Passkeys in 2025: Your Playbook to Stop Phishing Now
If you’re still juggling passwords and six‑digit codes, you’re playing on the attacker’s turf. Phishing kits now steal both passwords and one‑time passcodes in real time, SIM swaps sidestep SMS, and push “MFA fatigue” tricks users into approving rogue logins. The good news: passkeys—phishing‑resistant, passwordless sign‑in—are now widely supported across Apple, Google, Microsoft, and major password managers. This guide shows you how they work, why they matter, and how to switch in a weekend.
Why Passkeys Are a Target Now
Online fraud is not slowing down. The FBI’s Internet Crime Complaint Center (IC3) reported $12.5 billion in reported losses in 2023, a sharp year‑over‑year increase (FBI IC3, 2023). The Federal Trade Commission separately reported that consumers lost more than $10 billion to fraud in 2023 alone (FTC, 2024). And attackers keep exploiting the human edge: the 2024 Verizon Data Breach Investigations Report found 68% of breaches involved a human element—phishing, misdelivery, and errors among them (Verizon DBIR, 2024).
Conventional logins are easy to trick. Passwords can be phished or reused across sites. One‑time passcodes (OTP) sent over SMS can be intercepted via SIM swapping. Even app‑based codes and push prompts can be stolen through real‑time phishing and social engineering. Passkeys change the game by removing secrets users can be tricked into sharing.
What’s a passkey? A passkey is a phishing‑resistant login credential built on FIDO2/WebAuthn standards. It’s made of a key pair: a private key that stays on your device (guarded by Face ID, Touch ID, or a device PIN), and a public key stored by the website or app. During sign‑in, your device proves possession of the private key and cryptographically signs a challenge tied to the specific site—so fake look‑alike pages can’t harvest anything reusable.
Why it matters now: In 2023, Google made passkeys the default sign‑in option for Google Accounts, accelerating mainstream adoption. CISA, the U.S. cybersecurity agency, explicitly recommends “phishing‑resistant MFA,” meaning FIDO2 security keys or passkeys, for high‑value accounts. NIST’s identity guidelines also recognize authenticator assurance levels that map to stronger, phishing‑resistant methods.
Top 3 Threats to Watch
1. Real‑Time Phishing That Steals Passwords and Codes
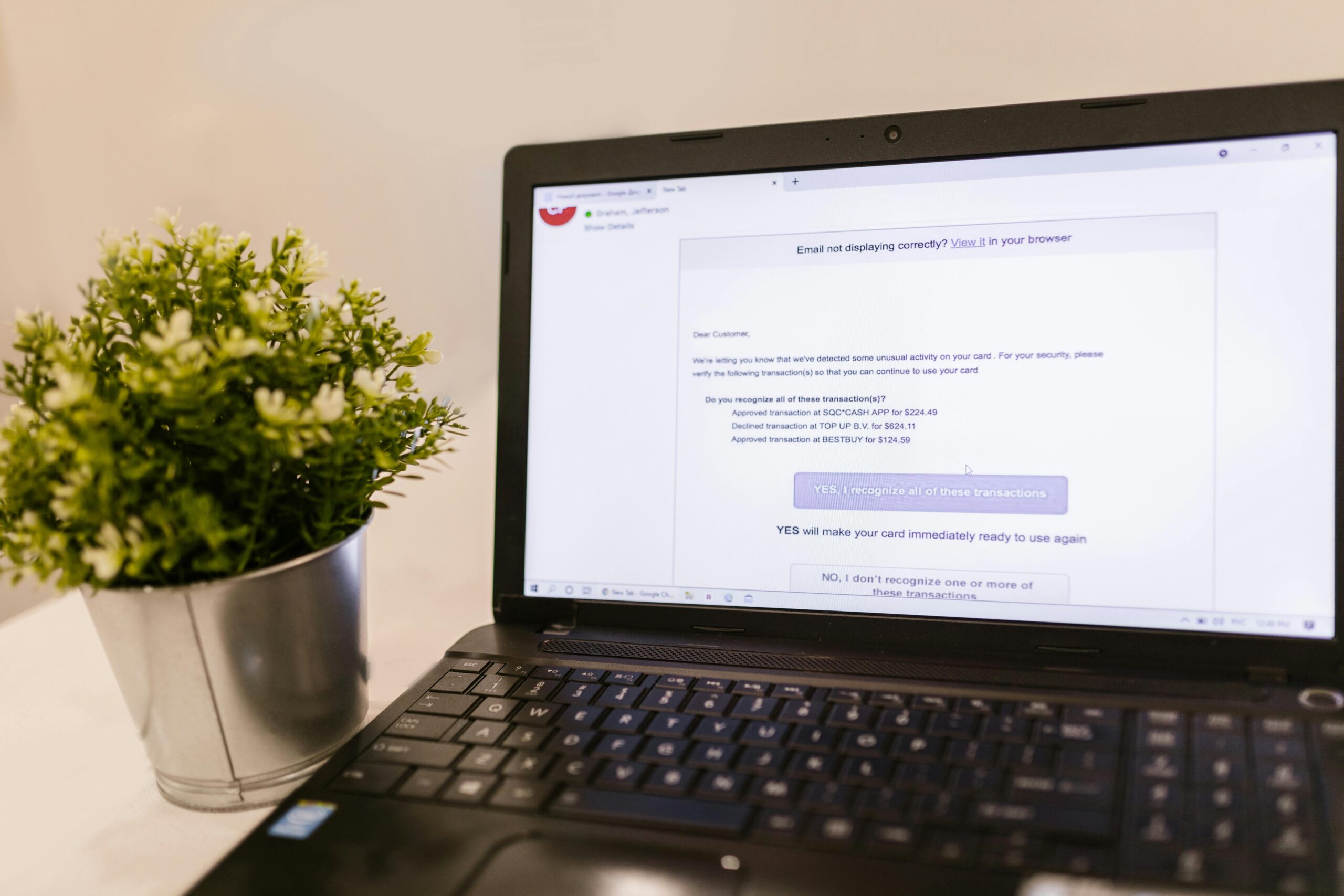
Threat: Crimeware kits proxy your session to the real site, capturing both your password and the one‑time code the moment you enter it. They may also push endless “approve sign‑in” prompts until you accept—known as MFA fatigue.
