2025 Guide to Tech Scams: Deepfakes, BEC, Crypto — What to Know Now
Scammers are moving faster than ever — and the money at stake is staggering. The FTC says consumers reported losing over $10 billion to scams in 2023, a 14% jump year-over-year, across 2.6 million reports (FTC). The FBI’s IC3 tallied $12.5 billion in reported cyber-enabled losses in 2023 alone (FBI IC3 2023). In one of the most jaw-dropping recent cases, a multinational firm in Hong Kong was duped out of roughly $25.6 million after criminals used deepfake video to impersonate executives on a live call (BBC).
AI Deepfake Scams (Celebrity Impersonation, Fake Video Calls)
Recent Cases and Financial Impact
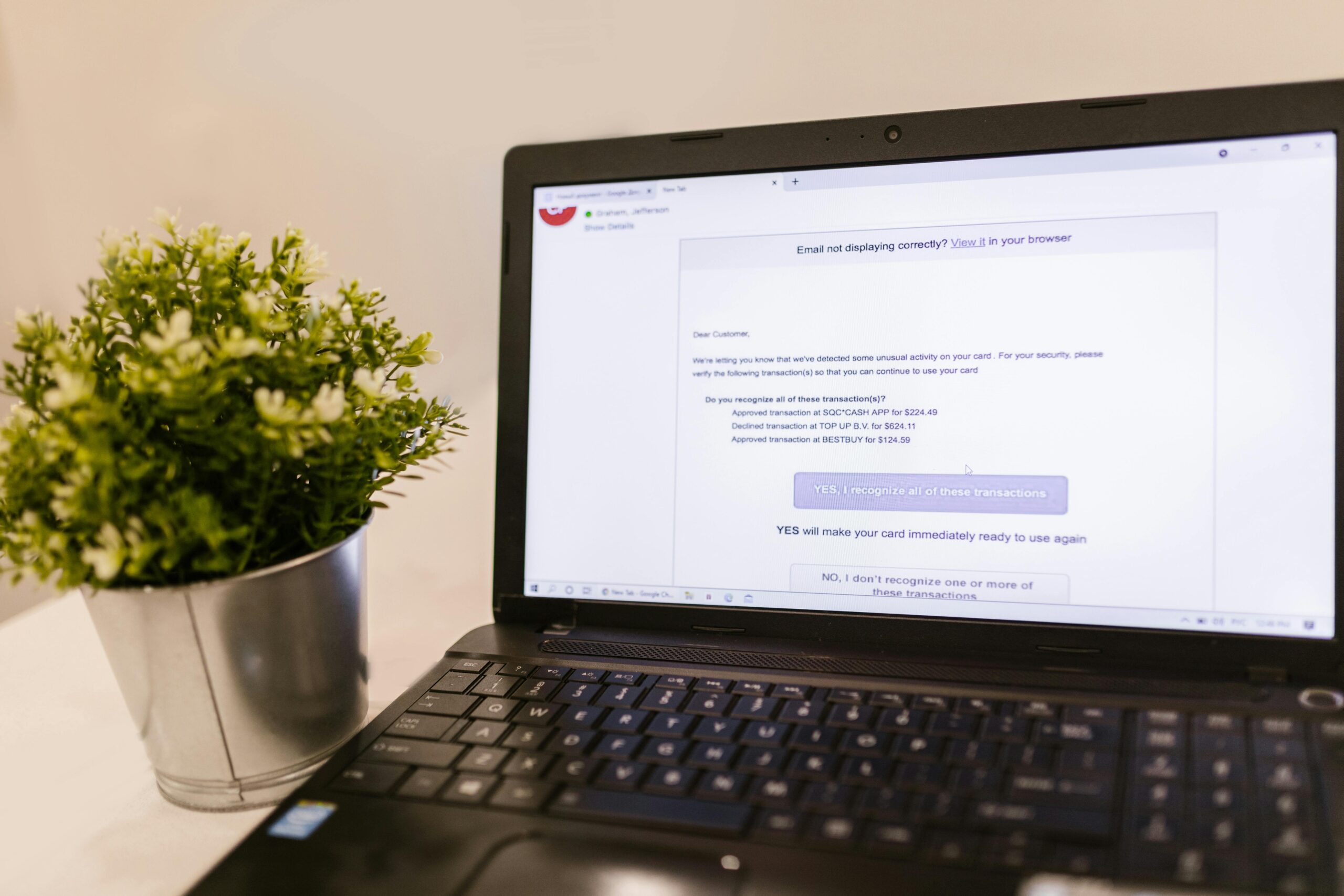
Deepfakes have shifted from novelty to weapon. In the Hong Kong case (Feb 2024), attackers allegedly recreated a CFO and colleagues on a video call to push an employee into authorizing transfers totaling about $25.6 million (BBC). While official accounting for deepfake-specific losses is still emerging, broader indicators underscore the risk:
- Human-driven tactics remain central: 68% of breaches involve a human element such as social engineering (Verizon DBIR 2024).
