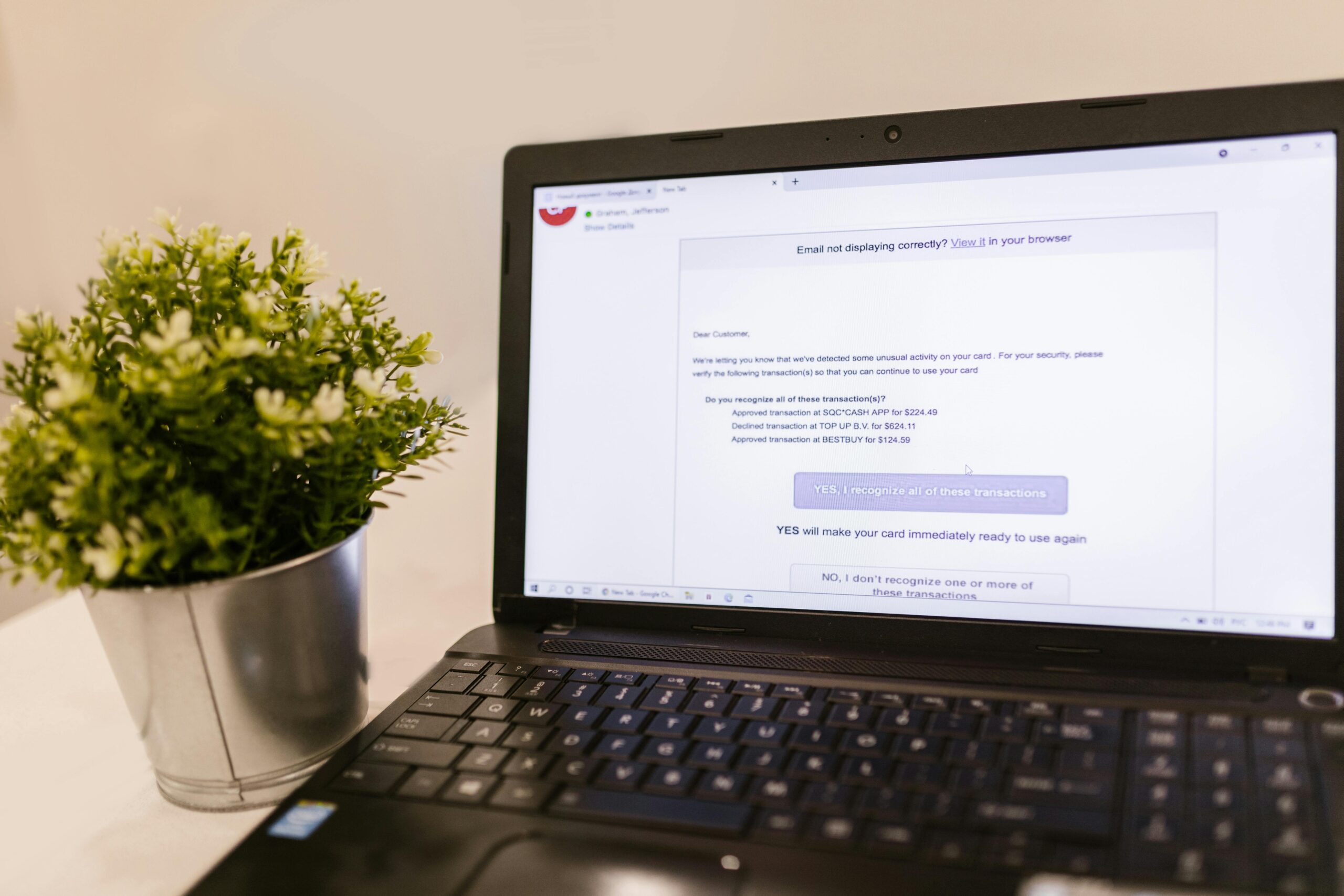
Criminals use artificial intelligence to copy your loved ones’ voices and demand emergency money.
By Sarah Mitchell – Cybercrime Correspondent
A Call No Family Should Ever Receive
It was a quiet Wednesday evening in Surrey when Margaret, a 72-year-old grandmother, picked up the phone. On the line was a familiar voice — her grandson Daniel.
“Nan, it’s me. I’ve been in an accident. I need money quickly or they won’t let me leave the hospital.”
Margaret’s heart sank. The voice sounded exactly like Daniel’s — the same tone, the same nervous laugh he always had when he was embarrassed. Without hesitation, she rushed to her computer, ready to transfer £2,000 into the bank account details he gave her.
But something didn’t sit right. Why was Daniel calling from an unknown number? Why was he asking for such urgency?
Margaret did something that saved her life savings. She called a cybersecurity helpline instead of transferring the money. The expert who answered told her the truth: her “grandson” wasn’t Daniel at all. It was a fraudster using advanced AI voice cloning technology.

