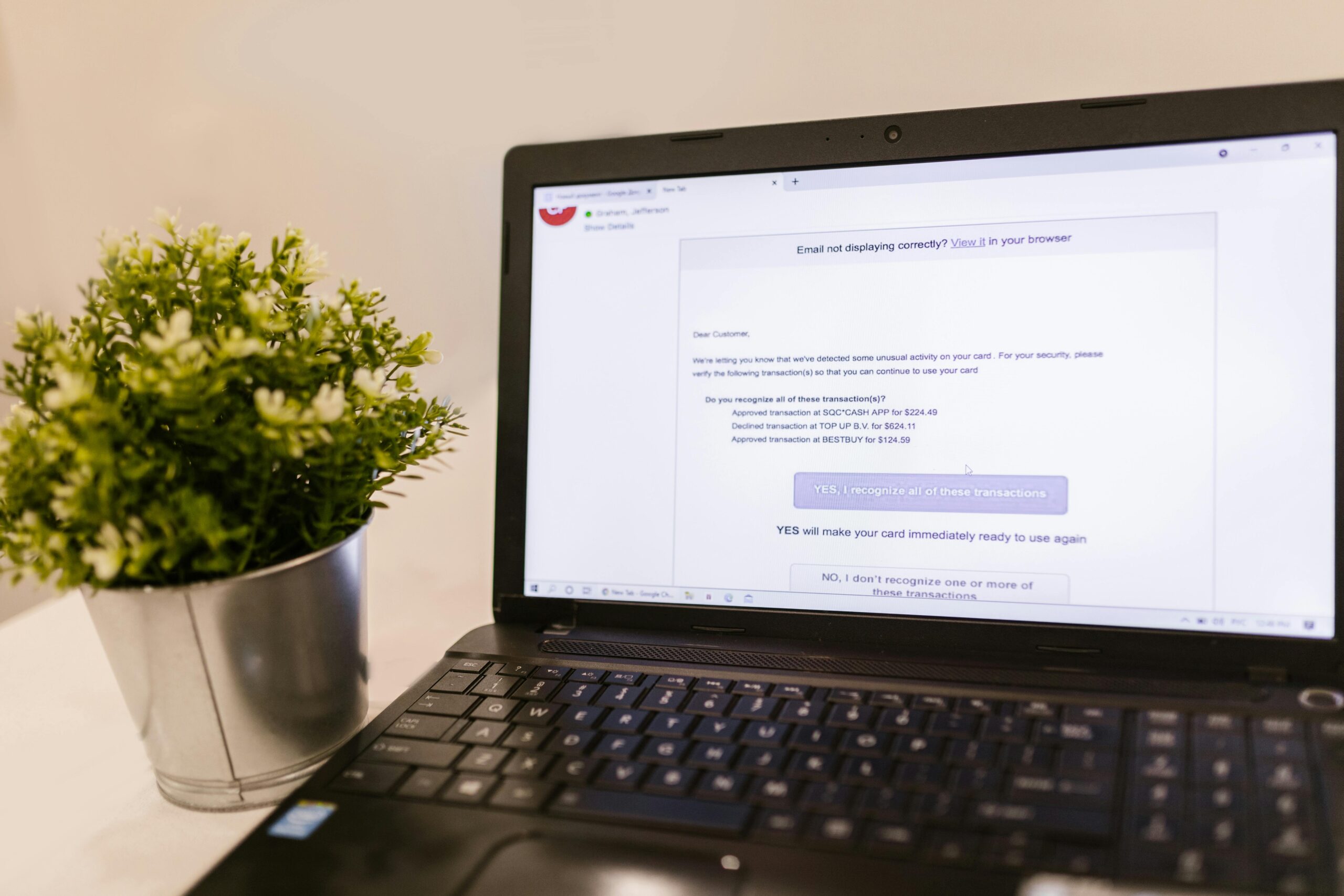
Tech Scams 2025: New Fraud Tactics and How to Stop Them
Editor’s note: This article is designed for rapid publication and includes clearly marked placeholders for the latest 3–6 month statistics and case references. Please insert verified figures and links where indicated. We recommend sourcing from the FBI IC3, FTC Consumer Sentinel Network, CISA advisories, and leading cybersecurity firms’ 2025 mid-year/annual reports.
