2025 Tech Scam Watch: Deepfakes, BEC, and Crypto Cons
Online fraud is accelerating in sophistication and cost. The FBI’s Internet Crime Complaint Center (IC3) logged more than 880,000 complaints in 2023 with reported losses topping $12.5 billion, driven by investment scams, Business Email Compromise (BEC), tech support fraud, and rapidly evolving AI deepfakes [FBI IC3, 2023]. Consumers also reported nearly $10 billion lost to fraud to the Federal Trade Commission (FTC) in 2023, underscoring how social engineering and digital payments fuel fast, irreversible losses [FTC, 2024]. While these are the most recent comprehensive government tallies available as of late 2024, the techniques behind these losses have only intensified—especially AI-powered impersonation and cross-channel phishing.
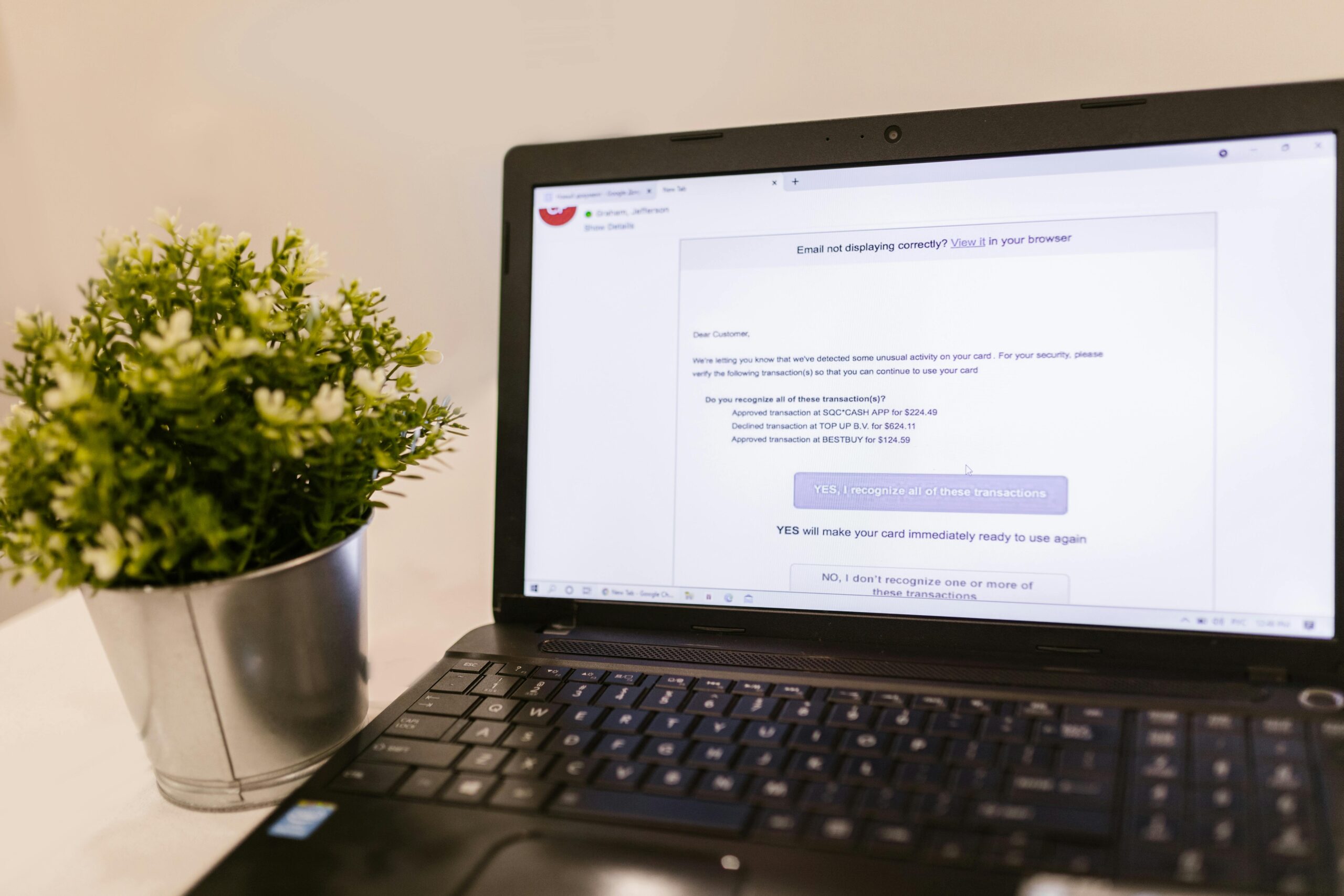
AI Deepfake Scams (celebrity impersonation, fake video calls)
Recent Cases and Financial Impact
– Law enforcement and cybersecurity firms reported surging use of AI-generated voice and video to convincingly impersonate executives and family members, enabling high-dollar social engineering incidents in late 2023–2024 [CISA; industry reports].
