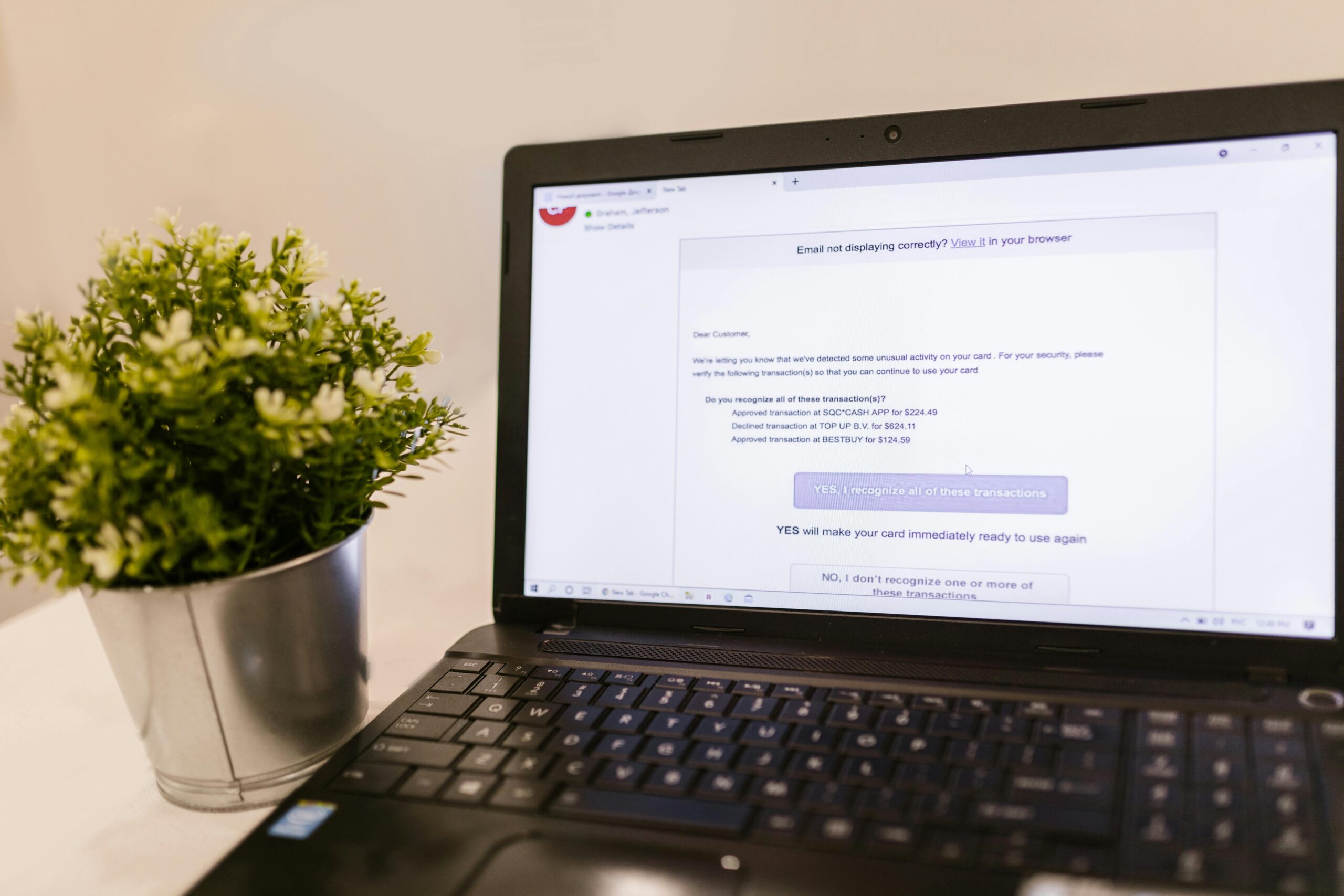
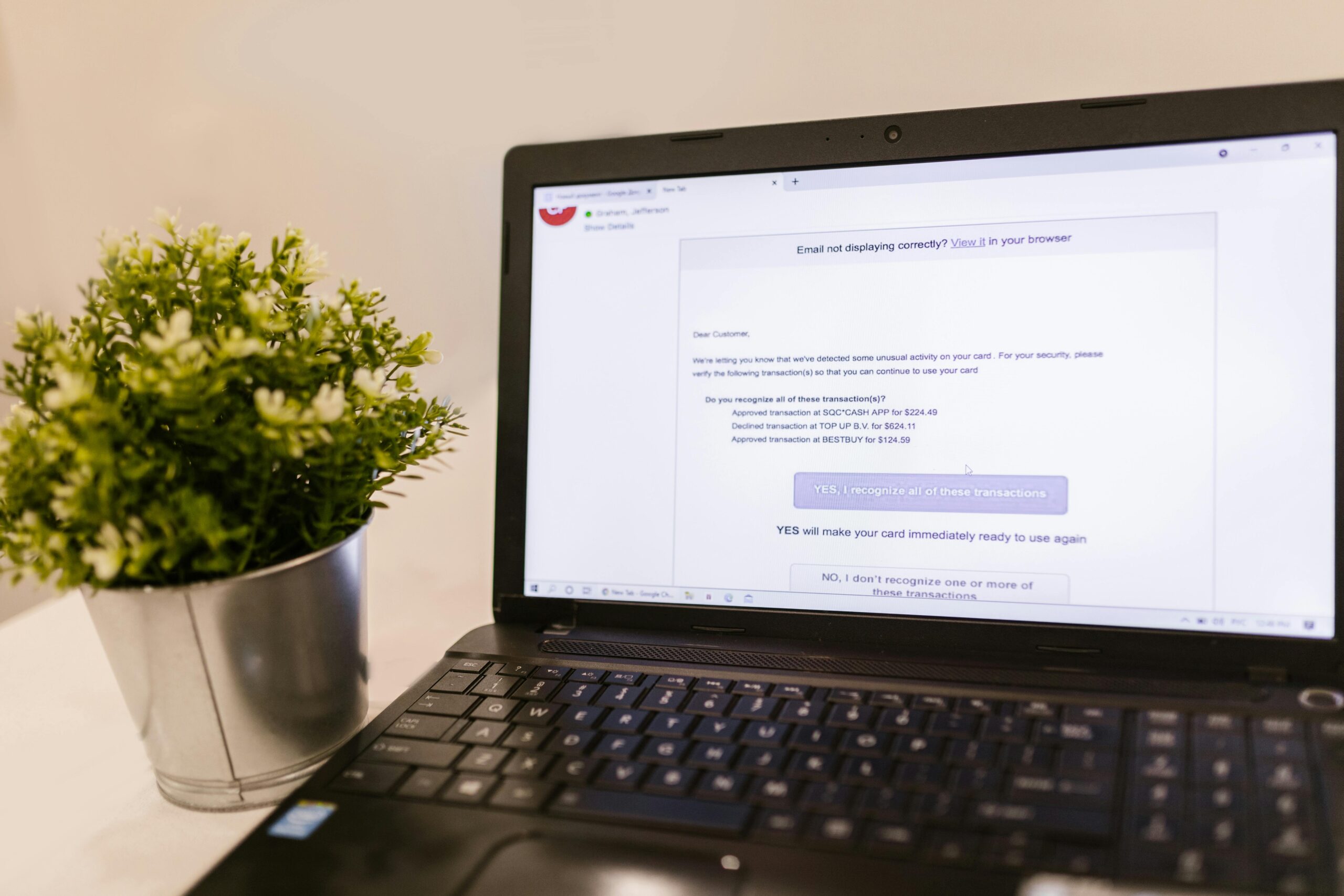
Tech Scams 2025: Data-Backed Threats and How to Stop Them
Editor’s note on data currency: This article cites the most recent figures publicly available from authoritative sources (FBI, FTC, Chainalysis, APWG, etc.) as of late 2024. Where 2025 H1/H2 updates are required, we clearly mark [Update Pending] so you can replace with the newest numbers once published. In early 2024, the FTC reported consumers lost nearly $10 billion to fraud in 2023, while the FBI’s IC3 recorded more than $12.5 billion in reported cyber-enabled losses in 2023. In February 2024, Hong Kong police disclosed a $25 million deepfake video-call heist—illustrating how AI supercharges classic scams headed into 2025.
