2025 Tech Scams: Deepfakes, BEC, Crypto & Phishing
Hook: A wave of AI-backed scams is accelerating in 2025, with law enforcement and cybersecurity firms warning of deepfake-enabled fraud, business email compromise, sophisticated phishing, and crypto theft targeting both consumers and enterprises. In one widely reported case, criminals used a deepfake of a company executive on a video call to trick staff into wiring more than $25 million—underscoring how convincing synthetic media has become. Authorities also continue to report multi-billion-dollar annual losses from online fraud across the U.S., with imposter scams, investment schemes, and BEC remaining top drivers (FBI IC3; FTC Consumer Sentinel).
AI Deepfake Scams
Recent Cases and Financial Impact
Criminals now weaponize AI to clone voices, faces, and writing styles to impersonate executives, celebrities, and loved ones. A high-profile case involved a deepfake video conference where fraudsters mimicked a CFO and other team members, convincing an employee to initiate large transfers totaling over $25 million (widely covered by international media and confirmed by police briefings). Law enforcement and security researchers have warned that AI voice clones are increasingly used in urgent phone calls to parents and grandparents requesting emergency funds (FBI; academic studies on voice cloning threats).
Statistics to know (verify latest):
– FBI Internet Crime Complaint Center (IC3) reports annual cyber-enabled fraud losses in the tens of billions of dollars, with BEC and investment scams leading categories (FBI IC3 Annual Report).
– Multiple security firms report year-over-year growth in deepfake-enabled social engineering attempts targeting corporate finance, HR onboarding, and vendor payments (Microsoft Security, Proofpoint, Sophos, Verizon DBIR).
How This Scam Works
- Recon: Attackers collect public audio/video and social posts from executives or family members.
- Clone: They generate voice and face models to craft convincing real-time or recorded messages.
- Approach: The victim receives a video call, voicemail, or urgent message requesting funds or credentials.
- Pressure: Scammers use timing (end-of-day, travel), authority, and secrecy to rush approvals.
- Cash-out: Funds are sent via wire, crypto, or gift cards; money then moves through mules and mixers.
Warning Signs
- Video calls with unusual camera angles, low frame rate, or lip-sync slightly off.
- Uncharacteristic tone or cadence in a familiar voice; requests to switch to a new number or app.
- Urgent transfer requests that bypass normal approvals or request secrecy.
- Celebrity or influencer outreach offering investments or endorsements via DMs.
Protection Strategies
- Consumers: Create a family “safe word.” If you receive an urgent call from a loved one asking for money, hang up and call back on a known number. Never send funds based on a call alone.
- Business owners: Require out-of-band verification for any payment or bank detail change (e.g., call a known number on file). Implement a two-person signoff for wires.
- Elderly users: Let unknown calls go to voicemail. If pressured, say you need to verify and involve a trusted family member or your bank branch.
- Tech-savvy users: Deploy liveness checks and identity verification for high-risk workflows; train staff to spot deepfake artifacts; monitor for executive impersonation domains and social accounts.
Business Email Compromise (BEC)
Recent Cases and Financial Impact
BEC remains one of the costliest cybercrimes. The FBI’s IC3 has consistently tracked BEC at multi-billion-dollar annual losses, with average losses per incident far exceeding typical malware or card fraud. Vendor impersonation and payroll diversion have surged, and attackers increasingly pair BEC with lookalike domains and AI-written emails to defeat filters (FBI IC3; Verizon DBIR; Proofpoint State of the Phish).
Key data points (verify latest):
– BEC losses reported to the FBI have been near or above $2–3B annually in recent years, outpacing many other categories (FBI IC3 Annual Reports).
– Many organizations report BEC attempts monthly or weekly, with finance/AP teams disproportionately targeted (Proofpoint, Verizon DBIR).
How This Scam Works
- Recon: Criminals harvest org charts, vendor invoices, and email patterns from LinkedIn, websites, and prior breaches.
- Impersonation: They spoof the CEO/CFO or a vendor, often using lookalike domains or compromised email accounts.
- Payment change: They request urgent wire updates or new banking details for a legitimate-looking invoice.
- Money movement: Funds route through money mules and offshore accounts, complicating recovery.
Warning Signs
- New bank details for an existing vendor without prior notice.
