Tech Scams 2025: How Deepfakes, BEC, and Crypto Grifts Are Draining Wallets—and How to Fight Back
Hook: Americans reported a record $10 billion in fraud losses in 2023, according to the FTC—driven by email scams, fake tech support, and fast-evolving schemes that abuse AI and cryptocurrency. The FBI’s 2023 IC3 report likewise logged 880,418 complaints and $12.5 billion in adjusted losses, underscoring a clear trend: online fraud is organized, professional, and increasingly AI-assisted. While 2025 brings new tools for defense, scammers are adapting just as quickly.
Note: The statistics cited reflect the latest publicly available figures from authoritative sources as of late 2024 (e.g., FBI IC3 2023, FTC 2023). We recommend updating with 2024–2025 report snapshots as they are released.
AI Deepfake Scams
Recent Cases and Financial Impact
Deepfake-enabled fraud surged as criminals used synthetic voices and fabricated video calls to impersonate executives, celebrities, and relatives. Law enforcement and cybersecurity advisories in 2023–2024 warned organizations that deepfakes were being used to socially engineer high-value transfers and extort payments.
- FBI and CISA have cautioned that deepfake tools are increasingly used in social engineering and disinformation, complicating traditional verification methods (CISA/FBI advisories; see sources).
- The Verizon 2024 Data Breach Investigations Report (DBIR) highlights the enduring human element in breaches—68% involve a non-malicious human action—making deepfake social engineering a potent threat amplifier.
How This Scam Works
- Threat actors harvest audio/video from public content to train voice cloning or face-swapping tools.
- They stage urgent calls (e.g., “CEO” on a video meeting) to push a confidential transfer or credential handoff.
- They add realism with spoofed caller IDs, forged emails, or leaked internal jargon.
- Funds are routed to money mules or converted to crypto for rapid laundering.
Warning Signs
- “Executive” refuses camera movement, shows distorted eye/mouth sync, or avoids multi-person verification.
- Unusual after-hours urgency to bypass normal payment controls.
- Requests to move to encrypted consumer apps or personal email.
- Inconsistent audio artifacts or latency during calls.
Protection Strategies
- All audiences: Establish safe words or callback protocols for any high-risk request, regardless of who appears on camera.
- Business owners: Require out-of-band verification for all wire requests over a set threshold; mandate dual approval and verified vendor bank changes.
- Elderly users: If a “grandchild” calls for urgent money, hang up and call a known number. Never pay via gift cards or crypto ATMs.
- Tech-savvy users: Validate media authenticity via reverse image/video searches and check for inconsistent lighting, reflections, and artifacting.
Business Email Compromise (BEC)
Recent Cases and Financial Impact
BEC—also called CEO fraud or vendor impersonation—remains the costliest email-based crime.
- The FBI IC3 reported $2.9 billion in adjusted BEC losses in 2023, again among the highest-loss categories.
- DBIR 2024 highlights that credential theft and pretexting continue to fuel email-driven intrusions, with the majority of breaches involving human factors (68%).
How This Scam Works
- Criminals phish executives or vendors, or use lookalike domains and thread-hijacking.
- They insert themselves into invoice conversations, swap banking details, and divert payments.
- Funds are moved through domestic accounts to overseas networks within hours.
Warning Signs
- Slight misspellings in sender domains (e.g., using rn for m) or newly registered supplier domains.
- Last-minute changes to payment instructions or bank locations.
- Pressure to keep the request confidential.
Protection Strategies
- All audiences: Confirm any banking-change request with a known phone number. Never trust contact info in the request itself.
- Business owners: Enforce a Business Email Compromise prevention checklist: DMARC enforcement, MFA on email, least-privilege finance access, dual control, payee allowlists, and bank-positive pay.
- Tech-savvy users: Deploy secure email gateways with anomaly detection, account takeover protection, and banner warnings for external senders.