– In 2023, the FBI highlighted deepfake-enabled fraud risks in both corporate and consumer contexts, noting the growing use of synthetic media in social engineering [FBI IC3, 2023].
– Verizon’s 2024 Data Breach Investigations Report (DBIR) found the human element is involved in 68% of breaches—a reminder that convincing impersonation remains the most reliable path for attackers [Verizon DBIR, 2024].
How This Scam Works
- Step 1: Recon – Scammers scrape social media, press releases, and public filings to gather voice/video samples and organizational details.
- Step 2: Voice/Video Synthesis – Tools clone voices from seconds of audio and generate lookalike video avatars.
- Step 3: Urgent Pretext – Impersonators initiate a “crisis” via video call, chat, or phone (e.g., a CEO demands a confidential wire; a relative needs emergency funds).
- Step 4: Payment Direction – Victims are steered to instant, hard-to-reverse rails (wires, crypto, gift cards, or instant transfers).
- Step 5: Rapid Cash-Out – Money is quickly moved across accounts or converted to crypto.
Warning Signs
- Unscheduled video calls with poor lip-sync or unusual background artifacts.
- Voice calls where cadence sounds slightly “flat,” robotic, or delayed.
- Requests to bypass standard approval chains or switch to private channels (personal email, encrypted apps).
- Urgency + secrecy framing (“don’t tell anyone,” “board approval pending, act now”).
- Payment instructions that deviate from normal vendors or bank accounts.
Protection Strategies
- Implement mandatory out-of-band verification (call-back to a known, verified number) for any payment or sensitive data request—even if confirmed over video.
- Use strong meeting controls: waiting rooms, unique meeting links, and watermarking for high-risk stakeholder calls.
- Adopt passphrases for family emergency calls and executive transaction approvals.
- Train staff and families with real examples of deepfake voice/video cues; rotate awareness content quarterly.
- For enterprises: deploy identity verification for critical workflows (FIDO2/WebAuthn for accounts; tiered approvals for wires).
Business Email Compromise (CEO fraud, vendor impersonation)
Recent Cases and Financial Impact
– BEC remained one of the costliest cyber-enabled crimes in 2023, with reported losses of roughly $2.9 billion in the IC3 database [FBI IC3, 2023].
– Vendor Email Compromise (VEC) schemes increasingly hijack legitimate supplier threads to redirect invoice payments, often with convincing, context-aware changes to bank details [Abnormal Security; Proofpoint, 2024].
– Real-time payments and faster settlement reduce recovery odds once funds are sent [FTC, FBI IC3].
How This Scam Works
- Step 1: Initial Access – Attackers phish credentials or exploit weak/missing MFA to access a mailbox.
- Step 2: Thread Insertion – They monitor ongoing invoices and projects; create forwarding rules to hide responses.
- Step 3: Impersonation – They use lookalike domains or the compromised mailbox to alter payment instructions.
- Step 4: Funds Diversion – Victims pay to new accounts; money is laundered through mules and crypto.
Warning Signs
- Subtle domain typos (acmec0rp.com vs acmecorp.com), new bank details mid-contract, or “we changed banks” notices.
- Unusual timing (late Friday) or urgent requests to split payments into multiple new accounts.
- Auto-forward rules you didn’t create; inbox anomalies; unexpected MFA prompts.
Protection Strategies
- Require MFA on email for all accounts, prioritize phishing-resistant MFA (FIDO2).
- Enforce dual-control and verified call-backs for any change to vendor banking details.
- Use DMARC enforcement (p=reject), SPF, DKIM, and brand indicators (BIMI) where supported.
- Deploy anomaly detection for invoice changes and supplier payment edits.
- Have a rapid response playbook: immediately contact your bank and file with IC3 if a wire is misdirected.