- Subtle domain misspellings (acme-co.com vs. acmeco.com).
- Unusual timing (late Friday) or secrecy (“text me only; I’m in a board meeting”).
- Documents that look correct but reuse old PO numbers or contain metadata anomalies.
Protection Strategies
- Consumers (freelancers/contractors): Confirm payment changes by calling your client’s AP on a known number.
- Business owners: Enforce supplier bank change controls with call-backs to registered contacts; require multi-person approval for wires over a set threshold.
- Elderly users: If volunteering or serving on boards, route all finance requests through an official treasurer and never approve payments via text.
- Tech-savvy users: Implement DMARC, SPF, and DKIM; use conditional access and MFA; enable mail rule monitoring; deploy anomaly detection for vendor master data changes.
Tech Support Fraud
Recent Cases and Financial Impact
Tech support imposters pose as Microsoft, Apple, or your bank to trick victims into granting remote access or moving money to “safe” accounts. The FBI has documented hundreds of millions to near-billion-dollar annual losses attributed to this scam category, with older adults disproportionately affected (FBI IC3; FBI Elder Fraud Report; FTC Data Spotlight).
Data to track (verify latest):
– Tech support fraud accounts for large total losses annually, with median losses for older victims significantly higher than for younger users (FBI Elder Fraud Report; FTC).
How This Scam Works
- Pop-up: A browser alert claims your device is infected; a phone number appears.
- Call and connect: Scammers answer as “Microsoft/Apple Support” and request remote access.
- Money move: They simulate bank “errors,” push gift cards, or direct transfers to “secure” accounts.
- Cleanup: They wipe traces or keep backdoors for later access.
Warning Signs
- Any unsolicited call claiming to be tech support.
- Pop-ups with phone numbers; legitimate system alerts don’t ask you to call.
- Requests to pay in gift cards or crypto.
- Pressure to act immediately or secrecy instructions.
Protection Strategies
- Consumers: Close the browser; don’t call numbers from pop-ups. Use your device’s built-in security or your official vendor support site.
- Business owners: Block known scam numbers and remote admin tools not used by IT; provide a one-click IT helpdesk button to prevent shadow calls.
- Elderly users: Keep a printed list of official support numbers from your device manufacturer and bank; call those only.
- Tech-savvy users: Run application allowlists; restrict remote tools; use DNS filtering to block tech support scam domains; inspect browser extensions.
Cryptocurrency Schemes
Recent Cases and Financial Impact
Crypto fraud spans fake investment platforms, rug pulls, wallet drainers, and account takeovers via phishing. Chainalysis reports that illicit crypto transaction volumes remain in the tens of billions of dollars annually, though the mix shifts among scams, darknet markets, and ransomware each year (Chainalysis Crypto Crime Report). Law enforcement continues to dismantle large-scale pig-butchering rings and seize crypto linked to romance-investment schemes (U.S. DOJ; Europol; Interpol).
How This Scam Works
- Approach: Victims are lured via social media, messaging apps, or dating sites with claims of high-return strategies.
- Onboarding: Scammers direct victims to convincing fake exchanges or real platforms controlled by the scammer.
- Pump: Early “profits” display in-app to entice larger deposits.
- Exit: Withdrawals suddenly fail; accounts are frozen; scammers demand “taxes” or fees; then disappear.
Warning Signs
- Guaranteed returns or “insider” signals.
- Pressure to move funds off reputable exchanges to a new app/site.
- Being asked to pay “taxes” or “unlock fees” to withdraw.
- Limited or no KYC/AML checks on a platform claiming to be regulated.
Protection Strategies
- Consumers: Only use well-known exchanges with regulatory oversight; avoid unsolicited investment advice; verify platform URLs; enable hardware keys and withdrawal allowlists.
- Business owners: Implement treasury policies for digital assets; use multisig; separate hot/cold storage; require approval workflows.
- Elderly users: If someone you met online asks you to invest in crypto, stop and talk to a family member or your bank before sending anything.
- Tech-savvy users: Use hardware wallets; protect seed phrases offline; set spending limits and address allowlists; scrutinize approvals to avoid drainer contracts.