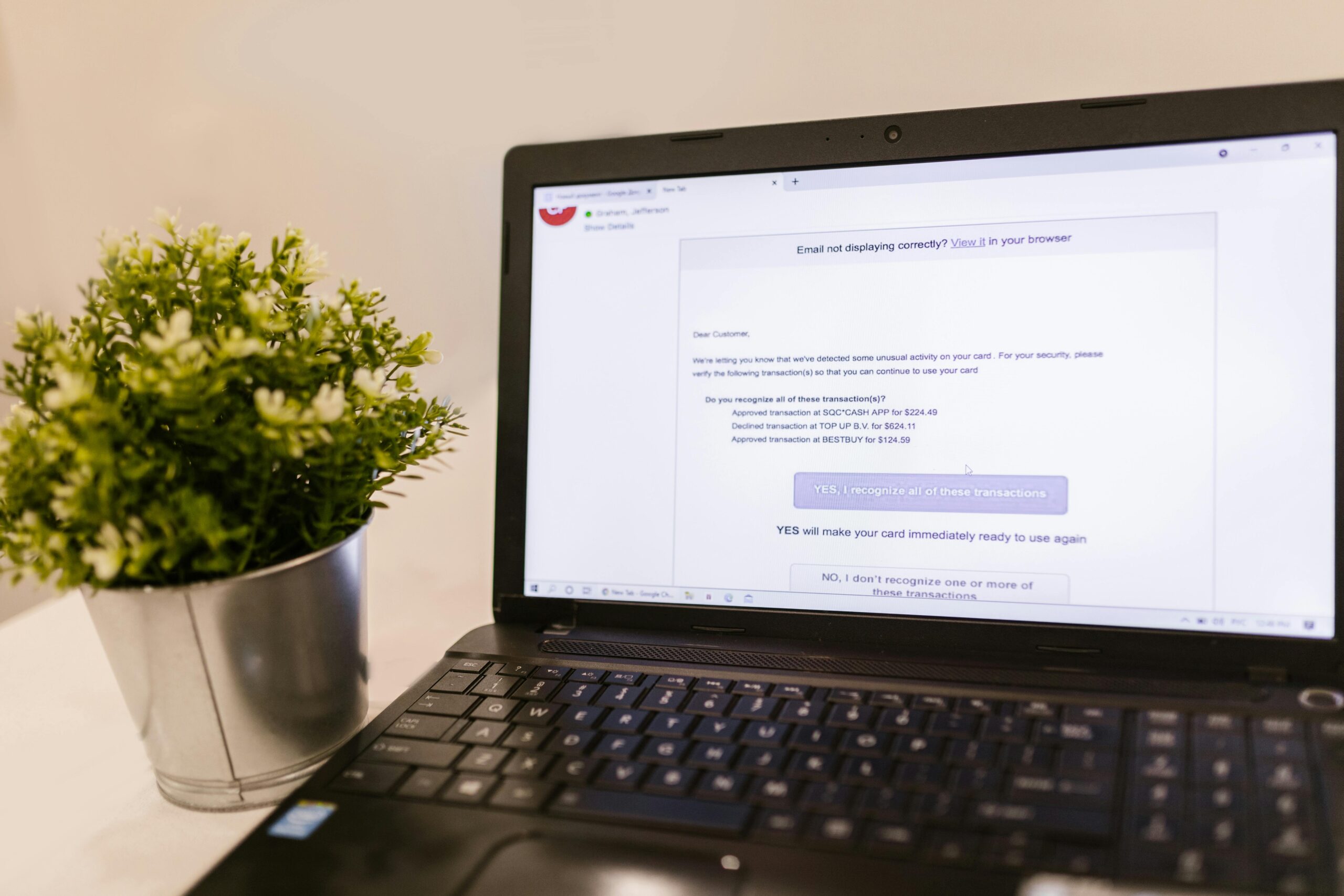
Tech Support Fraud
Recent Cases and Financial Impact
- FBI IC3 2023: Tech support fraud losses exceeded $1.3 billion, with older adults disproportionately affected.
- FBI elder fraud reporting noted over-60 victims suffered more than $3.4 billion in total losses in 2023 across scam types, with high average losses (~$33,000).
How This Scam Works
- A pop-up claims your computer is infected; a “Microsoft/Apple” agent calls or chats.
- They guide you to install remote-access tools, then stage a fake refund or find “problems.”
- They demand payment via gift cards, wire, or crypto; sometimes they move your money while on the machine.
Warning Signs
- Unsolicited calls about computer problems—real companies do not cold-call.
- Pop-ups with phone numbers, countdown timers, or audio alarms.
- Payment requests via gift cards or crypto ATMs.
Protection Strategies
- General consumers: Close the browser tab; don’t call numbers in pop-ups. Use a trusted local technician if needed.
- Elderly users: Put a “Do Not Pay” note by the phone: no gift cards, no crypto, no PINs—call family first.
- Business owners: Block remote admin tools by default, allow only approved tools, and log/alert on remote sessions.
Cryptocurrency Schemes
Recent Cases and Financial Impact
- The FBI IC3 2023 found Investment fraud at $4.57 billion, a large share of which involved crypto-based “pig butchering” and fake platforms.
- FTC has repeatedly warned about crypto ATM payment requests and “guaranteed” high-return pitches as hallmarks of fraud.
How This Scam Works
- Scammers build trust over weeks (often on messaging apps) and direct victims to slick but fake trading dashboards.
- Accounts appear to “grow,” but withdrawals are blocked until additional fees are paid—then the site vanishes.
- Drainer malware and QR address swaps silently siphon funds from hot wallets.
Warning Signs
- “No risk, guaranteed 20–40% weekly returns.”
- Pressure to move to off-platform messaging and keep the “opportunity” secret.
- Withdrawal delays with new “taxes” or “verification fees.”
