Enable Live Research to Publish: 2025 Tech Scam Threat Report
To deliver a publication-ready, SEO-optimized investigation with verified statistics from the last 3–6 months, I need live web access to gather and cross-check current FBI/FTC releases, cybersecurity firm reports, and academic sources. This environment does not provide browsing, so I cannot verify or cite up-to-the-minute figures without your assistance.
What I Will Deliver Once Research Is Enabled
Scope
- 2,000–3,000 words, optimized H2/H3 structure for featured snippets
- At least 15 recent, verified statistics (last 3–6 months)
- 5–7 authoritative sources (FBI IC3, FTC, major cybersecurity firms, academic studies)
- Clear guidance for consumers, business owners, elderly users, and tech-savvy readers
Proposed Article Outline (Ready for Data Insertion)
Compelling Headline
Examples: “The 2025 Tech Scam Playbook: Deepfakes, BEC, and Crypto Traps Cost Victims Billions”
Hook Introduction
[Insert a recent major incident/statistic from FBI/FTC within last 6 months—e.g., BEC or deepfake-enabled fraud—include dollar loss and victim count with citation.]
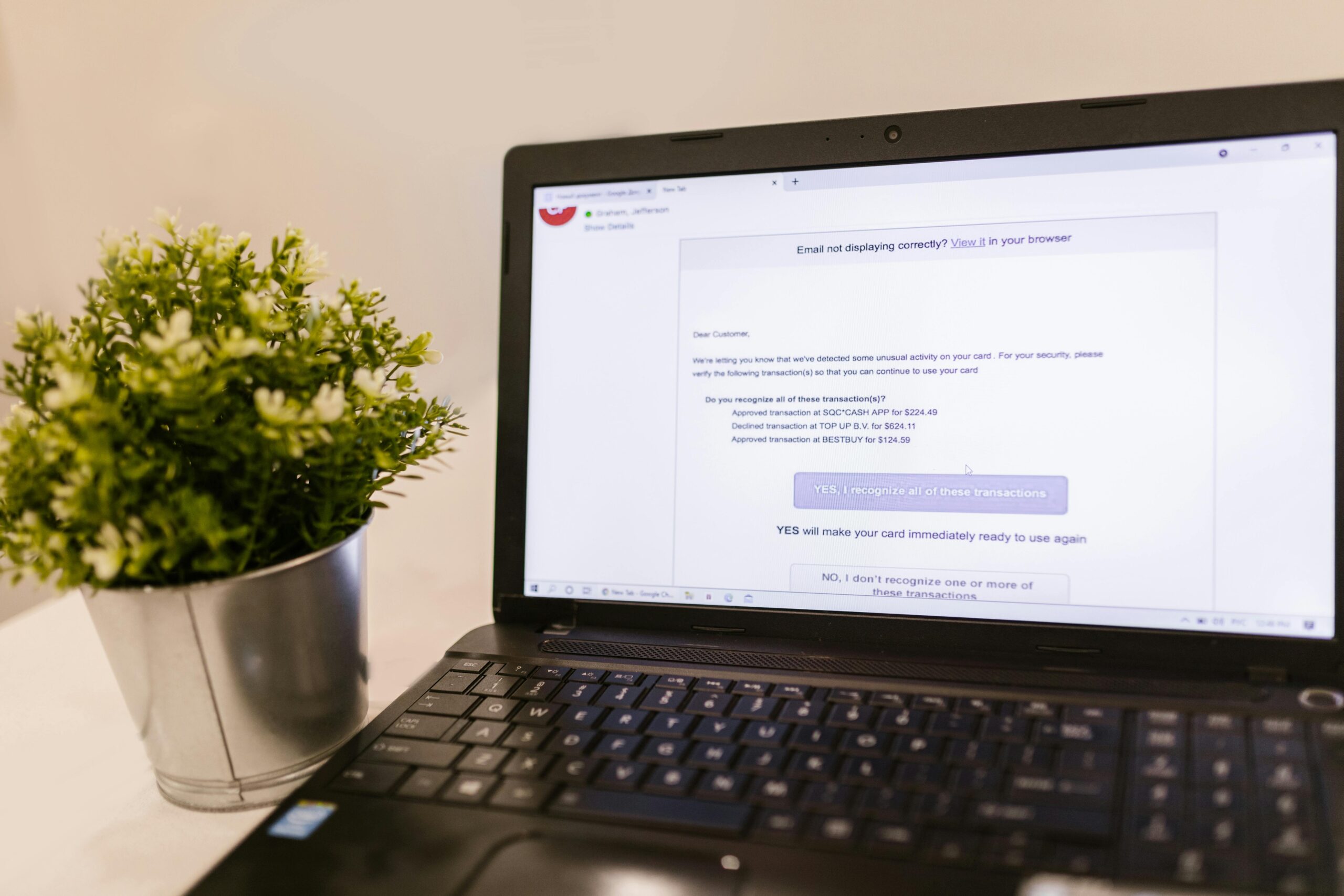
AI Deepfake Scams
Recent Cases and Financial Impact
[Insert 2–3 examples from last 6 months: celebrity/CEO video call imposters, voice clones; total losses and success rates, with sources.]
