2025 Tech Scams: Deepfakes, BEC, Crypto Cons, and What You Can Do Now
Online fraud is accelerating in scale and sophistication. The FBI’s Internet Crime Complaint Center (IC3) logged $12.5 billion in reported losses in 2023 alone—its highest ever—driven by investment fraud, business email compromise, tech support scams, and rapidly evolving phishing and deepfake schemes (Source: FBI IC3 2023). Meanwhile, the FTC tallied $10 billion in consumer fraud losses in 2023 across all categories (Source: FTC Consumer Sentinel 2023). Early 2024 and beyond saw criminals weaponize AI to impersonate executives on live video calls and spin up convincing voice clones—threats that are now reaching both households and boardrooms (Source: BBC; CISA).
AI Deepfake Scams
Recent Cases and Financial Impact
• Hong Kong police reported a theft of roughly $25 million after a finance worker joined a video meeting where all participants—seemingly including the CFO—were AI-generated deepfakes (reported Feb 2024) (Source: BBC).
• U.S. and EU authorities warn that deepfake audio and video are increasingly used to facilitate executive impersonation, sextortion, and fraudulent fund transfers (Sources: CISA deepfake guidance; FBI IC3 2023 report notes evolving impersonation tactics).
• IC3 reports business email compromise (BEC) losses of $2.9 billion in 2023, and experts note deepfakes amplify these social-engineering schemes by adding persuasive audio/video to email or chat pretexting (Source: FBI IC3 2023).
How This Scam Works
- Reconnaissance: Criminals scrape public videos, webinars, interviews, and social posts to train AI models on a target executive’s voice and likeness.
- Pretext setup: Attackers trigger urgency via email, chat, or messaging (e.g., late-night deal, vendor crisis) and schedule a “quick” video huddle.
- Live deepfake: On the call, a cloned voice and synthetic face direct a subordinate to process an unusual payment or share sensitive credentials.
- Funds exfiltration: Money moves to a mule or crypto off-ramp, splintered through accounts and cashed out rapidly.
Warning Signs
- Unusual payment requests tied to secrecy or time pressure.
- Inconsistent lip-sync, lighting, or lag on video; robotic phrasing or missing micro inflections in audio.
- Requests to bypass normal approvals “just this once.”
- New or previously unused accounts for urgent transfers.
Protection Strategies
- Use out-of-band verification (call a known number, not the meeting/chat link) for money or data requests—this defeats most deepfake setups.
- Mandate dual control and written confirmations for wire, ACH, crypto, or gift card disbursements above a low threshold.
- Limit public exposure of executive media; restrict high-quality voice/video samples where practical.
- Educate staff with examples and run drills on “how to spot a deepfake video call scam.”
Business Email Compromise (BEC)
Recent Cases and Financial Impact
• BEC led to $2.9 billion in reported losses in 2023, making it one of the costliest cyber-enabled crimes tracked by the FBI (Source: FBI IC3 2023).
• The Verizon 2024 DBIR confirms that the human element (including phishing, pretexting, and misuse) is present in the majority of breaches, underscoring BEC’s social-engineering core (Source: Verizon DBIR 2024).
• Vendor and invoice fraud variants increasingly target accounts payable, with fraudsters lurking in legitimate email threads to change banking details shortly before payment (Observed widely by incident responders; see Abnormal Security 2024 Email Threat Report).
How This Scam Works
- Initial access: Compromised email via password reuse, MFA fatigue, SIM swap, or token theft.
- Silent observation: Attackers study invoice cycles, tone, and authority lines.
- Pretext and timing: They inject a thread-hijacked request to “update banking info” right before a real invoice is due.
- Cash-out: Funds land in money mule accounts, then move through shells or crypto to evade clawbacks.
Warning Signs
- Bank detail changes sent right before payment deadlines.
- Subtle domain lookalikes (e.g., rn vs. m), or supplier replies that skip prior signatures.
- Uncharacteristic urgency or secrecy, even if the email sits in a legitimate thread.
Protection Strategies
- Use supplier-of-record callbacks for any banking changes; verify via a number on file.