- Business Email Compromise (BEC), often paired with voice/video impersonation, cost victims about $2.9 billion in 2023 (FBI IC3 2023).
How This Scam Works
- Recon: Criminals scrape public profiles, earnings calls, and prior interviews to collect voice, video, and background details.
- Clone: AI tools synthesize a convincing voice clone or video deepfake of a known figure (CEO, CFO, celebrity).
- Set the stage: An urgent pretext (e.g., confidential deal, audit, regulatory issue) justifies secrecy and speed.
- Execution: A live video call or voice note instructs wire transfers, gift card purchases, or crypto payments.
- Cover tracks: Funds move through money mules, exchanges, or mixers.
Warning Signs
- Voice or video calls that forbid callbacks or verification via official channels.
- Slight lip-sync delays, unnatural blinking, odd camera angles, or overly polished backgrounds.
- Urgent financial requests that bypass normal approval workflows.
- New or changed payment instructions, especially for high-value or international wires.
Protection Strategies
- Out-of-band verification: Require a second channel (e.g., verified phone number or secure chat) for any payment approval over a set threshold.
- Deepfake drills: Train staff to pause and verify when a senior leader appears on an unexpected, urgent call.
- Video-call passwords and waiting rooms: Limit who can join; use watermarked virtual backgrounds for execs to reduce spoofing.
- Payment controls: Dual approval, callback to verified vendor numbers, and a no-exceptions rule for “urgent” transfers.
Business Email Compromise (CEO Fraud, Vendor Impersonation)
Recent Cases and Financial Impact
BEC remains one of the costliest scams targeting organizations of all sizes. In 2023, BEC losses reported to the FBI totaled about $2.9 billion, more than any other single category except investment fraud (FBI IC3 2023). The Verizon DBIR 2024 notes the median BEC transaction sits around $50,000, highlighting how even a single successful email thread hijack can be devastating.
How This Scam Works
- Thread hijacking: Attackers gain mailbox access (often via phishing) and reply directly within real vendor threads.
- Invoice manipulation: They insert new bank details or create lookalike domains (ex: examp1e.com) to redirect payment.
- Pressure tactics: “We’ll miss the shipment cutoff” or “This closes our quarter” to push same-day wires.
- Mule networks: Funds are laundered through multiple accounts domestically and abroad.
Warning Signs
- Payment detail changes by email without a signed amendment and verification call to a known, verified number.
- New beneficiary accounts in high-risk jurisdictions.
- Mismatched display names vs. full email addresses; subtle domain misspellings.
- Unusual tone or grammar from a known contact or vendor.
Protection Strategies
- Mandatory call-back verification using previously verified phone numbers for any change to banking instructions (CISA BEC Guidance).
- Enforce MFA for email and financial systems; adopt phishing-resistant MFA where possible (FIDO/WebAuthn).
- Disable legacy mail protocols, enable conditional access, and monitor impossible-travel logins.
- AP aging and payment holds: Hold first-time vendor payments for 24 hours to allow internal review.
- Bank recall playbook: Keep rapid wire-recall procedures and law enforcement contacts on file.
Tech Support Fraud (Fake Microsoft/Apple Calls, Remote Access)
Recent Cases and Financial Impact
Criminals pose as trusted tech brands to gain remote access and drain accounts. The FBI reported tech support fraud losses exceeding $1 billion in 2023, with older adults disproportionately impacted (FBI PSA 2024). Overall, people 60+ reported nearly $3.4 billion in losses to online crimes in 2023 (FBI Elder Fraud 2023).
How This Scam Works
- Trigger: Pop-up warnings or unsolicited calls claim your device is infected or your bank account is compromised.
- Remote access: Scammers push victims to install tools like AnyDesk or RemotePC.
- Confidence tricks: They “show” fake errors, then request payment or guide “safe” transfers that actually route to criminals.
- Cleanup: Attackers remove traces, sometimes leaving malware for repeat hits.
Warning Signs
- Unsolicited calls or browser pop-ups demanding immediate action or payment.
- Pressure to install remote-access software or share one-time codes.
- Requests to buy gift cards or convert funds to crypto “for safekeeping.”
Protection Strategies
- Never call the number in a pop-up. Close the browser, reboot, and contact the company via its official site (FTC).