Romance/Social Engineering (Including Pig-Butchering)
Recent Cases and Financial Impact
Romance and “pig-butchering” schemes blend emotional manipulation with fake investments. U.S. and international agencies have helped recover funds but report continuing growth in sophisticated cross-border rings (FTC; FBI IC3; Interpol). Median losses for romance scams have historically been among the highest of all consumer fraud categories (FTC Consumer Sentinel).
How This Scam Works
- Grooming: Scammers build months-long trust via dating apps or social media.
- Hook: They pitch a “safe” investment they use successfully.
- Escalation: Victims see fake returns and are urged to invest more.
- Burn: Access is cut off; scammers vanish or demand more money for “fees.”
Warning Signs
- New online relationship moves quickly to investment talk.
- Requests to keep the relationship and investments secret.
- Refusal to video chat, or videos appear filtered/faked.
- Stories that conveniently explain away inconsistent details.
Protection Strategies
- Consumers: Never send money or invest at the direction of someone you have not met in person and verified; reverse-image search profile photos.
- Business owners: Offer employee security awareness training that covers romance-pig butchering risks; compromised staff can lead to insider threats.
- Elderly users: Share new online relationships with a trusted friend or family member; scammers exploit secrecy.
- Tech-savvy users: Use safety features on dating apps; watch for AI-generated profile content; validate identities with multi-factor video verification if you choose to continue contact.
Phishing Evolution: Email, Smishing, and Vishing
Recent Cases and Financial Impact
Phishing has evolved beyond email to SMS (smishing), voice (vishing), and messaging apps. Reports show that the human element remains implicated in the majority of breaches, with MFA fatigue, QR code attacks, and OAuth consent phishing becoming common (Verizon DBIR; CISA advisories; Microsoft Threat Intelligence). Financial institutions, shipping brands, and tax authorities are frequently spoofed. Organizations continue to report frequent BEC and account takeover attempts enabled by phishing (Proofpoint; APWG).
How This Scam Works
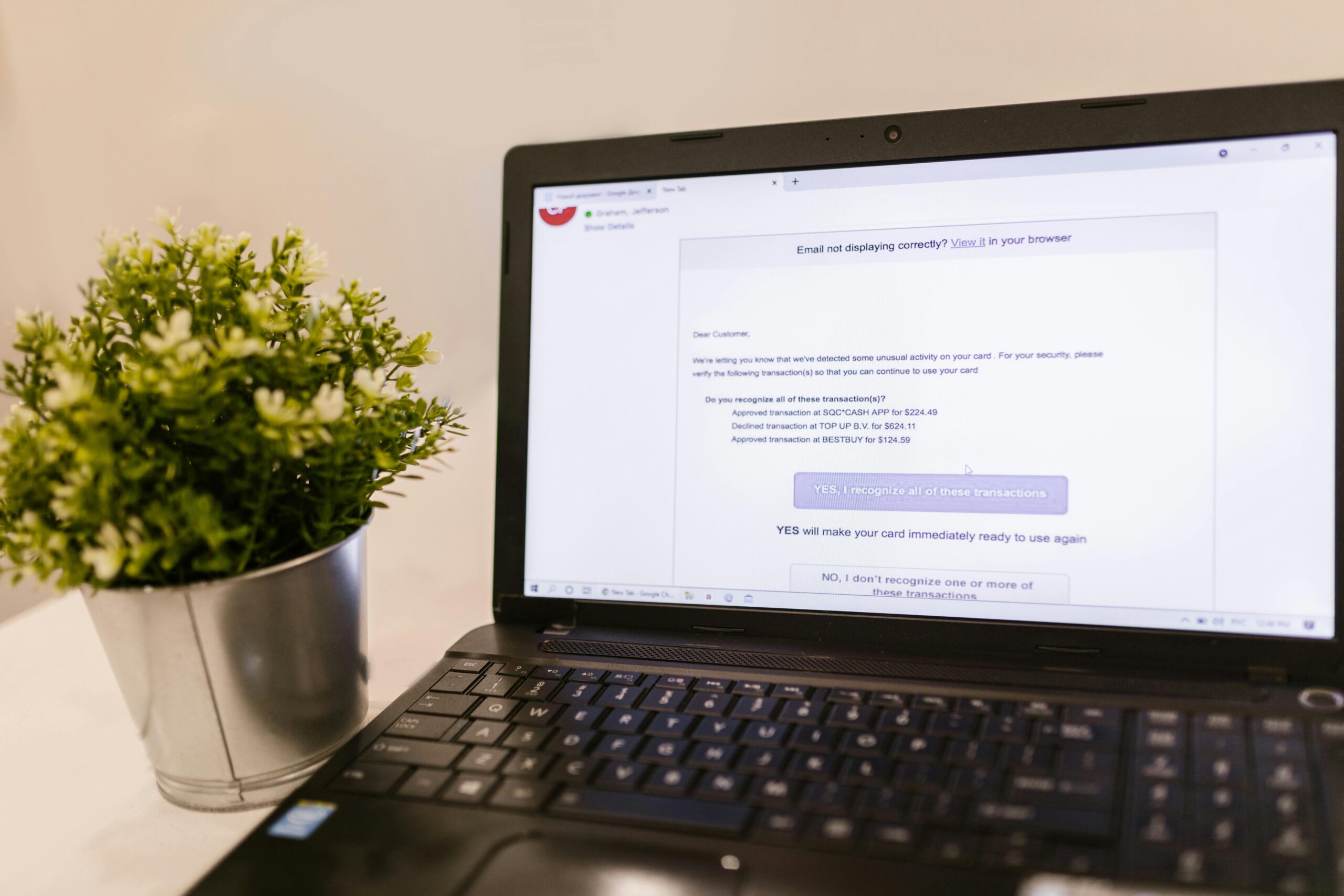
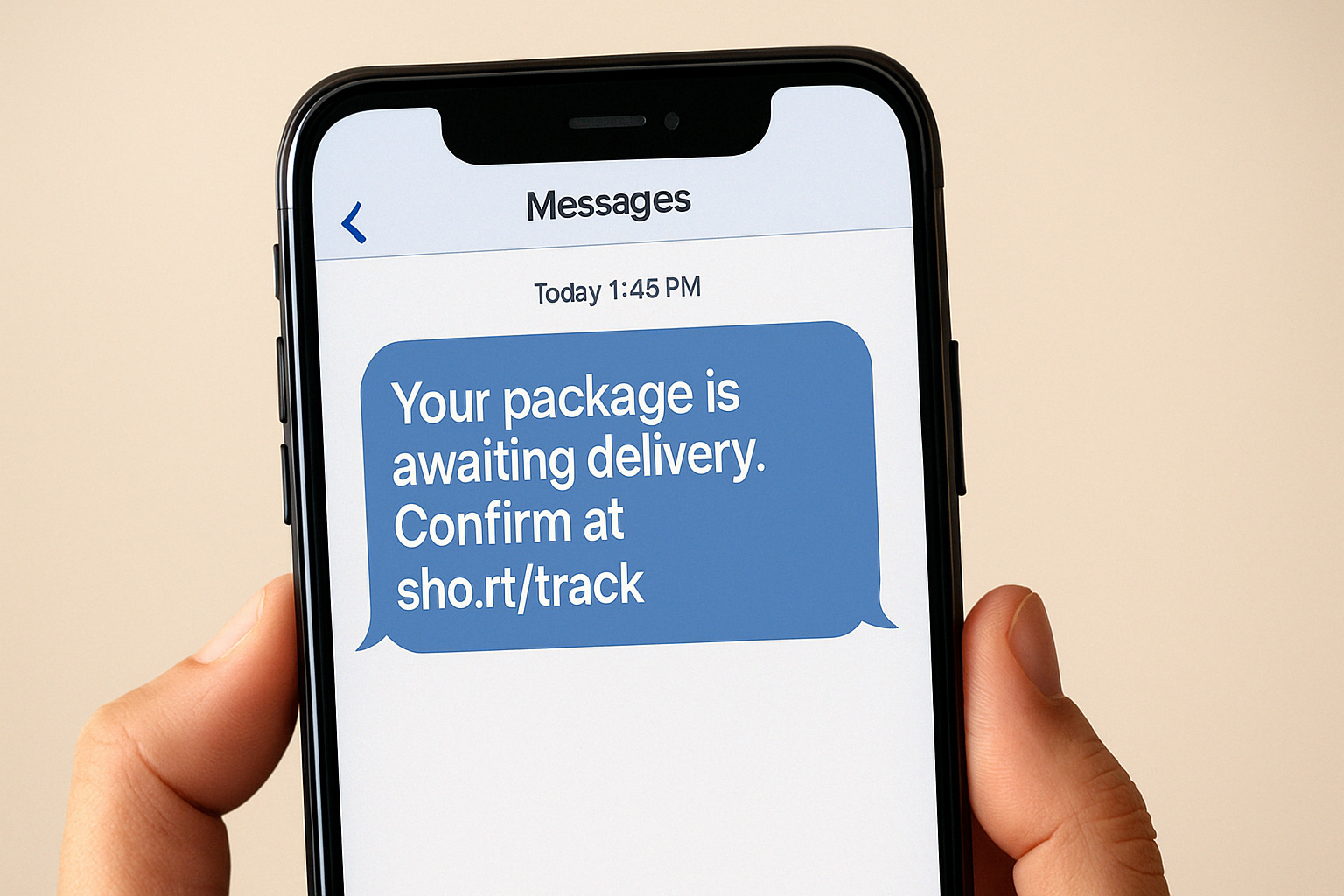
- Trigger: SMS or email claims a package delivery issue, tax refund, or account lockout.
