybercrime losses in 2023 (FBI IC3), with business email compromise (BEC) remaining the costliest category. In early 2024, Hong Kong police reported a single deepfake video call that tricked a finance employee into wiring approximately $25 million to scammers (Reuters). While full-year 2025 figures are still pending from official sources, evidence shows impersonation fraud and AI-generated lures are accelerating. This guide distills the latest patterns and gives you precise steps to protect your accounts, devices, and money today.
AI Deepfake Scams
Recent Cases and Financial Impact
Criminals now use AI to clone voices, faces, and writing style with alarming realism. In one widely reported case (Feb 2024), a finance worker joined a video call with what looked and sounded like company executives; it was a deepfake. The attackers walked the victim through a series of transfers totaling about $25 million (Reuters). The FBI has warned that AI-enabled impersonation is increasingly used to amplify fraud, from fake support agents to bogus investors and romantic partners (FBI IC3, PSA).
Key impacts documented by authorities and respected security reports include:
- Overall reported cybercrime losses reached $12.5 billion in 2023 (FBI IC3).
- BEC—often enhanced by AI—accounted for more than $2.9 billion in adjusted losses in 2023 (FBI IC3).
- Older adults (60+) lost $3.4 billion to cyber-enabled fraud in 2023, with among the highest median losses per victim (FBI Elder Fraud Report 2023).
How This Scam Works
- Recon: Criminals scrape public bios, earnings calls, and social media to capture voice/video samples of executives, celebrities, or relatives.
- Clone: They train models to mimic speech, accent, cadence, and facial expressions. Email and chat style are also imitated.
- Set the stage: Targets receive urgent messages about wire transfers, investments, vendor disputes, or family emergencies.
- Live deception: Attackers host a video call or phone call where a deepfaked leader or loved one directs payment, gift card codes, crypto transfers, or confidential access.
- Obfuscate: Funds are split through money mules, crypto mixers, or cross-border accounts to frustrate recovery efforts.
Warning Signs
- Urgent requests for secrecy, immediate payment, or bypassing normal approval channels.
- Slight audio/video oddities: unnatural blinking, latency, audio desync, or a caller refusing to repeat uncommon words.
- New or changed payment coordinates without a verified paper trail.
- Requests to switch to encrypted or personal messaging apps to avoid corporate logging.
Protection Strategies
- Out-of-band verification: For any money movement or sensitive data, call back using a trusted phone number already on file—never the number provided in the message.
- Challenge-response protocols: Use code phrases known only to verified team members or family. Enforce for high-value transfers.
- Meeting policies: Require cameras on, random gestures (“please touch your left ear”), and multi-party confirmations for large approvals.
- Data minimization: Limit executive voice/video samples online; lock down social media privacy and remove high-fidelity recordings when possible.
- Technical controls: Deploy anti-impersonation and anomaly detection in email, collaboration tools, and payment systems; log and alert on deviations.
Business Email Compromise (CEO/Vendor Impersonation)
Recent Cases and Financial Impact
BEC is consistently the most expensive cybercrime category tracked by the FBI, with over $2.9 billion in adjusted losses reported in 2023 (FBI IC3). Attackers hijack email threads, register lookalike domains, or use AI to write perfectly fluent messages to finance, procurement, and payroll teams. Verizon’s 2024 Data Breach Investigations Report highlights that the human element remains central to breaches, underscoring the risk of convincingly crafted social engineering (Verizon DBIR 2024).
How This Scam Works
- Initial access: Credential theft via phishing, MFA fatigue attacks, or exploiting weak mail rules.
- Thread hijack: Attackers quietly monitor inboxes, learn approval flows, and reply inside active vendor or M&A threads.
- Payment diversion: They submit a bank account “update,” altered invoice, or urgent wire request that looks routine.
- Cash-out: Funds are laundered via money mules, crypto off-ramps, or foreign accounts.
Warning Signs
- Bank change requests without a signed, verified vendor form.
- Emails sent just after business hours or when executives are traveling.
- Subtle domain typos (e.g., rn instead of m), newly registered domains, or display-name spoofing.
- Unexpected pressure to bypass standard procurement or AP workflows.
Protection Strategies
- Payment controls: Enforce out-of-band voice verification for any new/changed vendor banking details and wires above a set threshold.
- Email authentication: Implement SPF, DKIM, and DMARC at quarantine/reject; monitor DMARC reports for abuse.
- Access hardening: Mandate phishing-resistant MFA (FIDO2/passkeys), disable legacy protocols, and review forwarding rules.
- Role-based permissions and dual approvals: Segregate duties; require 2+ approvers for large payments and vendor onboarding.
- Detection: Deploy BEC/impersonation classifiers and banner warnings for external senders; train staff on real-world BEC samples.