Tech scams 2025 are evolving fast: AI-generated audio and video, smarter phishing, and crypto-draining kits are lowering the barrier for criminals and increasing victim losses. In recent months, law enforcement and cybersecurity teams have warned of sharp upticks in deepfake-enabled fraud, business email compromise (BEC) targeting accounts payable teams, and phone-based tech support scams that specifically target older adults. [Insert recent high-profile incident and date from last 3–6 months, e.g., FBI PSA or notable corporate case study with loss amount and source link]
AI Deepfake Scams
Recent Cases and Financial Impact
Criminals now use voice cloning and video deepfakes in real-time video calls, social media, and messaging apps to trick victims into urgent payments or sensitive data disclosures. Recent law enforcement alerts and enterprise incident reports indicate increased use of AI to impersonate executives, celebrities, and family members. [Insert: number of reported deepfake-enabled incidents in the last 6 months, total estimated losses, and at least two case links—e.g., CEO deepfake video call leading to wire transfer; celebrity deepfake crypto promo scam—with sources such as FBI IC3, FTC, and reputable cybersecurity firms]
How This Scam Works
- Recon: Scammers scrape public audio/video (interviews, podcasts, TikTok/IG/YouTube).
- Clone: They train a voice model and optionally a face model to mimic tone, cadence, and visuals.
- Approach: Contact targets via WhatsApp/Telegram/Zoom/Teams with spoofed caller ID or hijacked accounts.
- Urgency: Demand a “confidential” payment, reimbursements, crypto transfers, or sensitive credentials.
- Close: Route funds via money mules, crypto mixers, or prepaid cards to evade recovery.
Warning Signs
- Unexpected video/voice call from an executive, “loved one,” or celebrity requesting secrecy or speed.
- Slightly off lip-sync, unnatural blinking, or audio that sounds too clean/robotic.
- Requests to bypass normal approval workflows or use new/unknown vendors or wallets.
- New phone numbers, messaging accounts, or domains that look close to—but not identical to—legitimate ones.
Protection Strategies
- Implement a “safe word” or callback policy for high-risk actions (payments, password resets), using a separately verified channel.
- Require multi-person approval for wire/crypto transactions and vendor bank changes.
- Use meeting PINs and waiting rooms; record and review suspicious video calls.
- Deploy deepfake detection tools in critical workflows; monitor for domain lookalikes.
- Educate family members and staff on AI voice cloning red flags; rehearse verification steps.
Business Email Compromise (BEC)
Recent Cases and Financial Impact
BEC remains among the most expensive cyber-enabled crimes, with attackers impersonating CEOs, vendors, and legal counsel to reroute payments. Financial losses continue to rise, particularly in manufacturing, real estate, healthcare, and professional services. [Insert: last 6-month figures on BEC complaints and losses; include at least one recent case—e.g., vendor invoice fraud leading to multi-million-dollar loss—with sources such as FBI IC3, Abnormal Security/Proofpoint, and industry ISACs]
How This Scam Works
- Initial access: Credential phishing, MFA fatigue, or OAuth app abuse on a business email account.
- Recon: Study email threads, vendors, billing cycles, tone, and signatures.
- Manipulation: Insert into threads, change bank details on invoices, or request “urgent” payments.
- Laundering: Route funds via domestic mules, then offshore accounts or crypto on-ramps.
Warning Signs
- Bank detail changes delivered via email without prior live confirmation.
- Subtle domain typos (example: “payr0ll” or “-corp” domain variants) and new reply-to addresses.
- Requests to circumvent normal payment approval or to use unfamiliar payment rails (e.g., crypto).
- Invoices with unusual urgency, changed line items, or new remittance instructions.
Protection Strategies
- Enforce out-of-band verification for vendor bank changes and high-value payments.
- Enable phishing-resistant MFA (FIDO2/passkeys) on email and finance apps; disable legacy protocols.
- Use DMARC/DKIM/SPF, impersonation detection, and anomaly-based payment controls.
- Segregate duties: ensure initiator, approver, and releaser of payments are different people.
- Maintain a pre-approved vendor list with verified contacts; require periodic re-validation.