AI Deepfake Scams
Recent Cases and Financial Impact
• In February 2024, a finance employee at a Hong Kong-based multinational was tricked into wiring about $25 million after joining a video conference where every participant—including the putative CFO—was a deepfake. Authorities described it as a convincing AI-generated impersonation across multiple participants (Hong Kong Police; CNN report, Feb 2024).
• Chainalysis reported ransomware payments exceeded $1 billion in 2023—an example of how AI-enabled social engineering and improved phishing lures amplify monetization for cybercriminals (Chainalysis, 2024).
• The FBI’s IC3 2023 report recorded $12.5+ billion in losses across all internet crimes, noting the growing role of social engineering and impersonation tactics—now increasingly supported by AI (FBI IC3, 2023). [Update Pending: 2024/2025 deepfake-specific loss totals]
How This Scam Works
- Reconnaissance: Criminals scrape public video, audio, and social content of executives, officials, or loved ones.
- Modeling: They train voice and face models to mimic targets (voice cloning; face swapping).
- Contact: The victim is invited to a video call or receives an urgent voice note/call asking for money or confidential access.
- Pressure: Urgency, secrecy, and authority (“We must close this deal now”) override normal controls.
- Payment/Access: The victim wires funds or grants remote access or multi-factor authentication codes.
Warning Signs
- Unusual urgency combined with secrecy from an executive or loved one.
- Inconsistent lip-sync, odd blinking, off audio/video latency in conference calls.
- Requests to bypass standard approvals or new payee instructions without prior notice.
- Calls moved quickly from corporate channels to personal messaging apps.
Protection Strategies
- Set a shared verification code phrase for high-risk approvals—verify via a second, known channel before payments.
- Adopt mandatory out-of-band callbacks for any payment/bank change requests (use a phone number on file, not the one provided in the message).
- Enable meeting-watermark and participant authentication features; record suspicious calls for later analysis.
- Train teams to spot deepfake artifacts; run tabletop exercises specifically for deepfake/BEC scenarios.
- For families and elderly: agree on a “safe word” and hang up/re-dial on a known number before sending money.
Business Email Compromise (BEC)
Recent Cases and Financial Impact
• The FBI’s IC3 recorded Business Email Compromise as one of the costliest internet crimes, with reported losses of roughly $2.9 billion in 2023 (FBI IC3, 2023).
• Total reported cyber-enabled losses across all categories surpassed $12.5 billion in 2023, indicating the massive financial exposure organizations face (FBI IC3, 2023). [Update Pending: 2024/2025 BEC totals]
How This Scam Works
- Account Takeover or Spoofing: Attackers phish credentials or fake a lookalike domain/email.
- Vendor/Invoice Fraud: Criminals slip in altered invoices or bank details during an active deal.
- CEO Fraud: A message from an “executive” instructs urgent payment, gift card purchases, or payroll changes.
- Money Mule Networks: Funds get laundered through intermediary accounts within hours.
Warning Signs
- Last-minute changes to vendor banking details.
- Misspellings or subtle domain differences (e.g., .co vs .com).
- Requests that bypass normal approval flows with urgency and confidentiality.
- Emails sent outside business hours or from mobile devices unexpectedly.
