Tech Scams to Watch in 2025: Deepfakes, BEC, Crypto
In one of the most startling frauds of recent memory, a Hong Kong finance worker joined what looked like a routine video call with colleagues—only to be fooled by AI-generated deepfakes of his executives and instructed to wire roughly $25 million to criminals. That single incident captures a broader surge: according to the FTC, consumers reported nearly $10 billion lost to scams in 2023 (up 14% year-over-year), while the FBI’s IC3 logged $12.5 billion in reported cybercrime losses the same year. These losses are powered by fast-evolving tactics—from AI voice and video impersonation to sophisticated business email compromise (BEC), crypto investment schemes, and phishing conducted by bots at massive scale.
Note on data recency: The specific statistics cited below come from authoritative sources published in 2023–early 2024 (FBI IC3, FTC, Chainalysis, Verizon DBIR, and others). Where appropriate, we highlight timelines in the text and link to the original reports in the research sources. Always check the cited sources for the latest updates.
AI Deepfake Scams: Celebrity Impersonation and Fake Video Calls
Recent Cases and Financial Impact
• A multinational in Hong Kong was conned into sending about $25 million after employees attended a video conference where deepfaked versions of leadership directed the transfer (reported February 2024).
• The FBI and other agencies warn that synthetic media (voice and video) is increasingly showing up in social engineering and identity verification attacks. While global loss figures for deepfakes alone are still emerging, these attacks often serve as force multipliers for high-value crimes like BEC and wire fraud.
How This Scam Works
- Reconnaissance: Criminals harvest public video, audio, and social content from executives or celebrities.
- Modeling: They train or tune voice-cloning and face-swapping models to generate convincing synthetic media.
- Pretext: Attackers create urgency—”the deal closes today”, “regulators need immediate payment”—and schedule a call.
- Execution: On a fake video or voice call (sometimes mixed with real participants), targets are told to bypass normal controls to wire funds, share MFA codes, or disclose sensitive data.
- Laundering: Funds are rapidly moved through money mules, crypto mixers, or overseas accounts.
Warning Signs
- Odd video artifacts: unnatural blinking, mismatched lip-sync, or lighting inconsistencies.
- Audio anomalies: latency, robotic tone, or background noise that doesn’t match the video environment.
- New/unknown contact methods: requests to move to personal email, encrypted apps, or one-off conferencing links.
- Bypass of policy: urgent requests to skirt dual authorization, vendor verification, or callback procedures.
Protection Strategies
- Require out-of-band verification for all payment or data requests—e.g., call a known number already on file.
- Implement challenge phrases or code words for executive approvals.
- Adopt liveness checks and multi-person sign-offs for high-value wire transfers.
- Train teams to recognize deepfake telltales; run tabletop exercises simulating fake video calls.
- For tech-savvy users: deploy deepfake detection aids (e.g., frame analysis, audio forensics) and watermarking where available.
Business Email Compromise (BEC): CEO Fraud and Vendor Impersonation
Recent Cases and Financial Impact
• The FBI’s IC3 recorded $12.5 billion in total reported losses across cybercrime in 2023; BEC alone accounted for roughly $2.9 billion in adjusted losses—once again the most expensive single category of cyber-enabled fraud by dollars.
• IC3 logged 880,418 total complaints in 2023; phishing and social engineering are common precursors to BEC incidents.
• Verizon’s 2024 DBIR notes that the human element is implicated in the majority of breaches (68%), reflecting how social engineering bypasses tools and targets people.
How This Scam Works
- Impersonation setup: Attackers spoof an executive’s or vendor’s email domain or compromise a real mailbox through credential theft.
- Invoice or payroll diversion: Criminals submit a subtly altered invoice or banking change request.
- Social pressure: “This is urgent and confidential.” They discourage callbacks or policy checks.
- Funds transfer: Finance teams are rushed into wiring funds to attacker-controlled accounts.
- Money movement: Funds disappear via mules or crypto exchanges within minutes or hours.