Tech Support Fraud (fake Microsoft/Apple calls, remote access)
Recent Cases and Financial Impact
– IC3 reported tech support fraud losses exceeding $1.0 billion in 2023, with older adults disproportionately affected [FBI IC3, 2023].
– The FBI’s Elder Fraud analysis showed victims aged 60+ lost over $3.4 billion in 2023, with median losses of around $7,250, and tech support schemes a leading driver [FBI Elder Fraud, 2023].
How This Scam Works
- Step 1: Contact – Pop-up browser alerts, cold calls, or search ads claim your device is infected.
- Step 2: Urgency – The “technician” pressures you to act now to prevent data loss or charges.
- Step 3: Remote Access – They ask you to install remote tools; then plant fake errors.
- Step 4: Payment/Draining – They collect fees, request gift cards/crypto, or access banking apps while connected.
Warning Signs
- Unsolicited security alerts or calls claiming to be from Microsoft/Apple or your bank.
- Requests to install remote-control software or disable your security tools.
- Payment via gift cards, crypto, or wire for “support fees.”
Protection Strategies
- Never call phone numbers shown in pop‑ups; close the tab and run your own security scan.
- Only seek support via official vendor sites you type yourself into the browser.
- For families: pre-set a trusted helper list and a “no remote access” rule unless initiated by you.
- For businesses: restrict local admin rights; block risky remote tools; monitor for unusual remote sessions.
Cryptocurrency Schemes (fake investment platforms, crypto draining)
Recent Cases and Financial Impact
– Investment fraud drove the highest reported losses in 2023, at about $4.57 billion, a large share tied to crypto-themed scams including so-called “pig butchering” [FBI IC3, 2023].
– Blockchain analytics firms reported persistent scams using fake trading dashboards and liquidity pool tricks, even as some illicit crypto categories declined in 2023 [Chainalysis, 2024].
How This Scam Works
- Step 1: Grooming – Scammers build rapport via social media, messaging apps, or dating platforms.
- Step 2: Demos & Dashboards – Victims see fabricated “profits” on slick sites or apps.
- Step 3: Lock-In – After a small withdrawal, victims are encouraged to add more capital.
- Step 4: Exit – Payouts are blocked; pressure and threats escalate; accounts are drained or closed.
- Crypto-drainer kits: malicious signing prompts trick victims into granting token approvals, enabling wallet drains.
Warning Signs
- Guaranteed returns, VIP “insider” tips, or pressure to move to a specific exchange/app.
- Unverified apps, sideloaded APKs, or requests to share wallet seed phrases.
- Smart contract prompts you don’t understand; repeated requests to “reconnect wallet.”
Protection Strategies
- Use hardware wallets and limit token approvals; regularly revoke approvals using reputable tools.
- Verify platforms through multiple sources; avoid links sent in DMs or unfamiliar groups.
- Assume unsolicited investment outreach is a scam—especially on dating/social apps.
- For businesses: implement custody policies, multisig approvals, and transaction monitoring on corporate wallets.
Romance/Social Engineering (dating app fraud, pig butchering)
Recent Cases and Financial Impact
– The FTC continues to rank imposter and romance/investment hybrid scams among top loss categories, with consumers reporting nearly $10 billion to fraud in 2023 and heavy losses tied to social media/dating contacts [FTC, 2024].
– IC3 attributes billions in losses to investment scams that commonly originate through long-con social grooming (“pig butchering”) [FBI IC3, 2023].
How This Scam Works
- Step 1: Contact – Scammers initiate on dating sites or misdial/text pretexts (“Hi, is this Alex?”).
- Step 2: Bonding – Weeks of daily messages, shared interests, and future plans build trust.
- Step 3: Opportunity – The “partner” introduces a low-risk, high-return investment—often crypto.
- Step 4: Escalation – After small “wins,” victims are pressured to invest more, even borrow.
- Step 5: Vanish – Access is cut off; platforms disappear; new identities appear elsewhere.
Warning Signs
- Early requests to move off-platform to encrypted apps.
- Unwillingness to meet via live, spontaneous video with verifiable context.
- Financial topics introduced within days/weeks; guaranteed or exclusive returns.
Protection Strategies
- Keep conversations on the platform initially; use reverse image searches on profile photos.
- Never invest based on a relationship alone; involve a third-party advisor before sending money.
- For families: establish a “no-secret-loans” rule and a trusted check-in person for large transfers.