- Bank verification: If told your funds are at risk, call your bank using the number on your card.
- Device hygiene: Keep OS/browser updated, block pop-ups, and run reputable security software.
- For families: Add a “call me first” rule so older relatives verify any tech support request.
Cryptocurrency Schemes (Fake Investment Platforms, Wallet Drainers)
Recent Cases and Financial Impact
Investment fraud was the top loss category to the FBI in 2023 at roughly $4.57 billion, with crypto-investment scams estimated around $3.94 billion (FBI IC3 2023). Ransomware extortion, a related crypto-enabled crime, rebounded to over $1 billion in 2023 after a dip the prior year (Chainalysis 2024).
How This Scam Works
- Pig butchering: Long-term grooming on social or dating apps leads victims to deposit funds into fake investment portals.
- Approval phishing: Wallet “allow” prompts grant drainer contracts permission to move assets.
- Giveaways and airdrops: Fake promotions request seed phrases or drive users to malicious dApps.
Warning Signs
- Guaranteed “no risk” returns or earnings screenshots that look too perfect.
- Pressure to keep the investment “secret.”
- Web3 transaction prompts asking for unlimited spend approvals or seed phrase entry.
Protection Strategies
- Verify platforms: Check registration, domain age, and independent reviews; avoid links sent via DM.
- Cold wallets and permissions: Use hardware wallets; regularly revoke unnecessary token approvals.
- Test withdrawals: On any new platform, start with a tiny deposit and confirm you can withdraw before adding more.
- Never share seed phrases. No legitimate support agent will ask for them.
Romance/Social Engineering (Dating App Fraud, Pig Butchering)
Recent Cases and Financial Impact
Social engineering fuels multiple high-loss categories. The FTC reports imposter scams — often blending romance, business, and government impersonation — drove about $2.7 billion in reported losses in 2023, the top fraud category by count (FTC). Older adults continue to be heavily targeted across romance and investment hybrids, contributing to nearly $3.4 billion in losses for those aged 60+ (FBI Elder Fraud 2023).
How This Scam Works
- Relationship building: Scammers befriend on dating apps or social media, shifting to private chat.
- Trust and isolation: They discourage victims from discussing the “opportunity” with friends/family.
- Escalation: The story pivots to urgent needs (medical bills, customs, investment) and requests for money or crypto.
- Exit: Accounts vanish once large sums are sent; victims are re-contacted later with a “recovery” scam.
Warning Signs
- Rapid professions of love or moving the relationship off-platform immediately.
- Refusal to video chat, or highly constrained call times with bad camera angles.
- Requests for money, gift cards, or crypto — especially if it must remain a “secret.”
Protection Strategies
- Reverse image search profile photos. Look for multiple, inconsistent identities.
- Never send money to someone you haven’t met in person and verified.
- Set a personal rule: discuss large financial decisions with a trusted friend first.
- Use in-app reporting tools; if you’ve paid, contact your bank immediately and file with the FTC and FBI IC3.
Phishing Evolution (AI-Generated Emails, Smishing, Vishing)
Recent Cases and Financial Impact
Phishing remains a gateway to nearly every other scam. The Verizon DBIR 2024 finds phishing is present in a large share of breaches, while use of stolen credentials appears in about 31% of breaches and the human element is a factor in 68%. The median BEC incident value around $50,000 underscores how convincing messages can rapidly turn into significant financial impact (DBIR 2024).
How This Scam Works
- Email: AI-personalized messages spoof bosses or vendors; links lead to credential harvesters.
- Smishing: SMS messages emulate delivery services or banks to elicit logins or one-time codes.
- Vishing: Phone calls pressure targets to share MFA codes or install remote tools.
Warning Signs
- Lookalike domains, mismatched sender names, and shortened links.
- Unusual requests for MFA codes or “urgent security verification.”
- Invoices or pay updates sent outside normal cycles.
Protection Strategies
- Phishing-resistant MFA (FIDO/WebAuthn) wherever possible; avoid SMS-only authentication (Microsoft).
- Use password managers to auto-detect fake domains.
- Email authentication: Enforce SPF, DKIM, DMARC with reject policies; monitor brand impersonation.
- Report buttons: One-click reporting in email clients to speed analysis and takedown.
Statistics You Can Use (Verified)
- Consumers reported losing over $10 billion to fraud in 2023; 2.6 million reports in total (FTC).
- Imposter scams drove about $2.7 billion in reported losses in 2023 (FTC).
- Median loss across fraud reports was roughly $500 in 2023 (FTC).