Tech Support Fraud (Fake Microsoft/Apple, Remote Access)
Recent Cases and Financial Impact
Tech support fraud disproportionately targets older adults. The FBI reports older adults lost $3.4 billion to online fraud in 2023 (FBI Elder Fraud Report 2023), and tech support ploys represent a significant share. IC3 has recorded tech support fraud losses exceeding $1 billion in 2023, with persistent patterns like fake antivirus pop-ups and scam calls claiming to be from Microsoft, Apple, or your bank (FBI IC3).
How This Scam Works
- Pop-up scareware: A browser popup says your device is infected and gives a phone number.
- Cold calls: Scammers spoof caller ID and pose as known brands or your bank’s fraud desk.
- Remote access: They ask to install software (e.g., AnyDesk) and “fix” issues while stealing data or moving money.
- Refund ruse: They “accidentally” refund too much and pressure you to return funds via gift cards, wire, or crypto.
Warning Signs
- Unsolicited calls about problems you didn’t report.
- Instructed to install remote access tools or change bank settings.
- Requests for gift cards, crypto, or wire transfers to “resolve” an issue.
- Pressure, secrecy, or claims that your account is under “federal investigation.”
Protection Strategies
- Never call the number in a popup. Close the tab, clear the browser cache, and restart.
- Use a known number on a card statement or the official website before speaking to “support.”
- Remove remote access software you don’t use; restrict admin rights.
- Enable bank transaction alerts; set daily transfer limits.
- For families: Create a simple “one-call” plan—call a trusted person before moving money.
Cryptocurrency Schemes (Fake Platforms, Draining Attacks)
Recent Cases and Financial Impact
Crypto fraud remains a major driver of losses. Chainalysis reports that illicit crypto transaction volume remained in the tens of billions in 2023, with scammers shifting from mass phishing to targeted “pig butchering” investment romances and sophisticated wallet-drainer malware (Chainalysis 2024 Crypto Crime Report). The FTC has repeatedly warned that crypto payments are a top channel for scammers because they’re fast and hard to reverse (FTC Consumer Advice/Data Spotlights).
How This Scam Works
- Fake investment apps: Fraudsters register convincing domains, show fake dashboards, and manipulate “profits.”
- Pig butchering: Long-game grooming turns into pressured crypto “opportunities.”
- Approval phishing: Malicious DApps and websites trick you into signing unlimited token approvals.
- Drainer kits: One bad click, and automated scripts sweep wallets in seconds.
Warning Signs
- Guaranteed returns, “limited seat” offers, or pressure to “reinvest” to withdraw.
- Wallet prompts you don’t understand; urgent signature requests.
- Support staff only available via Telegram or WhatsApp.
- Friends or “mentors” urging you to move funds off-exchange quickly.
Protection Strategies
- Use hardware wallets and split funds across multiple addresses.
- Review on-chain approvals regularly; revoke anything you don’t recognize.
- Verify platform licensing and corporate registration; search the company name + “scam” + “complaints.”
- Never invest because of pressure or romance. Ask a neutral third party to review first.
- Enable withdrawal allowlists and delays; keep large holdings in custody with strong controls.
Romance and Social Engineering (Pig Butchering)
Recent Cases and Financial Impact
Romance scams continue to inflict multi-billion-dollar damage. The FTC has documented more than a billion dollars in yearly losses attributed to romance scams in recent reporting, with median losses among the highest of all fraud types (FTC Data Spotlights). Criminals increasingly mix romance with crypto investment ploys and voice cloning to create an aura of authenticity.
How This Scam Works
- Match: Scammers create polished profiles, often stealing photos from real people.
- Groom: Weeks of emotional bonding, support, and daily messages.
- Hook: They introduce “safe” investment platforms, real estate deals, or urgent emergencies.
- Drain: After initial “wins,” they demand larger deposits and block withdrawals—then disappear.
Warning Signs
- Won’t meet in person or video chat, or uses excuses about camera issues or security.
- Quickly moves the chat to encrypted apps and asks for money or crypto.
- Stories that provoke sympathy: medical bills, customs fees, military leave, or sudden emergencies.
Protection Strategies
- Reverse image search profile photos; look for duplicates across names.
- Never send money, gift cards, or crypto to someone you haven’t met in person.
- Ask a trusted friend to sanity-check before any transfer.
- Use dating app safety features; report suspicious profiles promptly.
Phishing Evolution (AI Email, Smishing, Vishing, QRishing)
Recent Cases and Financial Impact
Generative AI has made phishing emails grammatically perfect, localized, and personalized at scale. Verizon’s 2024 DBIR found the human element remains a factor in the majority of breaches, with social engineering a repeat entry point (Verizon DBIR 2024). The FBI has also warned about “QRishing”—malicious QR codes placed on parking meters or invoices that send victims to fake payment portals (FBI IC3 PSA).