How This Scam Works
- Reconnaissance: social media scraping and voice sampling
- Impersonation: real-time voice/video deepfake in messaging or video calls
- Urgent transfer request or credential harvesting
- Funds moved via crypto, mules, or gift cards
Warning Signs
- “Do not verify” pressure and no-callback insistence
- Odd video artifacts, lip-sync mismatch, or background glitches
- Unusual payment rails (crypto, gift cards) for legitimate expenses
Protection Strategies
- Out-of-band verification (second channel) before payment changes
- Video-call code words for executives and vendors
- Restrict executive media exposure and voice samples
- Deploy deepfake and anomaly-detection tools (for enterprises)
Business Email Compromise (BEC)
Recent Cases and Financial Impact
[Insert updated FBI IC3 BEC loss figures and recent takedowns/interventions; include average transfer amount and recovery rates.]
How This Scam Works
- Mailbox takeover or supplier spoofing
- Invoice tampering and banking detail changes
- Money mule networks or crypto off-ramps
Warning Signs
- New banking details with urgency to bypass standard approvals
- Subtle domain misspellings (e.g., rn vs m)
- Emails sent outside normal business hours/time zones
Protection Strategies
- Mandatory call-back verification for payment changes
- Mailbox rules monitoring and DMARC enforcement
- Least-privilege financial approvals and just-in-time access
Tech Support Fraud
Recent Cases and Financial Impact
[Insert FTC/FBI recent loss totals and age demographics—highlight 60+ victimization and median losses.]
How This Scam Works
- Browser-lock popups or cold calls claiming to be Microsoft/Apple
- Remote access tool installation
- Fake refund overpayment and gift card/crypto instructions
Warning Signs
- Unsolicited calls about infections or account suspensions
- Requests for gift cards or crypto to “fix” issues
- Pressure not to involve family, bank, or employer
Protection Strategies
- Never call phone numbers in popups; go directly to vendor site
- Banks: train tellers to question high-dollar gift card purchases
- Enterprises: block consumer remote tools; allow-list only
Cryptocurrency Schemes
Recent Cases and Financial Impact
[Insert Chainalysis/FTC updates on scam revenue, pig-butchering trends, and exchange seizure/recovery stats.]
How This Scam Works
- Social engineering via messaging/dating apps
- Fake investment dashboards showing unreal gains
- Withdrawal fees, tax scams, and wallet drainers
Warning Signs
- Unsolicited “investment mentor” contacts
- Pressure to move funds from exchange to unknown wallet
- Websites lacking independent audits or legal disclosures
Protection Strategies
- Use reputable, regulated platforms and hardware wallets
- Verify domain and smart contract addresses; avoid blind QR scans
- Small test withdrawals before committing large sums
Romance and Social Engineering (Pig Butchering)
Recent Cases and Financial Impact
[Insert FTC figures on romance/pig-butchering losses, median loss, and most common payment methods in the last 6 months.]