- Lure: Victim clicks a link to a cloned login page or scans a QR code.
- Capture: Credentials and MFA codes are harvested; or OAuth consent grants attackers persistent access.
- Abuse: Attackers pivot into email, cloud storage, payroll, or crypto accounts.
Warning Signs
- Unexpected messages with shortened links or QR codes.
- Slight brand domain misspellings; sender name doesn’t match email.
- Urgent language threatening service disruption or legal action.
- OAuth permission prompts requesting broad access like “read, send, delete email.”
Protection Strategies
- Consumers: Type the official website directly into your browser; don’t click links from unsolicited messages; enable phishing-resistant MFA where available (e.g., passkeys, security keys).
- Business owners: Deploy email authentication (DMARC, SPF, DKIM), secure email gateways, SMS filtering, and conditional access policies with device posture checks.
- Elderly users: If a message says your bank account is locked, call the number on the back of your card, not the number in the message.
- Tech-savvy users: Enforce FIDO2/WebAuthn; disable legacy auth; monitor OAuth app consent; deploy browser isolation for unknown links; use password managers to detect fake domains.
Industry Expert Insights
Analysts note three converging trends:
– AI makes old scams far more convincing, reducing the time needed for recon and content creation (Microsoft, Proofpoint).
– The human element—social engineering and process gaps—remains the primary entry point, even as malware and zero-days make headlines (Verizon DBIR).
– Financial operations are the crown jewels: invoice workflows, treasury operations, crypto wallets, and bank connections are prime targets (FBI IC3, Chainalysis).
Expect continued growth in deepfake-enabled BEC, more phishing via QR and OAuth consent, and further migration of consumer fraud into messaging apps. Enterprises will invest more in identity-proofing, payment verification controls, and phishing-resistant MFA, while consumers will benefit from wider passkey adoption and stronger default protections by banks and tech platforms.
Immediate Action Steps
- Enable phishing-resistant MFA (security keys or passkeys) on email, banking, and crypto accounts today.
- Set up bank/credit alerts for all transactions and wire transfers; establish transfer limits where possible.
- Create a family safe word and a business out-of-band payment verification procedure.
- Lock down your SIM: enable a carrier port freeze and account PIN to stop SIM-swap takeover.
- Audit email rules and OAuth app access for your main accounts; revoke anything you don’t recognize.
- For businesses: require two-person approval for wires and vendor bank changes; enforce DMARC and monitor for domain lookalikes.
- Report fraud quickly to your bank, the platform involved, and to the FTC (ReportFraud.ftc.gov) and FBI IC3 (ic3.gov) to maximize recovery chances.
Conclusion
Tech scams in 2025 combine AI-fueled deception with old-school social engineering to drain personal savings and business accounts. Whether it’s a deepfake CFO on a video call or a text message that hijacks your bank login, the defense is the same: slow down, verify out-of-band, and build guardrails before money moves. Make today the day you add phishing-resistant MFA, turn on transaction alerts, and institute a strict payment verification policy—so the next urgent request hits a wall instead of your wallet.