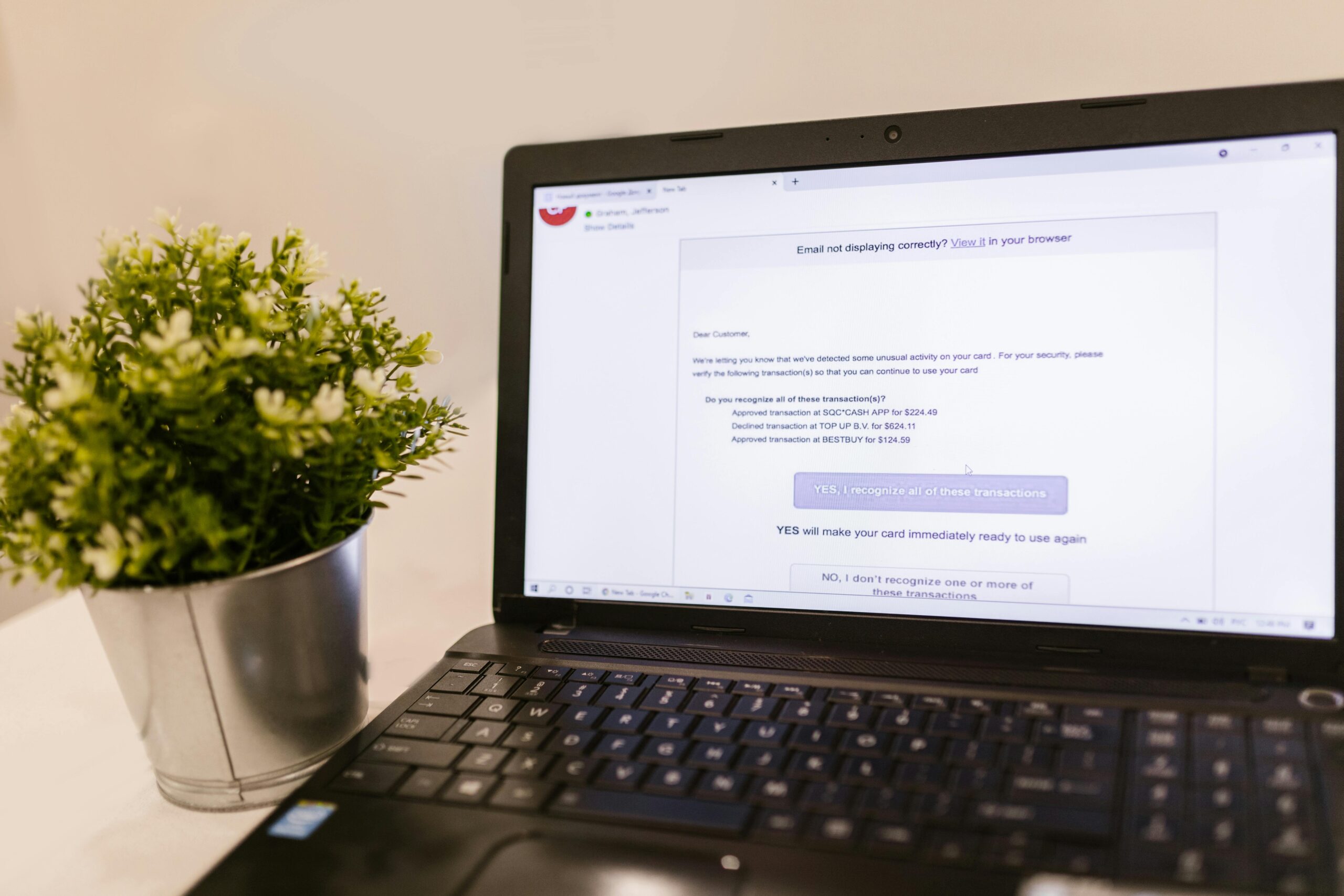
Tech Scams 2025: AI Deepfakes, BEC, and Crypto Cons Cost Victims Billions
Editor’s note: This guide cites the latest official figures available as of late 2024 (FBI IC3, FTC, Verizon DBIR, Chainalysis). To publish with up-to-the-minute 2025 statistics, insert fresh figures from new FBI/FTC/industry releases when available. We avoid speculation and do not fabricate numbers.