Warning Signs
- New bank details without prior notice from a vendor.
- Misspellings or lookalike domains (e.g., substituting rn for m).
- Urgent payment requests outside normal cycles or amounts.
- Requests to keep the transaction secret or bypass two-person approvals.
Protection Strategies
- Enforce mandatory out-of-band callback verification to a known contact before any bank changes or large payments.
- Use email authentication (SPF/DKIM/DMARC) and block newly registered lookalike domains.
- Implement zero-trust access and strong MFA on email and finance apps.
- For business owners: set hard payment thresholds requiring multiple approvers and a waiting period.
- For tech-savvy teams: automate vendor change workflows with cryptographic signing and logging.
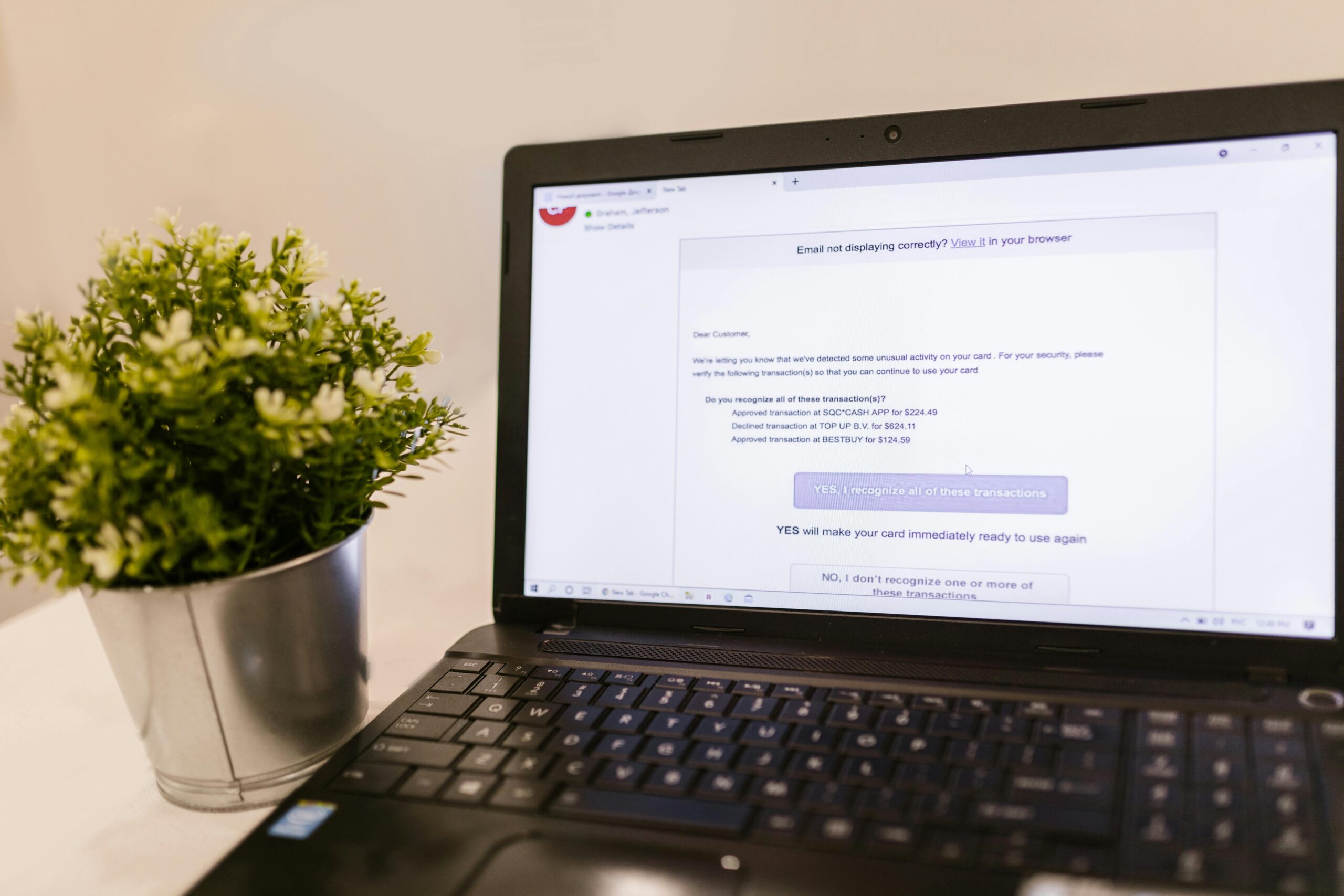
Tech Support Fraud: Fake Microsoft/Apple Calls and Remote Access
Recent Cases and Financial Impact
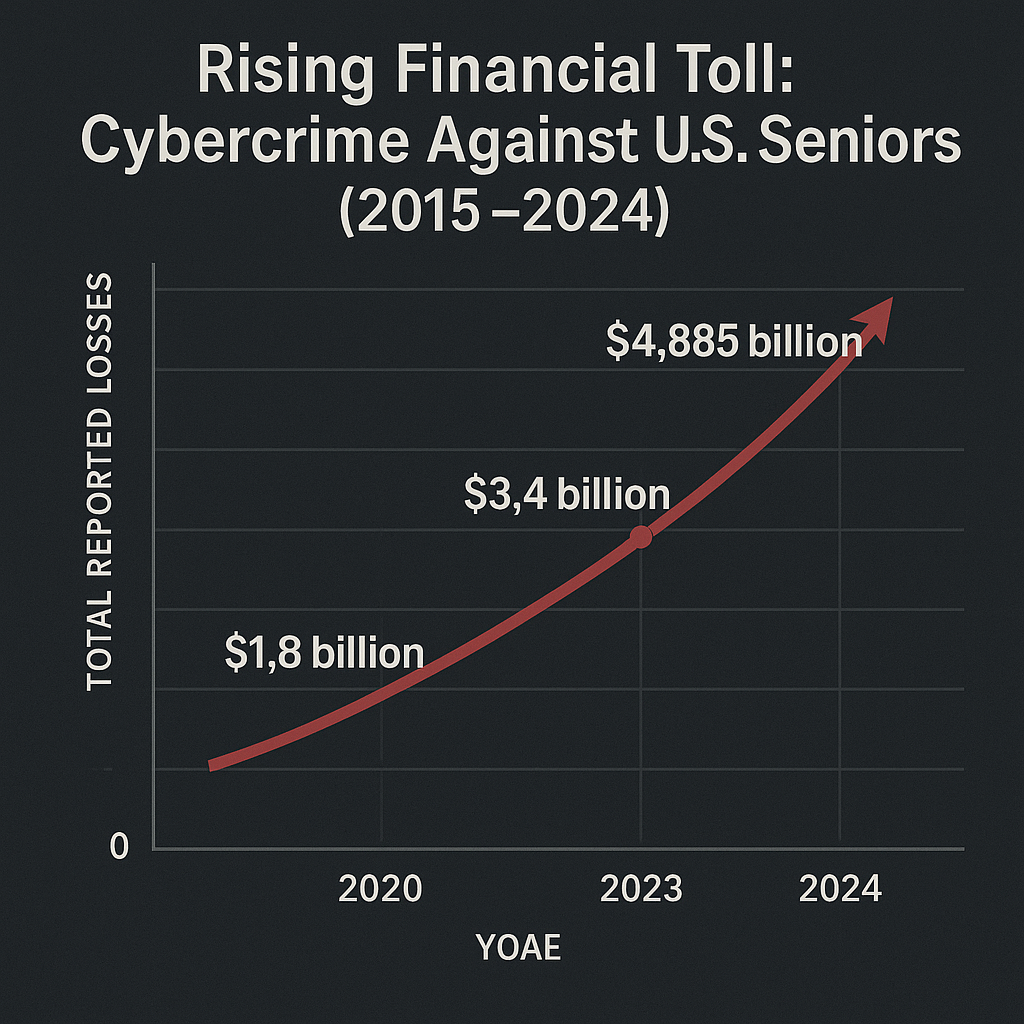
• The FBI’s IC3 reports tech support fraud losses of about $924 million in 2023, with a disproportionate impact on older adults (60+).