- Apply DMARC enforcement, phishing-resistant MFA (e.g., FIDO2 security keys), and conditional access.
- Segregate duties: AP cannot both approve and release payments; require dual control.
- Implement payment hold-and-review windows and bank positive pay/ACH blocks.
Tech Support Fraud
Recent Cases and Financial Impact
• Tech support scams produced more than $1.3 billion in reported losses in 2023, a steep rise year over year (Source: FBI IC3 2023).
• Older adults bear a disproportionate burden: victims aged 60+ reported over $3.4 billion in losses across all cyber-enabled crimes in 2023, with tech support among the top schemes (Source: FBI Elder Fraud 2023).
• FTC guidance continues to flag fake “Microsoft” or “Apple” pop-ups/calls, remote access, and refund scams as dominant patterns (Source: FTC Tech Support Scams).
How This Scam Works
- Scareware: A browser pop-up claims a virus and lists a phone number; or an unsolicited call purports to be “Microsoft” or your bank.
- Remote control: Scammers push remote-access tools to “fix” the issue and move money to a “safe account.”
- Refund ruse: They pretend to overrefund and pressure you to return funds via crypto ATM, wire, or gift cards.
Warning Signs
- Any pop-up or caller demanding remote access to “remove a virus.”
- Requests to pay by crypto, gift cards, or wire to fix a computer issue.
- Pressure not to hang up or call your bank directly.
Protection Strategies
- Close the browser tab; never call numbers in pop-ups. Reboot if needed.
- Only seek help from your device maker or a trusted local technician you initiate.
- Banks never ask you to move funds to a “safe” account. End the call and dial your bank’s number on your card.
- For caregivers: enable call screening, browser pop-up blockers, and block remote access tools by policy.
Cryptocurrency Schemes
Recent Cases and Financial Impact
• Investment fraud led all FBI IC3 categories at $4.57 billion in 2023; a large share involved cryptocurrency “pig butchering” and fake platforms (Source: FBI IC3 2023).
• Chainalysis reported that while some crypto scam revenues dipped in 2023, romance-investment hybrids and impersonation schemes remained resilient (Source: Chainalysis 2024 Crypto Crime Report).
• BEC actors increasingly request cryptocurrency or stablecoins to speed cash-out and complicate recovery (Observed trend in FBI reporting and 2024 industry telemetry).
How This Scam Works
- Long con: Scammers build trust on social apps or messaging, then “introduce” a high-return crypto platform.
- Fake dashboards: Victims see fabricated profits and are nudged to invest more.
- Exit trap: Withdrawals are blocked by bogus “taxes” or “fees” before funds vanish.
Warning Signs
- Guaranteed returns, VIP groups, or insider tips.
- Pressure to keep the opportunity secret, move to a specific app, or split transactions.
- Unregulated “brokers” refusing video verification or audited statements.
Protection Strategies
- Use only registered exchanges and check licensing where you live.
- Verify URLs and custody policies; avoid links shared by strangers.
- Start small, test withdrawals early, and never invest money you can’t afford to lose.
- Enable hardware wallet or multi-sig for long-term holdings.
Romance and Social Engineering (Pig Butchering)
Recent Cases and Financial Impact
• The FTC reports consumers lost $10 billion to fraud in 2023 across all types, with romance scams continuing to generate high median losses (Source: FTC CSN 2023).
• Romance-investment hybrids (“pig butchering”) are a key driver within the FBI’s $4.57 billion investment fraud category (Source: FBI IC3 2023).
• Older adults and recent widowers are frequently targeted, with heavy emotional manipulation and isolation tactics (Source: FBI Elder Fraud 2023).
How This Scam Works
- Grooming: Daily texts build intimacy and reliance.
- Opportunity: The scammer “shares” a profitable crypto or forex play “for us.”
- Escalation: Small wins and screenshots coax larger deposits.
- Cut-off: Withdrawals blocked; the scammer disappears or pivots to extortion.
Warning Signs
- Reluctance to meet on video or in public; excuses about cameras or security.
- Fast-tracked intimacy and financial advice from a new online connection.
- Demands for secrecy from family and banks.
Protection Strategies
- Reverse-image search profile photos; verify identities with multiple live video calls.