Protection Strategies
- All audiences: Treat unsolicited investment pitches as scams. Verify platforms against official registries; avoid crypto ATM instructions.
- Tech-savvy users: Use hardware wallets, approve-list addresses, and separate “hot” and “cold” funds. Verify URLs and contracts; revoke dApp approvals regularly.
- Business owners: Implement treasury policies for crypto holdings: multi-sig, policy-based approvals, and segregation of duties.
Romance and Social Engineering (“Pig Butchering”)
Recent Cases and Financial Impact
- FTC 2023 data showed romance and imposter scams among top loss categories, with aggregate consumer fraud losses reaching $10 billion in 2023.
- FBI reports highlight large individual losses from “long-con” romance-investment hybrids.
How This Scam Works
- A scammer builds rapport on dating or social apps, then pivots to a “can’t-miss” investment (often crypto).
- They coach the victim through deposits on a fake platform and show fabricated gains to encourage bigger transfers.
- When the victim tries to withdraw, the scammer invents fees or blocks access.
Warning Signs
- Reluctance to meet on video or in person; stock photos or recently created profiles.
- Rapid escalation to money talk, secrecy, or isolating the victim from friends/family.
- Emotional manipulation tied to urgent financial requests.
Protection Strategies
- General consumers: Do not send money or crypto to someone you haven’t met; verify identities with live, casual video and real-life details.
- Elderly users: Involve a trusted friend/family member if an online relationship asks for money or investments.
- Business owners: Offer employee awareness training—romance-investment scams often lead to payroll diversion and account misuse at work.
Phishing Evolution: AI-Generated Emails, Smishing, and Vishing
Recent Cases and Financial Impact
- FBI IC3 2023 recorded phishing as the most-reported complaint type, with approximately 298,000+ complaints.
- Verizon DBIR 2024: 68% of breaches involve human factors—phishing, pretexting, and credential misuse remain dominant entry points.
How This Scam Works
- AI enables grammatically clean, personalized phishing at scale; SMS and voice spoofing reach users off-email.
- URL shorteners, QR codes, and web impersonation bypass old filters.
- Credential harvesting leads to session hijacking and account takeover.
Warning Signs
- Unexpected password reset or MFA requests.
- Unfamiliar domains behind shortened links; mismatched sender display name and address.
- QR codes in emails asking for login or payment.
Protection Strategies
- All audiences: Type known URLs directly; don’t scan QR codes in unsolicited messages; use a password manager to auto-fill only at legitimate domains.
- Business owners: Enforce phishing-resistant MFA (FIDO2 security keys) and conditional access; roll out DMARC at enforcement (p=reject).
- Tech-savvy users: Check DKIM/SPF/DMARC headers when in doubt; run links in isolated browsers or sandboxes.
Industry Expert Insights
Across authoritative sources, several themes stand out:
- The human is the battleground. Verizon’s 2024 DBIR attributes 68% of breaches to human factors, mirroring FBI/FTC observations that social engineering drives the largest losses.
- Losses are consolidating into fewer, higher-impact categories. FBI IC3 2023 shows outsized losses in BEC ($2.9B) and investment fraud ($4.57B).
- Elderly users face severe loss per incident. FBI elder fraud reporting cites $3.4B+ in 2023 losses with average losses in the five figures, demanding tailored education and controls.
- AI scales persuasion. Proofpoint and other security firms note higher-quality lures and thread-hijacking; defenders must adopt phishing-resistant MFA, strong email authentication (DMARC at p=reject), and automated detection tuned for language and sender anomalies.
Immediate Action Steps
- Enable phishing-resistant MFA (security keys) on email, banking, crypto, and payroll services today.
- Lock down email: implement SPF, DKIM, and DMARC at enforcement; add external sender banners; disable legacy protocols (POP/IMAP) and enforce conditional access.
- Adopt a wire transfer playbook: 2-person approval, out-of-band callbacks using verified numbers, and vendor bank-change verification through a known channel.
- Freeze credit and enable bank alerts for transactions, new payees, and large transfers. Use account activity alerts for crypto exchanges.
- Harden devices: auto-updates, application allowlists, disable unneeded remote tools, browser isolation for risky clicks.
- Family plan for elders: a written “do-not-pay” rule (no gift cards/crypto/wires), a trusted-contact phone tree, and in-branch verification for any large transaction.
- Incident readiness: post a recovery checklist on the wall—contact bank fraud desk, recall wires, freeze accounts, revoke tokens, rotate credentials, and file reports with IC3/FTC.
Conclusion
From deepfake video calls to polished BEC pretexts and crypto “investments,” today’s scams are engineered to bypass judgment, not firewalls. The good news: a short list of disciplined habits—phishing-resistant MFA, verified callbacks, DMARC enforcement, and strict payment controls—neutralizes the majority of high-impact fraud. Share this guide with your team and family, implement the checklists this week, and turn today’s most common attacks into near-misses instead of losses.