• IC3’s Elder Fraud Report shows people 60+ reported $3.4 billion in losses in 2023, with over 100,000 complaints—tech support schemes are consistently among the costliest for seniors.
How This Scam Works
- Trigger: A pop-up imitates a trusted brand (Microsoft, Apple, ISP) claiming your device is infected.
- Hook: A phone number is provided to “fix” the issue; scammers ask for remote access tools.
- Manipulation: They show fake error logs, then push paid “support plans” or refunds.
- Monetization: Attackers request gift cards, bank transfers, or crypto; sometimes they install info-stealers.
Warning Signs
- Unsolicited calls claiming to be from tech companies—legitimate companies don’t cold-call to fix your device.
- Pop-ups that lock the screen and demand immediate payment.
- Requests for gift cards or crypto to pay for support.
- High-pressure tactics and threats of data loss or legal action.
Protection Strategies
- Close suspicious pop-ups; never call numbers shown in alerts.
- Install reputable security software and keep OS/browsers updated.
- For elderly users: pre-configure call screening, browser protections, and a “trusted helper” contact list.
- For businesses: block known remote admin tools for non-IT users; log and alert on remote tool installs.
Cryptocurrency Schemes: Fake Investment Platforms and Crypto Draining
Recent Cases and Financial Impact
• Chainalysis reports that ransomware revenue exceeded $1 billion in 2023—an all-time high—while crypto scam revenue fell to roughly $4.6 billion as several large scam networks were disrupted.
• The FBI’s IC3 classifies investment scams (many crypto-related) as the largest by reported losses, totaling about $4.57 billion in 2023.
How This Scam Works
- Trust building: Criminals befriend targets on social media or dating apps and introduce a “sure-win” crypto platform.
- Demo gains: Fake dashboards show rising balances to entice bigger deposits.
- Lock-in: When victims try to withdraw, “taxes” or “fees” are demanded; funds never arrive.
- Drainers: Wallet-draining scripts trick users into signing malicious approvals that empty accounts.
Warning Signs
- Guaranteed returns or “inside tips.”
- Pressure to move off mainstream exchanges into obscure platforms or private wallets.
- Requests to pay withdrawal “taxes” upfront.
- Unsigned or opaque smart contracts; unfamiliar token approvals.
Protection Strategies
- Verify platforms’ regulatory status; stick to reputable, well-known exchanges.
- Use hardware wallets and review all on-chain approvals before signing.
- For tech-savvy users: enable transaction simulators, set spending limits, and monitor for malicious approvals.
- Never invest based solely on private messages; corroborate with independent sources.
Romance and Social Engineering: Dating App Fraud and “Pig Butchering”
Recent Cases and Financial Impact
• The FTC consistently ranks imposter and romance scams among top loss drivers by category, contributing to the nearly $10 billion consumers reported lost in 2023.
• The FBI’s IC3 has warned that “pig butchering” (long-con investment romance schemes) is a major driver of investment fraud losses, often tied to crypto platforms.
How This Scam Works
- Contact: A “wrong number” text or a match on a dating site leads to friendly conversation.
- Grooming: Weeks of daily chatting build trust and emotional dependence.
- The pitch: The scammer introduces a “private” investment platform with screenshots of big profits.
- Extraction: Victims are urged to invest more, then blocked or bled dry via withdrawal fees.
Warning Signs
- Reluctance to video chat or meet in public.
- Stories that conveniently justify why they need money or cannot verify identity.
- Push to move conversations to encrypted apps immediately.