Phishing Evolution (AI-generated emails, smishing, vishing)
Recent Cases and Financial Impact
– Phishing remains the most common initial vector; the 2024 Verizon DBIR attributes 68% of breaches to the human element, including phishing and pretexting [Verizon DBIR, 2024].
– IC3 has long recorded phishing as the top category by complaint volume; combined email, smishing, and vishing feed BEC and account takeover downstream [FBI IC3, 2023].
How This Scam Works
- Step 1: Lure – AI-polished emails/texts use current events, HR/payroll notices, or package delivery hooks.
- Step 2: Link/Attachment – QR codes (“quishing”), lookalike portals, or macros prompt credential entry.
- Step 3: Takeover – Attackers harvest MFA codes via real-time prompts or MFA fatigue.
- Step 4: Lateral Movement – Compromised accounts fuel BEC/VEC, payroll redirects, or data theft.
Warning Signs
- Subtle domain or URL mismatches; QR codes from unknown senders.
- Unexpected MFA push prompts; unusual login alerts.
- Payment/benefits updates requiring urgent login from a link in the message.
Protection Strategies
- Adopt phishing-resistant MFA (FIDO2 security keys) and disable SMS fallback where feasible.
- Use password managers to auto-fill only on legitimate domains—this blocks many phish.
- Deploy email authentication (SPF/DKIM/DMARC) and advanced email security with QR/URL rewriting.
- Run frequent, targeted simulations on smishing/vishing and coach, not shame, after failures.
Audience-Specific Guidance
For General Consumers
- Use a password manager + security keys (or app-based MFA) on email, banking, and cloud storage.
- Never pay with gift cards or crypto to settle “fees,” “taxes,” or “support” charges.
- Set bank account alerts for transactions and new payees; enable account lock if available.
- Agree on a family passphrase for emergencies; verify unexpected money requests with a call-back.
For Business Owners
- Require dual approval and call-back verification for any new or changed vendor bank details.
- Roll out phishing-resistant MFA, conditional access, and least-privilege for email and finance systems.
- Implement DMARC enforcement, supplier risk monitoring, and invoice anomaly detection.
- Practice an incident response drill: how to recall a wire, notify banks, and file with IC3 quickly.
For Elderly Users and Care Networks
- Pre-approve trusted helpers for tech and finances; keep a written list of official support numbers.
- Never allow unsolicited remote access; hang up and call your bank or device maker directly.
- Banks/courts/police do not demand payment in gift cards or crypto.
- Set transaction limits and alerts; use a companion account for large transfers.
For Tech-Savvy Users
- Use security keys, disable SMS MFA recovery, and monitor token approvals in crypto wallets.
- Adopt DNS filtering, app sandboxing, and browser isolation for high-risk tasks.
- Instrument mailboxes: alert on new forwarding rules, impossible travel, and OAuth consent grants.
- Validate meeting invites: unique links, lobby enabled, watermarking or liveness checks for sensitive calls.
Industry Expert Insights
– Scaling AI: Voice and video cloning lower the cost of convincing pretexts. Expect more blended attacks where deepfake calls confirm forged emails.
– Faster payments risk: As instant rails expand, recovery windows shrink. Prevention and pre-transaction verification are paramount.
– Supplier ecosystems: VEC thrives because it leverages trust between real businesses. Continuous vendor verification and DMARC enforcement will separate resilient firms from victims.
– Passwordless momentum: Wider adoption of passkeys/security keys will cut credential phishing success, pushing attackers toward session hijacking and social engineering around MFA.
– Mobile-first phishing: Smishing and QR-based “quishing” bypass some email defenses. Mobile anti-phishing and user coaching must catch up.
Immediate Action Steps
- Turn on phishing-resistant MFA (security keys) for your primary email and bank today.
- Set bank alerts for new payees and transactions over a threshold you define.
- Create a family or team passphrase for money requests and emergency calls.
- Enable DMARC p=reject on your domain; verify vendor bank details by phone before changes.
- Install a password manager on all devices; rotate passwords for email, banking, and cloud.
- For businesses: run a 30-minute BEC drill this week—simulate a vendor bank change and test approvals.
Conclusion
The con has gone high-tech, but the defense still starts with verification. Deepfakes can imitate faces and voices; BEC can hijack genuine email threads; crypto dashboards can simulate profits. Make it policy—at home and at work—that no payment or sensitive action proceeds without an independent check using known-good contact information. Pair that culture with phishing-resistant MFA, strong email authentication, and tight payment controls, and most modern scams lose their edge.