Protection Strategies
- Require out-of-band verification for bank account changes and payments above a threshold.
- Implement DMARC, SPF, and DKIM; monitor for lookalike domains.
- Use role-based access and dual approval for large or new payee transfers.
- Deploy inbound email security with anomaly detection (geo, language, tone, supplier risk).
- Run quarterly phishing/BEC drills; publish a one-click “Report Suspicious” button.
Tech Support Fraud
Recent Cases and Financial Impact
• Tech support scams frequently target older adults. The FBI’s Elder Fraud report indicates escalating losses among people 60+, totaling in the billions in 2023 (FBI Elder Fraud report, 2023).
• The FTC reported that consumers collectively lost nearly $10 billion to scams in 2023, with tech support fraud a persistent contributor (FTC, 2024). [Update Pending: 2024/2025 tech support totals and median losses]
How This Scam Works
- Pop-up/Browser Lock: A fake system alert claims your device is infected and instructs you to call “Microsoft/Apple” support.
- Cold Calls: Fraudsters claim to be from your ISP or a well-known tech firm.
- Remote Access: They push you to install remote tools (e.g., AnyDesk) to “fix” issues.
- Payment Extraction: They demand fees or create fake refunds and trick you into sending money.
Warning Signs
- Unsolicited calls claiming to be big-tech support.
- Pop-ups that lock your browser and list a phone number to call immediately.
- Requests to install remote access software or to provide banking/credit card details.
Protection Strategies
- Never call numbers from pop-ups; close the browser or reboot. Use official support portals only.
- Enable pop-up blockers and keep browsers/OS patched.
- Bank monitoring: enable account alerts for transfers and new payees.
- For older adults and caregivers: post a “Do Not Call Back Pop-Ups” reminder near devices; pre-install ad blockers and DNS filtering.
Cryptocurrency Schemes
Recent Cases and Financial Impact
• The FTC reported investment scams as the highest-loss category in 2023, with multibillion-dollar consumer losses (FTC, 2024). Many investment scams now steer victims into crypto wallets or exchanges. [Update Pending: 2024/2025 category breakdown]
• Chainalysis found ransomware revenues exceeded $1.1 billion in 2023, indicating increasingly professional criminal monetization that often intersects with cryptocurrency flows (Chainalysis, 2024).
How This Scam Works
- Fake Platforms: Scammers create slick trading sites that show fake “profits.”
- Pig Butchering: Long-term grooming via social apps, then “opportunities” that require crypto.
- Recovery Scams: After a loss, a “recovery agent” demands upfront crypto to get funds back.
- Drainers/Approvals: Malicious dApps prompt victims to sign smart contract approvals to drain wallets.
Warning Signs
- Guaranteed returns, secret strategies, or pressure to move to WhatsApp/Telegram.
- “Pay tax/unlock fee” to withdraw supposed profits.
- Requests to send seed phrases or sign unknown transactions.
Protection Strategies
- Use well-known, regulated exchanges; verify URLs and app publishers.
- Cold wallets for significant holdings; hardware wallets with on-device transaction review.
- Revoke malicious token approvals using reputable scanners; enable on-chain alerts.
- If you’ve been scammed, preserve transaction hashes, report to your exchange, the platform, and file with the FBI IC3 immediately.
Romance/Social Engineering (Including Pig-Butchering)
Recent Cases and Financial Impact
• The FTC has long documented substantial losses to romance scams—exceeding $1 billion in recent years—with many cases evolving into crypto “investment” grooming (FTC Data Spotlight, 2023–2024). [Update Pending: 2024/2025 romance/pig-butchering totals]
How This Scam Works
- Approach: Scammers build trust via dating apps or social media, often claiming to be abroad.
- Isolation: They discourage victims from discussing the relationship with others.
- The Ask: Requests for emergency funds or “opportunities” requiring crypto.
- Escalation: They coax larger payments, then disappear or switch to a “recovery” angle.