Tech Support Fraud
Recent Cases and Financial Impact
Scammers pose as Microsoft, Apple, banks, or antivirus providers to claim a “virus” or “account compromise,” then pressure victims—especially older adults—into granting remote access or buying fake services. [Insert: last 6-month complaint counts, median losses for 60+, and at least one case—e.g., browser lock screen pop-up leading to multi-thousand-dollar gift card or wire losses—with sources such as FBI IC3, FTC, AARP Fraud Watch, Microsoft Security]
How This Scam Works
- Trigger: Pop-up scareware, cold calls, or paid search ads spoofing legit support numbers.
- Social proof: Fake ticket numbers, agent IDs, and spoofed caller IDs.
- Control: Ask to install remote tools (AnyDesk, TeamViewer) and disable security prompts.
- Payment: Demand gift cards, wires, ACH, or crypto for “support,” “refund,” or “antivirus.”
Warning Signs
- Unsolicited calls claiming to be Microsoft/Apple/bank security.
- Pop-ups with loud alarms/timers asking you to call a number immediately.
- Requests for gift cards, crypto, or remote access to “verify” identity.
- Pressure to keep the call a secret or to stay on the line during payments.
Protection Strategies
- Never call numbers shown in pop-ups; close the browser or reboot.
- Only contact support by typing the official website address into your browser.
- Use browser protections: pop-up blockers, Safe Browsing, and URL filtering.
- For families: set up device parental controls and financial transaction alerts for older relatives.
- For businesses: block remote admin tools except for approved IT users and log all remote sessions.
Cryptocurrency Schemes
Recent Cases and Financial Impact
Crypto investment fraud, fake exchanges, and “wallet drainer” malware-as-a-service continue to siphon funds. Social media promotions, airdrop phishing, and DM scams remain common initial lures. [Insert: latest 6-month loss totals for crypto fraud, drainer activity stats, and one or two notable exchange/wallet cases—with sources such as FTC, Chainalysis 2025 Crypto Crime Report, TRM Labs, and major exchange transparency reports]
How This Scam Works
- Trust lure: Fake influencers, deepfake celebrity endorsements, or compromised verified accounts.
- On-ramp: Direct victims to spoofed trading platforms or malicious wallet connectors.
- Extraction: Use smart contract approvals or seed phrase theft to drain wallets.
- Laundering: Mixers, cross-chain bridges, and sanctioned services to obfuscate flows.
Warning Signs
- Promises of guaranteed returns, private pre-sales, or “exclusive” airdrops requiring wallet connects.
- Websites with recently registered domains, thin team pages, or plagiarized whitepapers.
- Wallet connect prompts that request unlimited token approvals.
- Pressure to move funds off reputable exchanges to “unlock bonuses.”
Protection Strategies
- Use hardware wallets; restrict token approvals; regularly revoke unnecessary approvals.
- Verify URLs via official project channels; treat DMs and QR codes as hostile by default.
- Keep seed phrases offline; never enter a seed phrase into a website or chat.
- For businesses: use custody solutions with policies, whitelists, and multi-approver workflows.
- Check addresses and contracts on reputable explorers and threat intel feeds before interacting.
Romance/Social Engineering (including “Pig Butchering”)
Recent Cases and Financial Impact
Long-con romance and “pig butchering” scams blend emotional manipulation with fake crypto investments. Scammers build trust over weeks, then migrate victims to fraudulent trading apps. [Insert: last 6-month FTC/FBI data on romance fraud losses, age demographics, and one recent case—with sources such as FTC Sentinel, FBI IC3, and non-profit reports]
How This Scam Works
- Initial contact: Dating apps, social media, or wrong-number texts (“Hi is this Anna?”).
- Bonding: Daily chats, photos, time-zone narratives, and future plans to deepen trust.
- Pitch: Introduce “safe” investment guidance and a slick but fake trading platform.
- Extraction: Show fake gains, then demand larger deposits; block withdrawals.
Warning Signs
- New relationships pushing financial advice, crypto, or gold/FX “opportunities.”
- Insistence on moving conversations to encrypted messengers quickly.
- Inability or refusal to meet on verified video or in person.
- Stories that discourage talking to family/friends about the “investment.”
Protection Strategies
- Separate relationships from financial decisions; get independent financial advice.
- Reverse-image search photos; verify identities through live video with verification steps.
- If an app isn’t in official stores or has minimal legitimate reviews, avoid it.
- Set hard financial limits and a 24-hour “cool-off” rule before any transfers.