Example & Case Study: In 2022, Uber confirmed an attacker used social engineering and MFA fatigue to gain access to internal systems. The intruder spammed push prompts and contacted the user on WhatsApp, eventually convincing them to approve a login. Once in, the attacker pivoted through internal tools. A phishing‑resistant method (passkey or hardware security key) would have blocked the attack because the authenticator signs only the legitimate site’s challenge; a fake site or rogue prompt can’t reuse anything the user types or taps.
2. SIM Swapping That Hijacks SMS Codes
Threat: A criminal convinces or bribes a carrier agent to port your phone number to a SIM card they control. Your SMS codes—and sometimes voice calls—now go to the attacker.
Impact: Accounts relying on SMS two‑factor become vulnerable. Even cautious users can be locked out while attackers reset passwords elsewhere.
Why passkeys help: Passkeys don’t use SMS. The secret never leaves your device, and nothing travels over the phone network that a fraudster can divert.
3. Credential Stuffing and Password Reuse
Threat: Attackers test billions of stolen username/password combos from past breaches against other sites, hoping you reused a password.
Impact: Even strong passwords fail if reused. Attackers target email, cloud storage, banking, social media, and crypto exchanges—where a single hit can cascade.
Why passkeys help: There’s no password to guess or reuse. Each site has its own key pair, and private keys cannot be exfiltrated by typing mistakes or look‑alike domains.
Practical Defense Guide (Step‑by‑Step)
- Step 1: Turn on passkeys for your primary identity. Start with the account that protects everything else—usually your email.
- Google: Visit myaccount.google.com > Security > Passkeys. Create a passkey on your phone and computer. If you use Chrome, Edge, or Safari, your device can store and sync passkeys through your platform’s secure enclave or your password manager.
- Apple (iCloud/Apple ID): On iOS/iPadOS 17+ or macOS Sonoma+, passkeys are built into iCloud Keychain. Ensure iCloud Keychain is on (Settings > iCloud > Passwords & Keychain). Many apps and sites will prompt to “Save a passkey.”
- Microsoft: Go to account.microsoft.com > Security > Advanced security options > Passkeys. Register a platform passkey or FIDO2 security key.
- Step 2: Add at least two phishing‑resistant authenticators. Redundancy prevents lockouts.
- Register a hardware key (e.g., a FIDO2 security key) alongside your device‑bound passkeys. Keep one on your keychain and one in a safe place.
- When possible, enroll multiple devices (phone + laptop) so you’re not dependent on a single device.
- Step 3: Migrate your high‑value accounts. Move the crown jewels first:
- Email accounts (all providers you use)
- Financial accounts (banks, brokerages, crypto exchanges)
- Password manager (the vault protects everything—enable passkey or security keys if supported)
- Cloud storage & dev tools (Apple, Microsoft, Google, GitHub, AWS)
- Marketplaces & social (PayPal, eBay, Amazon, X, Instagram, Facebook)
Not every site supports passkeys yet. If they don’t, choose an authenticator app (TOTP) over SMS, and add a hardware security key if available as a backup factor.
- Step 4: Lock down your recovery and fallback options.
- Remove SMS as the default 2FA where you can. Switch to passkeys or authenticator apps.
- Set unique recovery emails and phone numbers you actively control.
- Save backup codes in a secure place (password manager secure notes or a printed, locked copy). Do not screenshot them to your photo roll.
- Step 5: Harden your devices (your new keys).
- Enable a strong device screen lock (biometrics + PIN/password). If someone can unlock your phone/laptop, they can use your passkeys.
- Turn on full‑disk encryption (enabled by default on modern iOS/Android/macOS/Windows when you set a passcode and sign in).
- Update OS and browsers to the latest versions to ensure WebAuthn support and security patches.
- Enable device‑finding and remote wipe (Find My, Find My Device) in case of loss or theft.
- Step 6: Plan for loss or replacement.