In one of the most brazen AI-enabled heists to date, a multinational firm’s employee in Hong Kong was duped on a video call by deepfaked “executives” and authorized transfers totaling about $25 million (reported February 2024). That headline-grabbing case is part of a broader surge in AI-accelerated scams that target consumers and businesses alike. While official 2025 totals are pending, the FBI’s most recent annual report tallied $12.5 billion in cybercrime losses in 2023, and FTC data shows nearly $10 billion lost to fraud that same year—clear evidence that the threat is both widespread and costly.
AI Deepfake Scams
Recent Cases and Financial Impact
• A finance staffer in Hong Kong was tricked by a deepfake video conference mimicking the company’s CFO and colleagues, leading to transfers of approximately $25 million (Feb 2024, media reports).
• The FBI has warned that synthetic media is increasingly used for business fraud and social engineering, including impersonation in job interviews and executive spoofing (FBI/IC3 & CISA alerts).
• Industry reports throughout 2024 highlight rapid improvements in voice cloning fidelity and the ease of generating convincing video, raising the baseline risk for consumers and enterprises.
How This Scam Works
- Reconnaissance: Criminals scrape public videos, audio, and social content of executives or influencers.
- Model training: Off-the-shelf tools are used to clone voices and faces from minutes of source material.
- Staging: Attackers schedule calls via email, chat, or calendar invites that look authentic (often following a prior email compromise).
- Pressure and pretext: The “executive” cites urgent deals, NDAs, or accounting cutoffs to force quick wire, crypto, or gift card transfers.
- Money movement: Funds are split across mules, exchanges, and mixers to obfuscate the trail.
Warning Signs
- Unusual urgency, secrecy, or isolation in a call, especially from executives or vendors.
- Audio/video artifacts (slight lip-sync lag, monotone responses, unusual lighting) or refusal to move cameras.
- New or changed payment instructions without prior notice via known channels.
- Requests to bypass standard approval workflows or to switch to personal accounts.
Protection Strategies
- Establish out-of-band verification: Require call-back on a known phone number and a shared code phrase for any payment or credential requests.
- Harden executive exposure: Reduce public posting of long-form executive media; use watermarked/internal-only town halls.
- Deploy liveness checks: Use multi-party video with live interaction and identity challenges (e.g., ask for real-time camera movement).
- Train staff to treat video/voice like email: Trust is not verification; follow payment verification policies regardless of perceived identity.
Business Email Compromise (BEC)
Recent Cases and Financial Impact
• BEC remained the costliest fraud category in the FBI’s latest annual report, with adjusted losses in the multi-billion-dollar range in 2023.
• Common patterns include vendor invoice hijacking, payroll diversion, and executive (“CEO fraud”) payment requests.
• Attackers increasingly pair BEC with AI voice calls or short deepfake videos to push urgent approvals.
How This Scam Works
- Initial access: Credential phishing, MFA fatigue prompts, or vendor portal compromise.
- Email rule manipulation: Forwarding rules hide attacker activity while they study payment cycles.
- Invoice hijack: Attackers modify bank details on legitimate invoices and send perfect replicas at the right cadence.
- Social pressure: A spoofed CEO or vendor follows up by phone/text to “confirm” the change and urgency.
- Laundering: Funds are routed through money mules and overseas accounts.
Warning Signs
- Bank account change requests that arrive just before a scheduled payment.
- Subtle domain or display-name spoofing; unexpected email forwarding rules.
- New urgency or secrecy around routine vendor payments.