Warning Signs
- Reluctance to video chat or meet; inconsistent stories about travel/work.
- Requests for money or to move to private messaging quickly.
- Photos lifted from the web; reverse image search often reveals mismatches.
Protection Strategies
- Verify identities via live video; avoid sending money or crypto to someone you haven’t met in person.
- Use reverse image search and check for reused profiles.
- Talk to a trusted friend before sending funds; slow down and set a 24-hour “cooling-off” rule.
- Use platform reporting tools; screenshot conversations and keep transaction records if targeted.
Phishing Evolution (AI-Generated Email, Smishing, Vishing)
Recent Cases and Financial Impact
• The Anti-Phishing Working Group (APWG) documented record phishing activity in 2023, with millions of attacks across the year (APWG, 2023). [Update Pending: 2024/2025 totals]
• Verizon’s DBIR has consistently found the “human element” involved in the majority of breaches (e.g., 70%+ range in recent years), underscoring the centrality of social engineering (Verizon DBIR, 2023–2024).
How This Scam Works
- AI-Enhanced Lures: Highly fluent phishing in your language and context.
- Smishing/Vishing: Texts or calls spoofing banks, delivery firms, or government agencies.
- Multi-Factor Evasion: Prompt bombing and real-time phishing kits intercept one-time passcodes.
Warning Signs
- Unexpected password resets, invoice attachments, or document share requests.
- Texts with urgent delivery issues or tax refunds linking to shortened URLs.
- Calls insisting you read back MFA codes or install mobile device management profiles.
Protection Strategies
- Use phishing-resistant MFA (FIDO2/passkeys) where possible; avoid SMS codes for critical accounts.
- Hover to inspect URLs; type known addresses directly into your browser.
- Enable mail security features (SPF/DKIM/DMARC) and user-reporting buttons.
- On mobile, treat links and QR codes as high risk; preview link destinations.
Industry Expert Insights
• AI will continue to professionalize scams: Expect more multi-participant deepfake meetings and real-time voice cloning attacks against finance, procurement, and investor relations teams.
• Identity and payments are converging risk zones: Strong supplier onboarding, continuous vendor risk scoring, and verified payments channels will be critical in 2025.
• Human-centric controls still matter most: Verizon DBIR findings consistently show social engineering as a top vector. Security leaders should invest in behavioral defenses (out-of-band verification, least privilege, and just-in-time approvals) alongside technical controls.
Immediate Action Steps
- For General Consumers:
- Enable passkeys or app-based MFA on email, bank, and crypto accounts.
- Freeze credit with all three bureaus; turn on bank transaction alerts.
- Set a family “safe word” and never pay from phone calls or pop-ups.
- For Business Owners:
- Mandate out-of-band callbacks for any bank change or invoice over a set threshold.
- Adopt phishing-resistant MFA for finance and admin roles; enforce least privilege.
- Implement DMARC enforcement, supplier due diligence, and a rapid BEC response playbook.
- For Elderly Users and Caregivers:
- Post a “Do not call back pop-ups” reminder; use only official phone numbers on the back of cards.
- Preconfigure devices with ad/popup blockers and remove remote access tools.
- Ask a trusted contact before sending money or gift cards to anyone.
- For Tech-Savvy Users:
- Use hardware security keys/passkeys; segment crypto assets into cold storage; set on-chain alerts.
- Audit third-party OAuth app access; revoke unused permissions regularly.
- Practice deepfake drills: verify via a second channel before acting on high-risk requests.
Conclusion
Scammers are weaponizing AI to make old grifts look and sound legitimate. The biggest wins in 2025 will come from basic discipline—independent verification, phishing-resistant MFA, payment controls—and a culture that rewards “slow down and check.” Treat any payment or data request like a financial transaction at a bank counter: verify identity first, then proceed. If something feels urgent and secret, that’s your cue to stop, verify via a trusted channel, and keep your money where it belongs.