How This Scam Works
- Email phishing: Spoofed invoices, security alerts, and payroll updates that look flawless.
- Smishing: Texts pretending to be USPS/UPS delivery issues, bank fraud alerts, or two-factor codes.
- Vishing: Call-center operations impersonate IT or bank staff; AI voice cloning adds credibility.
- QRishing: Tampered QR codes redirect to credential harvesters and fake wallet apps.
Warning Signs
- Unexpected password reset prompts or MFA requests you didn’t initiate.
- Links that resolve to lookalike domains; shortened URLs hiding true destinations.
- Voicemails or calls pressuring immediate verification or payment.
- QR codes placed over official stickers or printed on unsecured flyers.
Protection Strategies
- Use passkeys or FIDO2 security keys for phishing-resistant MFA.
- Hover to preview links; type known URLs directly into the browser.
- Block SMS from unknown senders; use banking apps for official messages.
- Verify delivery problems in the carrier’s official app, not via links.
- For businesses: Turn on DMARC enforcement, TLS reporting (TLS-RPT), and brand indicators (BIMI) for email.
Audience-Specific Guidance
General Consumers
- Set account alerts for transfers, new payees, and failed login attempts.
- Freeze your credit at Experian, Equifax, and TransUnion; unfreeze only when needed.
- Use passkeys or hardware security keys where available; enable automatic OS and browser updates.
- Use a password manager to generate unique passwords; never reuse banking credentials.
- If scammed: Contact your bank immediately, file at reportfraud.ftc.gov and ic3.gov, and save all evidence.
Business Owners and Finance Leaders
- Require out-of-band callback verification for new vendors and bank changes; document the call.
- Enforce least privilege, separation of duties, and dual approvals for payments.
- Mandate phishing-resistant MFA (FIDO2/passkeys) and disable legacy email protocols.
- Implement EDR/XDR on endpoints, conditional access, and impossible-travel detection.
- Run quarterly BEC tabletop exercises; test your incident response and recovery playbooks.
Elderly Users and Caregivers
- Use call-screening features and block unknown numbers; register on Do Not Call lists.
- Before moving money, call a trusted family member or caregiver using a known number.
- Set bank transfer limits and alerts; add a trusted contact at your financial institution.
- Never give remote access to anyone who calls you first. Hang up and call your bank or device maker directly.
Tech-Savvy Users
- Adopt passkeys; use hardware tokens for critical accounts and admin roles.
- Inspect email headers (SPF/DKIM/DMARC), WHOIS/domain age, and TLS cert details for suspicious messages.
- Use sandboxed browsers/VMs for high-risk sites; restrict wallet approvals; monitor for drainers.
- For deepfakes: Check for low-light artifacts, unnatural blinking/eye tracking, audio spectral oddities, and request dynamic movements on video calls.
Industry Expert Insights
The consensus across FBI, FTC, and leading cybersecurity firms is clear: AI is lowering the cost and skill barrier for criminals. Email and messaging platforms are the first line of contact, but payments are the endgame. BEC losses remain massive because they exploit trust and process gaps—not just technology. For consumers, the biggest breakthroughs are passkeys and account alerts; for businesses, it’s verification workflows and policy discipline. Expect more deepfake-enabled social engineering and hybrid scams that blend romance, investment hype, and corporate impersonation. Organizations that align identity controls (MFA, least privilege), email authentication (DMARC), and strong payment verification will see outsized risk reduction.
Immediate Action Steps
- Turn on passkeys or hardware-key MFA for email, bank, and crypto accounts today.
- Set real-time alerts for all transfers and new payees; add daily transfer caps.
- Create a two-step money movement rule at home and work: request + out-of-band callback.
- For businesses: Enforce DMARC reject, block legacy auth, and require dual approvals on wires.
- Build a “deepfake challenge” protocol for high-risk video calls (code phrase + movement challenge).
- Back up devices and wallets; store recovery keys offline; practice account recovery steps.
- If you suspect fraud: Contact your bank immediately, freeze accounts, file with FTC (reportfraud.ftc.gov) and FBI (ic3.gov), and notify local law enforcement.
Conclusion
Tech scams in 2025 are faster, more personalized, and harder to spot—especially when AI and deepfakes are involved. But simple, consistent habits still stop the majority of losses: verify money moves out-of-band, use phishing-resistant MFA, enforce payment discipline, and slow down any request wrapped in urgency or secrecy. Share this playbook with your team and family, lock in the controls today, and turn every urgent request into a verified process—not a costly mistake.
Editor’s note on sources and recency: This article cites authoritative datasets (FBI, FTC, Verizon, Chainalysis) and high-confidence case reporting. Where 2025 year-to-date figures are still pending public release, we reference the most recent verified numbers (through late 2023/early 2024) and provide source links below so you can confirm the latest updates as they are published.