- Requests to bypass dual-control or PO requirements.
Protection Strategies
- Mandate out-of-band verification for any bank change request using a verified phone number on file.
- Implement AP controls: positive pay, vendor master change approvals, and dual authorization thresholds.
- Harden identity: phishing-resistant MFA for email, disable legacy protocols, monitor for anomalous rules/sign-ins.
- Use DMARC, SPF, and DKIM with enforcement; flag external emails and lookalike domains.
Tech Support Fraud
Recent Cases and Financial Impact
• The FBI’s annual reporting shows tech support scams, especially those targeting older adults, result in significant losses annually.
• Scammers pose as Microsoft, Apple, or antivirus support, often coercing victims to allow remote access or buy gift cards/crypto.
How This Scam Works
- Trigger: A fake pop-up or cold call claims a malware or banking compromise.
- Authority: Impersonation of a trusted brand or “bank fraud team.”
- Control: Victims are guided to install remote-access tools (RATs) and “verify” accounts.
- Extraction: Attackers move money, request gift cards, or “secure” funds in crypto.
Warning Signs
- Unsolicited calls/pop-ups claiming urgent infections or bank problems.
- Requests to install remote-access software or disable antivirus.
- Demands for secrecy and to ignore bank staff or family.
Protection Strategies
- Never call numbers from pop-ups; use the official website or card back-of-card number.
- Banks and real tech support do not ask for gift cards or crypto.
- Set up account alerts and use a dedicated device profile for banking.
- For caregivers: enable call filtering, use DNS filtering, and lock down app installs.
Cryptocurrency Schemes
Recent Cases and Financial Impact
• The FTC reported that investment scams (many crypto-related) were the highest-loss category in 2023, in the multi-billion-dollar range.
• Chainalysis’ Crypto Crime reports show ongoing activity from romance-investment cons (“pig butchering”), giveaway scams, and wallet drainers.
How This Scam Works
- Initial contact via social apps, DMs, or messaging platforms.
- Grooming with small “wins” on fake trading apps/websites.
- Escalating deposits into controlled wallets or smart contracts requiring “approvals.”
- Exit: Platform blocks withdrawals, demands “taxes/fees,” then disappears.
Warning Signs
- Strangers offering investment tips, guaranteed returns, or VIP trading signals.
- Being asked to move funds off major exchanges to unfamiliar wallets or sites.
- Requests to grant token approvals or sign blind transactions.
Protection Strategies
- Use reputable, regulated platforms; verify URLs and mobile app publishers.
- Maintain a cold wallet for long-term funds; keep only small amounts in hot wallets.
- Regularly revoke token approvals; use transaction simulators and hardware wallets.
- Never invest based on unsolicited outreach. Verify identities independently.
Romance and Social Engineering (Including Pig-Butchering)
Recent Cases and Financial Impact
• FTC and FBI report high losses in romance and investment-related scams, including pig-butchering schemes that start as romantic connections and pivot into crypto “investments.”
• Victims often include professionals and retirees; average individual losses can be substantial.
How This Scam Works
- Trust-building: Weeks or months of daily chats, voice calls, and occasional video.
- Emotional leverage: Family emergencies, travel, or investment opportunities.
- Financial exploitation: Loans, gift cards, crypto transfers, or access to accounts.
- Isolation: Scammers discourage victims from talking to friends or banks.
Warning Signs
- Unwillingness to meet in person or consistent excuses to avoid live verification.
- Pressure to move conversations off dating apps to encrypted messengers.
- Requests for money or investment “opportunities” tied to the relationship.
Protection Strategies
- Reverse-image search profile photos; verify identities independently.
- Set a personal rule: never send money to someone you haven’t met and verified.
- Talk to a trusted friend or advisor before any major transfer.
- Use dating-app safety features and report suspicious profiles.