- Investment advice tied to secrecy or “exclusive opportunities.”
Protection Strategies
- Reverse-image search profile photos; look for inconsistencies.
- Set a personal policy: never send money or invest at a new partner’s suggestion.
- For elderly users and families: discuss common scripts; establish a “call a trusted person” step before any transfer.
- Report suspicious profiles and platforms to the app and to authorities promptly.
Phishing Evolution: AI-Generated Emails, Smishing, and Vishing
Recent Cases and Financial Impact
• The FBI’s IC3 recorded 298,878 phishing-related complaints in 2023, the single most reported crime type by volume.
• Verizon’s 2024 DBIR indicates that the human element (phishing, errors, misuse) is involved in the majority of breaches (68%), underscoring that social engineering remains a front door for attackers.
How This Scam Works
- AI-crafted bait: LLMs generate error-free, personalized emails and texts at scale.
- Multi-channel: Email (phishing), text (smishing), and phone (vishing) reinforce each other.
- Credential theft: Fake login pages harvest passwords and MFA codes.
- Account takeover: Compromised email drives BEC, invoice fraud, and data theft.
Warning Signs
- Unexpected password reset notices or MFA prompts.
- Sender addresses that look right at a glance but differ on close inspection.
- Links that resolve to domains unrelated to the brand.
- Urgent, high-consequence language (“account closed”, “lawsuit filed”).
Protection Strategies
- Use passkeys or phishing-resistant MFA (FIDO2) where possible.
- Enable domain-based message authentication (SPF, DKIM, DMARC) and block newly registered domains.
- For businesses: deploy secure email gateways plus behavioral anomaly detection (impossible travel, unusual vendor edits).
- For consumers: bookmark real login portals; never click auth links in messages; use password managers to detect fake domains.
Industry Expert Insights
• FBI IC3 data shows BEC and investment fraud (often crypto) dominate dollar losses. Phishing remains the most common complaint category, acting as the on-ramp for BEC and account takeover.
• Chainalysis notes ransomware revenue exceeded $1 billion in 2023 even as some scam revenues fell, suggesting high-value targeted operations are growing more professional.
• Verizon’s 2024 DBIR emphasizes that 68% of breaches involve the human element—reinforcing the need for layered controls, user training, and phishing-resistant authentication. Proofpoint’s annual research echoes that nearly all organizations continue to face targeted phishing, smishing, and vishing.
Prediction for 2025: deepfake-enabled BEC will rise, especially for high-value transfers; crypto “drainers” and approval phishing will keep evolving; and AI-assisted phishing will increase the speed, personalization, and grammatical quality of lures. Organizations that combine controls (zero trust, least privilege, verified callbacks) with security culture will be best positioned to reduce risk.
Immediate Action Steps
- For general consumers: freeze your credit, enable account alerts, use a password manager, turn on MFA (prefer FIDO2/passkeys), and bookmark official login pages.
- For business owners: require verified callbacks for payment changes, enforce two-person approvals for wires, deploy phishing-resistant MFA, and log/monitor vendor master file changes.
- For elderly users and caregivers: set call screening, restrict remote-access tools, maintain a “trusted contacts” sheet by the phone, and pre-authorize your bank to hold unusual transfers pending verification.
- For tech-savvy users: use hardware security keys, transaction simulators for crypto, DNS filtering, and EDR on endpoints; monitor dark-web credential exposures.
- Everyone: report incidents quickly to your bank and to the FBI’s IC3; speed improves recovery odds.
Conclusion
Scammers are moving fast—using AI to mimic voices and faces, automating phishing, and hijacking business processes. The good news: simple habits and verified processes stop most losses. Treat every urgent payment or sensitive request as hostile until verified out of band; use phishing-resistant MFA; and train teams and family members on the exact scripts criminals use. If something feels off, pause and verify using a number or channel you already trust. That one extra step is often the difference between a near-miss and a multimillion-dollar loss.