- Bring a trusted friend into the conversation if money enters the picture.
- If an “investment” requires secrecy or a specific app, walk away.
- Report to the platform, FTC, and IC3 immediately; preserve chats and payment records.
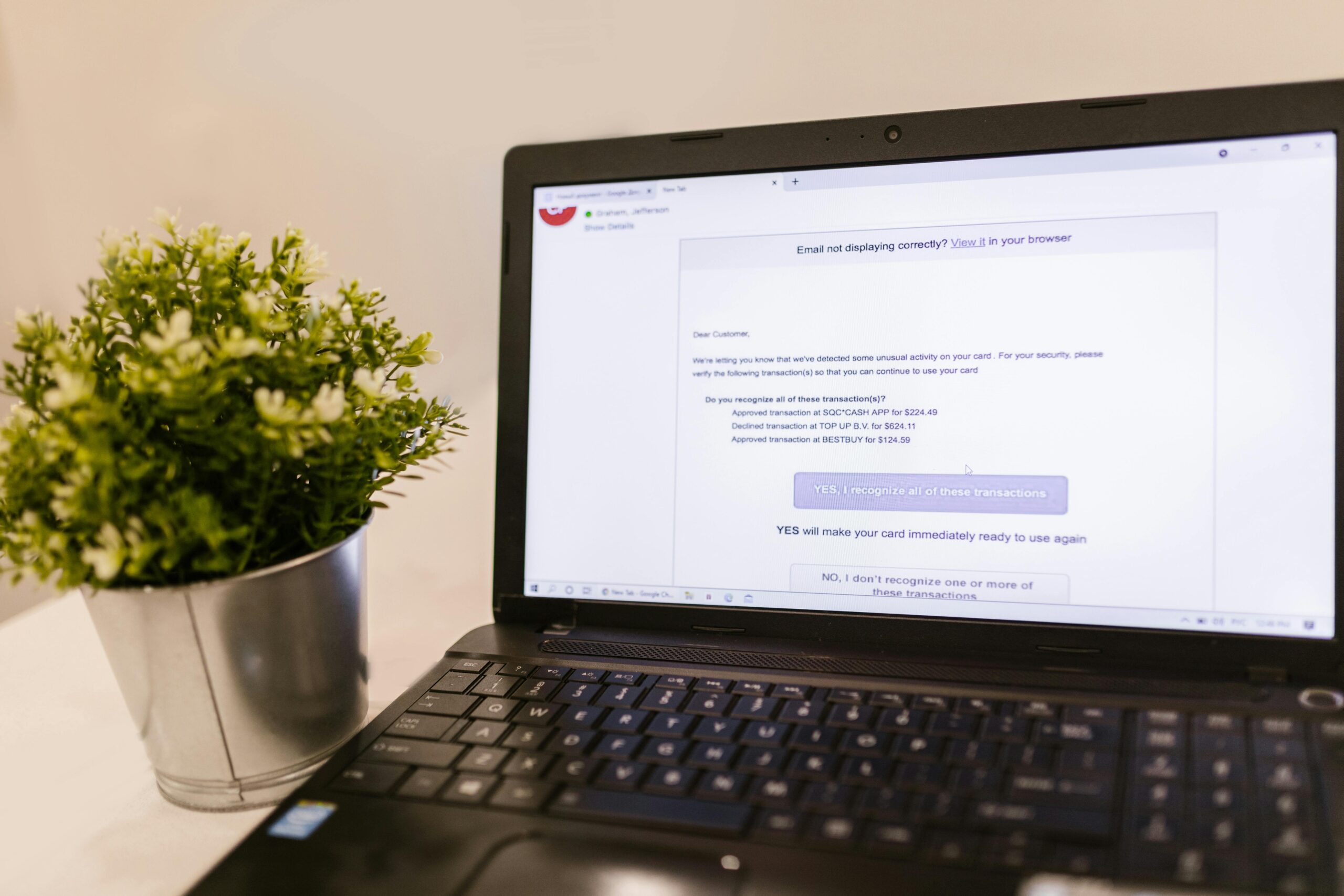
Phishing Evolution: Email, Smishing, Vishing, and Quishing
Recent Cases and Financial Impact
• The Verizon 2024 DBIR attributes the majority of breaches to the human element, with phishing and pretexting central to initial access (Source: Verizon DBIR 2024).