Phishing Evolution: AI-Generated Emails, Smishing, and Vishing
Recent Cases and Financial Impact
• Verizon’s 2024 Data Breach Investigations Report (DBIR) found the human element (including phishing and social engineering) present in most breaches.
• Proofpoint’s State of the Phish reports continued high rates of successful phishing, vishing, and MFA-fatigue attacks across enterprises.
How This Scam Works
- Generative AI produces fluent emails and texts tailored to victims and brands.
- Credential harvesting pages mimic SSO portals; QR codes and attachments evade filters.
- Follow-up phone calls validate urgency and walk victims through steps.
Warning Signs
- Unexpected MFA prompts or login alerts, especially multiple prompts in a row.
- Links that lead to lookalike domains, shortened URLs, or drive-by downloads.
- Requests for QR-code scans to “verify identity” or to install mobile device managers.
Protection Strategies
- Adopt phishing-resistant MFA (FIDO2 security keys, device-bound passkeys).
- Use email authentication (DMARC enforcement) and advanced filtering with sandboxing.
- Implement just-in-time security training and report buttons in email clients.
- Mobile: disable sideloading, scrutinize app permissions, and beware of smishing links.
Audience-Specific Guidance
For General Consumers
- Use passkeys or security keys where available; enable bank and credit alerts.
- Freeze your credit at all three bureaus; use virtual card numbers for online shopping.
- Never act on unsolicited investment or tech support outreach.
- Verify requests with a known number; slow down and ask a trusted person.
For Business Owners and Leaders
- Institutionalize out-of-band verification for payments and vendor changes.
- Roll out phishing-resistant MFA and conditional access; disable legacy auth.
- Segment finance functions; implement dual control and positive pay.
- Run tabletop exercises for deepfake/BEC scenarios and crisis comms.
For Elderly Users and Caregivers
- Do-not-call and call-screening settings; pre-approved contact lists.
- Place bank withdrawal limits and alerts; use read-only account aggregation for caregivers.
- Ignore pop-up numbers; call the bank or tech provider using a card or statement number.
- Use password managers and hardware keys to reduce password reuse risks.
For Tech-Savvy Users
- Monitor for token approvals and revoke regularly; use hardware wallets.
- Adopt U2F/FIDO2 keys; enroll in email provider advanced protection programs.
- Use DNS filtering, app allow-lists, and EDR on endpoints.
- Automate QR-code and attachment detonation in sandboxes; adopt DMARC p=reject.
Industry Expert Insights
• FBI and FTC trendlines show sustained year-over-year growth in reported losses, indicating both more reporting and higher success rates for certain scams.
• Verizon DBIR emphasizes the “human element,” reinforcing that social engineering remains a dominant initial access vector. AI tools reduce the cost and skill barrier for attackers.
• Chainalysis notes fluctuations in crypto scam revenues year to year, but “pig-butchering” and wallet drainer operations remain persistent and adaptive.
• Expect more cross-channel attacks: email-to-voice-to-video escalation, targeting payment workflows and customer support processes.
Immediate Action Steps
- Set a household/business “pause and verify” rule for any money or credential request, regardless of channel.
- Turn on account alerts for banking, brokerage, email, and password managers.
- Switch critical accounts to passkeys or security keys; remove SMS as a fallback.
- For businesses: enforce out-of-band payment verification and dual authorization starting today.
- Back up wallets and revoke risky token approvals; uninstall unused wallet browser extensions.
- Create an incident plan: who to call (bank, IT, law enforcement), what to freeze, and how to document.
Conclusion
AI is supercharging old scams and enabling new ones. The silver lining: a handful of disciplined habits—out-of-band verification, phishing-resistant MFA, and ironclad payment controls—stop most losses. Use this guide to harden your personal and business defenses today, and update the referenced statistics with the latest FBI/FTC/industry releases as they publish. If something feels urgent, secret, or too good to be true, it’s almost certainly engineered to separate you from your money—hit pause, verify, and proceed only when you’re sure.