- Sync passkeys securely using your platform (iCloud Keychain, Google Password Manager) or a password manager that supports passkeys (e.g., 1Password, Dashlane). Sync guards against single‑device failure.
- Keep a spare hardware key offsite. Label it and test it quarterly.
- Document your recovery workflow (which accounts have passkeys, where backup codes live, who your emergency contact is). A single page can save days later.
- Step 7: Turn on login alerts and risky‑sign‑in prompts.
- Enable sign‑in notifications for your email and financial accounts. Act immediately on any alert you didn’t initiate.
- Review active sessions and trusted devices monthly. Sign out old sessions; revoke trust on devices you no longer use.
Recommended Tools/Resources
Use official setup pages and authoritative guidance:
- CISA: Implementing phishing‑resistant MFA (FIDO2/security keys). Guidance from the U.S. Cybersecurity and Infrastructure Security Agency.
- NIST SP 800‑63B: Digital Identity Guidelines for authenticator assurance levels and best practices.
- Google Accounts: Passkeys dashboard to create, manage, and remove passkeys.
- Apple Platform: iCloud Keychain passkeys on iOS, iPadOS, and macOS.
- Microsoft Accounts: Passkeys and FIDO2 security keys management.
- Hardware keys: FIDO2‑certified keys (e.g., YubiKey, Google Titan). Register at least two.
- Password managers with passkeys: Consider vendors that support passkey creation and sync across devices.
How Passkeys Work (Plain English)
With passwords, you prove who you are by typing a secret the website also knows. If a fake site tricks you into typing it, the attacker can reuse that secret. With passkeys, your device proves who you are by signing a challenge with a private key that never leaves your device. The site verifies the signature with your public key. Because the signature is bound to the real site’s domain, a fake site can’t collect anything reusable. There’s no password to steal, and nothing to “type” that can be shoulder‑surfed or proxied.
Even if malware or a malicious proxy tries to relay your session, the origin binding means the cryptographic exchange fails on impostor domains. That’s what “phishing‑resistant” means in practice.
Where Passkeys Fit with MFA
Think of passkeys as the best blend of what you have (your device or security key) and what you are (your biometric), delivered in one step. They replace passwords entirely on sites that support them. You can still keep other factors enabled for recovery, but the goal is to make passkeys the primary login—and demote SMS to a last‑ditch fallback or remove it altogether where policies allow.
When a Site Doesn’t Support Passkeys (Yet)
- Prefer app‑based codes (TOTP) over SMS. Authenticator apps resist SIM swaps and reduce exposure to carrier fraud.
- Use push prompts sparingly and enable number matching or geolocation prompts where available to reduce MFA fatigue attacks.
- Set tight alerts and limits on money movement (wire transfers, external account links) and require re‑authentication for high‑risk actions.
Proof That Stronger Auth Matters
- $12.5B in losses: The FBI IC3 says reported losses in 2023 hit $12.5 billion, reflecting the scale of account takeover and cyber‑enabled fraud (IC3, 2023).
- $10B in consumer fraud: The FTC reports more than $10 billion lost by consumers in 2023 (FTC, 2024), underscoring the urgency of upgrading defenses.
- 68% human element: Verizon’s 2024 DBIR attributes 68% of breaches to the human element—where phishing‑resistant authentication has outsized impact (Verizon, 2024).
Quick Wins This Weekend
- Saturday morning: Turn on passkeys for your Google, Apple, and Microsoft accounts. Register your phone, laptop, and a hardware security key.
- Saturday afternoon: Migrate your bank, broker, and PayPal/Stripe accounts. Where passkeys aren’t available, switch to an authenticator app and create new, unique passwords in your password manager.
- Sunday: Lock down recovery: remove SMS where possible, save backup codes, and print a one‑page recovery plan. Test logging in from a second device to make sure you’re not single‑point‑of‑failure.
Frequently Asked Concerns
What if I lose my phone? That’s why you enroll multiple authenticators (e.g., laptop + phone + hardware key) and keep backup codes. If you use a password manager or platform that syncs passkeys end‑to‑end, your credentials can be restored to a new device after secure sign‑in.
Are biometrics stored by the website? No. Your fingerprint or face data never leaves your device. It only unlocks the private key stored in your device’s secure enclave.
Can malware on my device steal passkeys? Passkeys are designed so private keys can’t be exported even if malware runs in user space. But device hygiene still matters: keep OS and browsers updated, don’t sideload shady apps, and consider a separate security key for your highest‑risk accounts.
Will passkeys work when traveling or offline? Yes, platform passkeys work offline because the challenge is signed locally. You need a network connection only for the service to verify and complete the login.
Do I still need a password manager? Yes, for sites that haven’t adopted passkeys and for storing recovery notes, backup codes, and secure documents. Many modern managers also store and sync passkeys.
Conclusion
You can’t out‑train every phish or out‑run every SIM swap. But you can change the rules of engagement. Passkeys remove reusable secrets from the login flow and anchor authentication to your real device and the real site. In 2025, moving your primary identity and money accounts to phishing‑resistant authentication is the single highest‑leverage security upgrade most people can make. Do it once, keep a spare key, and stop playing the attacker’s game.
Real‑world case study sources and guidance are listed below.