A Growing Crime Wave
What happened to Margaret is no longer rare. Voice cloning — once the stuff of science fiction — is now a booming cybercrime industry. Criminals use a few seconds of someone’s voice, often stolen from social media videos, to build a convincing replica that can say anything.
According to the UK’s National Fraud Intelligence Bureau, cases of AI-generated voice scams increased by over 400% in 2024, with victims losing an average of £3,000 per incident.
“These scams are terrifyingly effective,” says Detective Chief Inspector Rachel Morrison from the City of London Police. “When people hear the voice of a loved one in distress, they react emotionally — and that’s exactly what the criminals are counting on.”
Protect Your Finances Before It’s Too Late
Scammers are getting smarter every day. Speak to a certified cybersecurity expert now — before you’re targeted.
Call Now for Free Expert Help: (855) 247-9875How the Scam Works
Cybersecurity researchers explain that the process is chillingly simple:
- Voice Collection – Criminals scrape voice samples from TikTok, YouTube, or even voicemail greetings.
- AI Training – Free or cheap software can mimic that voice within minutes.
- The Call – Scammers call the victim, posing as a loved one in distress.
- The Hook – They demand urgent money transfers or sensitive personal details.
Dr. Helen Walsh, a cybersecurity researcher at Cambridge University, notes: “All you need is 30 seconds of clear audio. The AI does the rest. To the human ear, it’s almost indistinguishable from the real person.”

Victims Speak Out
“I thought it was my daughter begging me for help,” recalls 68-year-old Alan from Manchester. “The voice was perfect. Same accent, same words she would use. I nearly emptied my savings account before my wife stopped me.”
In another case, a couple in Birmingham sent £5,000 to what they believed was their nephew abroad. The money was gone within hours, routed through offshore accounts that made recovery impossible.
Experts believe thousands of cases remain unreported, as many older victims feel too embarrassed to admit they were fooled.

Don’t Wait Until It Happens to You
Even if you’ve never been targeted, your details may already be for sale online. Call today and learn how to protect yourself.
Call Now — Speak to an Expert: (855) 247-9875Why Older Generations Are Being Targeted
Criminals deliberately focus on retirees and grandparents. Why?
- Trusting Nature – Older generations grew up in an era where a phone call could be trusted.
- Emotional Hooks – Calls often involve grandchildren in danger, tugging at heartstrings.
- Financial Stability – Many retirees have savings, making them lucrative targets.
Professor Katherine Mills, Director of the UK Cybercrime Research Centre, says: “Scammers exploit love and trust. The more caring you are, the more vulnerable you may be.”
The Cost of Falling for the Scam
The financial loss is devastating, but experts warn the emotional toll is even worse.
Victims often describe sleepless nights, broken trust, and deep guilt — especially when they realize the criminals tricked them using the voice of someone they love most.
Margaret, the Surrey grandmother, admits: “I felt so foolish. I would have lost everything if I hadn’t made that extra call.”

How to Protect Yourself
Cybersecurity experts offer these simple but life-saving steps:
- Verify First – If you get a distress call, hang up and call your loved one back on their normal number.
- Set Family Passwords – Agree on a private code word for emergencies.
- Be Skeptical of Urgency – Real hospitals and police do not demand immediate bank transfers.
- Never Share Financial Details – Especially over the phone with unverified callers.
- Use the Expert Hotline – Trained specialists can help you check if a call is real.
A National Security Warning
The National Crime Agency has warned that voice cloning is “the next frontier of fraud.” Criminal networks are already combining cloned voices with deepfake video calls to create scams that fool even experienced professionals.
Dr. Amanda Park, a leading cybersecurity analyst, stresses: “The technology is advancing faster than public awareness. Without professional verification, anyone could be tricked.”
Stay One Step Ahead of Scammers
Don’t wait for the next suspicious call, text, or email. Get peace of mind today with free, expert guidance available 24/7.
Call Now — Free Consultation: (855) 247-9875Closing Note
Voice cloning scams are spreading rapidly, targeting the most vulnerable members of society. The criminals rely on fear, love, and urgency to trick ordinary people into handing over their life savings.
The message from experts is simple: Never act alone. Always verify first.
☎️ Protect yourself and your family today. Call (855) 247-9875 for free, immediate cybersecurity guidance.