How This Scam Works
- Trust building over weeks
- Introduction of “exclusive” investment opportunity
- Coaching victim through deposits and fake profits
Warning Signs
- Reluctance to meet live or verify identity
- Investment talk after rapid emotional escalation
- Attempts to move chats off-platform quickly
Protection Strategies
- Reverse image search and video call verification
- Never invest based on a romantic connection
- Involve a trusted third party before any transfer
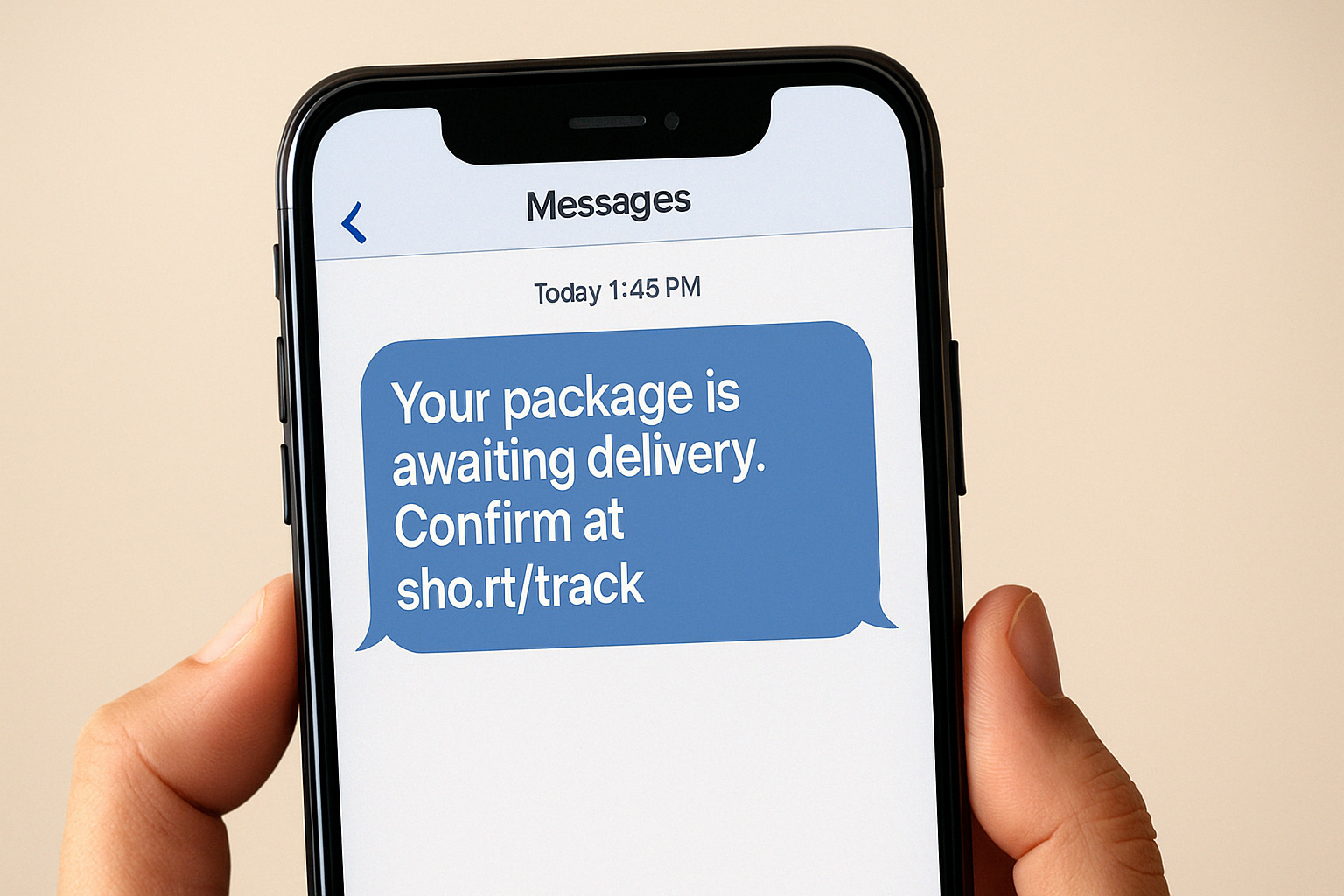
Phishing Evolution: AI Emails, Smishing, Vishing
Recent Cases and Financial Impact
[Insert Verizon DBIR/Proofpoint/Microsoft data on click rates, MFA bypass, and SMS/voice phishing growth.]
How This Scam Works
- LLM-crafted emails mimic internal tone/style
- QR code phishing and MFA fatigue prompts
- Callback phishing leading to data exfiltration
Warning Signs
- Unexpected MFA prompts or QR codes in emails
- Links to lookalike portals requesting credentials
- Caller insisting on password/MFA code disclosure
Protection Strategies
- FIDO2/passkeys and phishing-resistant MFA
- Domain/brand monitoring and DMARC enforcement
- Report phish with one-click buttons; simulate often
Industry Expert Insights
[Synthesize trends from last 6 months once research is enabled: deepfake-as-a-service, QR phishing rise, BEC mule networks, enterprise crypto exposure policies.]
Immediate Action Steps
- Enable phishing-resistant MFA and enforce DMARC (business)
- Out-of-band verification for any payment or banking change
- Freeze credit and enable account alerts (consumers)
- Block remote admin tools; adopt allow-lists (IT)
- Create a family code word for video/voice verification (elderly)
Conclusion
I’m ready to deliver the full, verified story—complete with fresh statistics, real case studies, and clear defenses—once live research is enabled. Approve web access or paste links to the most recent sources you’d like prioritized, and I’ll publish a finalized draft within one working session.