- FBI IC3 logged 880,418 complaints and $12.5 billion in reported losses in 2023 (FBI).
- Investment fraud losses reached about $4.57 billion in 2023; crypto investment fraud about $3.94 billion (FBI).
- BEC reported losses were about $2.9 billion in 2023 (FBI).
- Tech support fraud losses exceeded $1 billion in 2023 (FBI).
- Adults 60+ reported nearly $3.4 billion in losses in 2023 (FBI).
- Deepfake-enabled video call scam in Hong Kong netted about $25.6 million for criminals (Feb 2024) (BBC).
- 68% of breaches involved a human element in 2024 DBIR analysis (Verizon).
- Phishing featured in a significant share of breaches; stolen credentials in about 31% (Verizon).
- Median BEC transaction value was around $50,000 (Verizon).
- Ransomware revenue surpassed $1 billion in 2023 (Chainalysis).
Audience-Specific Guidance
For General Consumers
- Pause-Verify-Pay: For any unexpected money request, pause. Verify via a known-good phone number or website. Only then pay.
- Use phishing-resistant MFA on email, banking, and cloud storage; avoid SMS-only 2FA.
- Bank alerts: Turn on text/app alerts for logins and transactions over your chosen threshold.
- Report and recover: If you paid, call your bank immediately, file with the FTC and FBI IC3, and save all evidence.
For Business Owners and Leaders
- Financial controls: Dual approval for wires; out-of-band callbacks for new/changed banking instructions; 24-hour hold on first-time vendor payments.
- Email hardening: Enforce SPF/DKIM/DMARC; implement phishing-resistant MFA for all admins and finance users.
- Executive risk: Establish deepfake playbooks, pre-agreed passphrases for urgent approvals, and secure, verified comms channels.
- Vendor risk: Require SOC 2 or equivalent for critical suppliers; audit vendor change controls quarterly.
- Cost model: Compare the median BEC loss (~$50,000) against the cost of MFA, training, and secure email gateways — controls typically pay for themselves after blocking one incident.
For Elderly Users and Caregivers
- New rule: No one legitimate will ever ask for gift cards, crypto, or remote access to “protect” your money.
- Call-back habit: Hang up and call your bank or tech company using the number on your card or their official website.
- Trusted contact: Add a family member to your bank as a secondary contact and agree to check with them before any large transfer.
- Device setup: Enable auto-updates, install reputable security software, and block pop-ups on the main browser.
For Tech-Savvy Users
- Security keys: Use hardware keys (FIDO2) for critical accounts; disable SMS as a fallback where possible.
- Browser isolation: Open unknown links in a disposable VM/browser profile; use password managers for domain verification.
- Crypto hygiene: Cold storage for long-term holdings, multisig for large transfers, frequent allowance reviews, and phishing-resistant wallet connections.
- Detect deepfakes: Watch for head/eye movement artifacts, inconsistent lighting, audio-lip desync; verify identity on a second channel.
Industry Expert Insights
What’s new is the scale and speed. The combination of AI-generated content and well-practiced social engineering makes fraud more convincing and cheaper to run. Official data underscores two realities:
- Money and people: Losses tracked by the FTC ($10B+) and FBI ($12.5B) show the financial stakes, while the DBIR’s 68% human-element figure emphasizes that behavior-focused defenses — verification steps, strong MFA, least privilege — are essential.
- Convergence of scam types: Romance, investment, and BEC tactics increasingly blend. Pig-butchering is not just a romance scam; it’s also an investment and crypto scam. Deepfakes are the new accelerant across them all.
Expect more multi-channel attacks (email + SMS + voice + video) and more “live” impersonation attempts. Organizations that strictly enforce two-channel verification for payments and individuals who slow down and verify using official contact information will remain significantly harder targets.
Immediate Action Steps
- Turn on phishing-resistant MFA for email and financial accounts today; add account alerts for large transactions.
- Create a personal or company “payment verification” rule: no exceptions for urgent requests.
- Save your bank’s fraud hotline and local law enforcement non-emergency number in your phone.
- Back up your data and enable device auto-updates; uninstall unused remote-access tools.
- If you’re a business: run a 30-minute tabletop exercise on a deepfake CEO scenario and a BEC invoice-change scenario this week.
Conclusion
Scammers are betting you’ll act fast and verify later. Flip that script. The latest data from the FTC, FBI, and industry shows billions in preventable losses — much of it triggered by a single click or an unverified request. Whether you’re protecting a family member or a finance department, set clear rules: verify on a second channel, require multi-person approval for payments, and treat unsolicited urgency as a red flag. Make these habits your default, and you’ll stop most scams before they start.