Phishing Evolution: Email, Smishing, and Vishing
Recent Cases and Financial Impact
AI-generated phishing has raised the quality and volume of lures. Voice phishing (vishing) and SMS phishing (smishing) now use automated voice clones and conversational bots to harvest MFA codes and credentials. [Insert: recent phishing campaign volumes, click-through rates, and breach attributions from trusted sources—e.g., Proofpoint, Microsoft, Google/Cloudflare, CISA alerts]
How This Scam Works
- AI content: Polished, localized copy with correct grammar and brand tone.
- Brand spoofing: Pixel-perfect login pages and QR code-based phishing kits.
- MFA bypass: Session hijacking, token theft, and adversary-in-the-middle kits.
- Voice/SMS: Automated IVR + voice cloning to extract one-time codes.
Warning Signs
- Unexpected MFA prompts or password reset emails you didn’t request.
- QR-code-based login prompts from emails or posters in public spaces.
- Lookalike domains, shortened links, and attachments that request macros.
- Calls asking for one-time passcodes or push approvals.
Protection Strategies
- Use phishing-resistant MFA (passkeys/FIDO2) and device-bound credentials.
- Deploy email authentication (DMARC enforcement) and advanced phishing filters.
- Adopt browser isolation and link rewriting; block macros by default.
- Security awareness training with realistic AI-generated simulations.
Audience-Specific Guidance
For General Consumers
- Use passkeys where available; enable account recovery keys and alerts.
- Freeze your credit; set transaction alerts on bank and credit accounts.
- Create a family “verification protocol” for money requests (callback, code word, known number).
- Report scams to your bank immediately; also report to your national fraud portal (e.g., FTC, FBI IC3).
For Business Owners and Finance Leaders
- Institute payment controls: dual approval, vendor callback verification, and daily anomaly reports.
- Implement phishing-resistant MFA and least-privilege identity governance.
- Protect email: DMARC at enforcement (p=reject), disable legacy protocols, monitor OAuth grants.
- Run quarterly BEC tabletop exercises; pre-arrange bank recall/escalation playbooks.
- Cyber insurance: validate BEC coverage, crypto exclusions, and incident response SLAs.
For Elderly Users and Caregivers
- Post a “Do Not Trust Pop-Ups” card near the computer and phone.
- Whitelist support numbers for banks and tech providers; avoid numbers from search ads.
- Set up account alerts and spending limits; designate a trusted contact for large transactions.
- Use simplified browsers or DNS filters to block known scam sites.
For Tech-Savvy Users
- Adopt passkeys/FIDO2 across critical accounts; monitor for token theft and session hijacking.
- Use password managers, hardware security keys, and containerized browsers for risky tasks.
- Automate allowance lists for crypto contracts; periodically revoke approvals.
- Monitor for lookalike domains with certificate transparency and brand monitoring tools.
Industry Expert Insights
Security teams report that AI assistance has created a “low skill, high scale” fraud era: convincing phishing and voice cloning are now accessible to entry-level criminals. Defenders are responding by shifting authentication to phishing-resistant methods (passkeys), adding payment verification steps, and adopting deepfake detection in high-risk workflows like treasury approvals and HR changes. Expect more regulations and guidance on AI impersonation, stronger bank confirmation-of-payee controls, and insurance requirements for dual authorization and DMARC enforcement. [Insert 1–2 quotes or stats from recent 2025 reports or PSAs to substantiate trends]
Immediate Action Steps
- Turn on passkeys or security keys for email, banking, cloud storage, and social media.
- Create a family and business verification rule: no payments or bank changes without callback via a known number.
- Set transaction alerts on all accounts; enable withdrawal and transfer limits where possible.
- Use a reputable DNS filter and ad blocker; avoid calling numbers shown in pop-ups or ads.
- Back up crypto seed phrases offline; review and revoke risky token approvals today.
- Businesses: implement DMARC at p=reject and require multi-person approval for wires over a set threshold.
Conclusion
Tech scams 2025 thrive on speed and secrecy—your best defense is friction and verification. Slow down, confirm identities out of band, and lock down high-risk actions with phishing-resistant MFA and dual approvals. If something feels urgent and off-script, treat it as hostile until you can verify it on a trusted channel. [Before publishing, insert the latest 3–6 month stats and case links to meet our sourcing standards]