• Proofpoint’s 2024 State of the Phish observes persistent vishing and smishing pressure on organizations, alongside QR-code phishing (“quishing”) campaigns (Source: Proofpoint 2024).
• Phishing is often the entry point for BEC, ransomware, and payroll diversion, compounding losses reported to IC3 and the FTC (Sources: FBI IC3 2023; FTC CSN 2023).
How This Scam Works
- Email: Thread hijacking and brand lookalikes deliver malware, MFA-bypass links, or request credentials.
- Smishing: Texts push fake delivery notices, bank alerts, or tax refunds to harvest logins.
- Vishing: Call-center social engineers drive victims to read MFA codes or install remote tools.
- Quishing: QR codes in emails or on posters redirect to credential theft pages that bypass URL filters.
Warning Signs
- Mismatched sender domains, shortening services, and odd spelling or grammar in supposedly “official” messages.
- Links or QR codes urging immediate login “or lose access.”
- Unexpected password reset prompts or MFA pushes you didn’t initiate.
Protection Strategies
- Adopt phishing-resistant MFA (FIDO2 keys) and disable legacy authentication.
- Use an allowlist DNS resolver and email security with DMARC, DKIM, and SPF enforcement.
- Train using real-world simulations (including smishing and vishing) and measure report rates.
- For individuals: go to the site directly—never via links/QR codes in unsolicited messages.
Industry Expert Insights
Trendlines point to three converging risks: (1) AI-enabled social engineering (deepfake voice/video, auto-generated phishing) that raises the success rate of old cons; (2) accelerated cash-out via crypto rails and money mules, reducing recovery windows; and (3) cross-channel attacks—email plus SMS plus voice—that erode single-control defenses. The Verizon DBIR’s human-element finding underscores that controls must be layered across identity, communications, and payment authorization. FBI and FTC data show losses heavily concentrated in investment fraud, BEC, and tech support scams; expect 2025 reports to reflect more deepfake-assisted pretexting and broader targeting of small and mid-sized businesses that lack treasury controls.
Immediate Action Steps
- General Consumers
- Bank and device hygiene: enable automatic updates, use a password manager, and turn on MFA everywhere.
- Never call numbers in pop-ups; hang up on unsolicited tech or bank calls and dial the official number on your card.
- For investments, test withdrawals early and avoid platforms pushed by new online acquaintances.
- Business Owners
- Payments: dual approval for all wires/ACH; enforce supplier-of-record callbacks for bank changes.
- Identity: deploy phishing-resistant MFA (security keys), conditional access, and privileged access management.
- Email: enforce DMARC, implement advanced phishing and BEC detection, and log retention for thread hijacking analysis.
- Run tabletop exercises for deepfake/BEC scenarios and publish a staff playbook for out-of-band verification.
- Elderly Users and Caregivers
- Use call screening and enable carrier spam blocking; keep a written “do-not-pay” list: no gift cards, crypto ATMs, or urgent wires.
- Place bank transfer limits and alerts; designate a trusted contact for large transactions.
- Caregivers: lock down remote-access tools and browser pop-ups; prefer in-person tech help.
- Tech-Savvy Users
- Use hardware security keys, passkeys, and device-bound credentials wherever available.
- Adopt DNS filtering, script-blocking, and containerized browsers for risky tasks.
- Verify software supply chain (hashes/signatures) and isolate wallets on hardware devices with multisig.
Conclusion
Scammers haven’t invented new crimes—they’ve supercharged old ones with AI and faster payment rails. That’s why the best defense mixes human verification (voice/number you know), disciplined payment controls, and strong identity security. Whether you’re approving a vendor invoice, helping a parent handle a pop-up, or tempted by a “can’t miss” crypto win, treat urgency as your cue to slow down and verify. If you encounter a scam, report it to the FTC and FBI IC3 immediately—rapid reporting can aid recovery and helps authorities spot patterns before they reach someone you love.