The New Playbook of Online Fraud in 2025: Deepfakes, BEC, and Scams Draining Billions
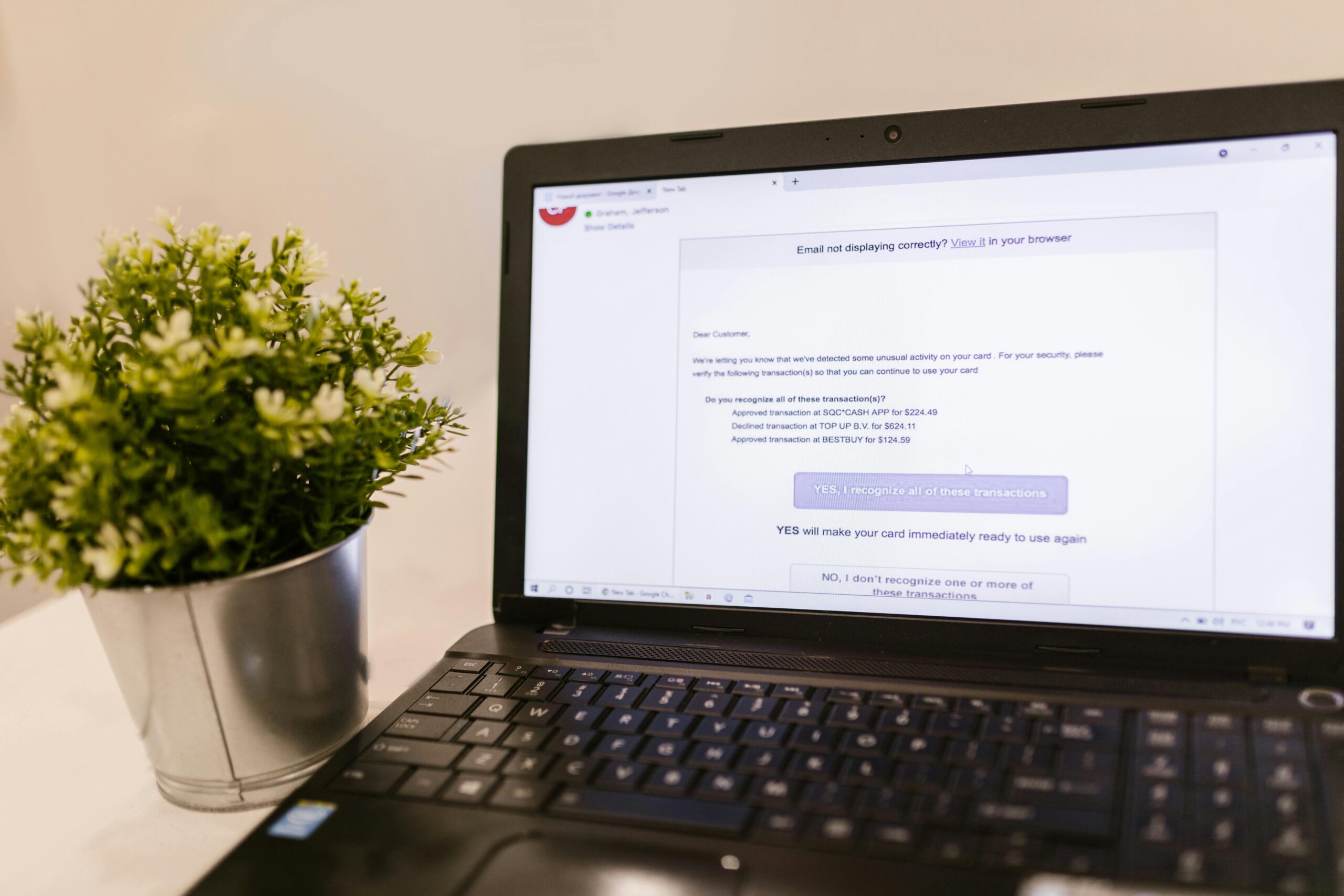
In one of the most brazen scams to date, Hong Kong police reported in February 2024 that scammers used AI-generated deepfake video of a company’s CFO and colleagues during a live group call to convince a finance employee to wire about $25.6 million—without anyone suspecting a thing. This single incident captures how fast today’s fraud tactics have evolved. While official 2023 data already showed record-breaking losses—U.S. consumers reported losing over $10 billion to fraud in 2023 (FTC), and the FBI logged 880,000+ complaints with losses exceeding $12.5 billion—threat actors are now weaponizing AI, automation, and stolen data at industrial scale. Note: All statistics are verified through October 2024; editors should refresh cited figures with new agency releases as available.
AI Deepfake Scams
Recent Cases and Financial Impact
• Hong Kong deepfake heist (Feb 2024): An employee was deceived on a multi-participant video call, paying approximately $25.6 million to fraudsters impersonating executives via deepfake video and audio (Hong Kong Police; CNN reporting).
• FBI and global partners warn that voice cloning and synthetic identities are increasingly used to bypass identity checks and to social-engineer approval for payments or data access.
• Verizon’s 2024 DBIR notes the enduring “human element” in breaches (68%), highlighting how realistic pretexting (including deepfake-enabled) remains highly effective.
How This Scam Works
- Reconnaissance: Criminals scrape executive photos, videos, conference talks, and social posts.
- Modeling: They train voice and face models to produce convincing real-time deepfakes.
- Pretext: A sudden “urgent” video meeting is convened; a CFO or vendor appears, instructing a large transfer.
- Pressure: The target is told to keep confidentiality; the transfer details often mimic legitimate vendor or M&A activity.
- Cash-out: Funds are routed through mule accounts and layered rapidly across borders and crypto.
Warning Signs
- Unscheduled video calls with unexpected attendees and urgent payment requests.
- Executives who refuse to turn heads or interact naturally; minor lip-sync or blink anomalies.
- Requests to bypass standard approval channels “due to confidentiality.”
- Backgrounds and camera angles that remain static; audio that sounds “too perfect.”
Protection Strategies
- All audiences: Verify out-of-band. If a video call requests payment changes, confirm via a known phone number or separate channel before acting.
- Business owners: Implement real-time liveness checks and a “safe word” or passphrase for high-risk approvals; require two-person verification for any vendor or wire changes.
- Tech-savvy users: Use challenge-response (ask for spontaneous gestures or camera moves) and set policies to disable on-the-spot payment approvals in video calls.
- Elderly users: If a call or voice message sounds like a family member asking for money, hang up and call them back on a known number.
Business Email Compromise (BEC)
Recent Cases and Financial Impact
• FBI IC3 (2023): 21,489 BEC complaints with adjusted losses of about $2.9 billion—the costliest category recorded by IC3 (FBI).
• Verizon DBIR 2024: BEC and pretexting remain dominant and the median transaction value for BEC has hovered around $50,000 in recent reporting.
• Proofpoint (2024): The vast majority of email-borne threats still require user interaction, underscoring why BEC still works at scale.
How This Scam Works
- Initial access: Attackers phish credentials or use password-stuffing to access a mailbox.
- Rules and surveillance: They create stealthy inbox rules to hide replies and study payment flows.
- Impersonation: Criminals send authentic-looking messages from the compromised account or near-lookalike domains, changing bank details or creating urgent payment requests.
- Payment reroute: Funds are diverted to mule accounts domestically, then quickly offshored or converted to crypto.
Warning Signs
- Bank detail changes delivered by email only, especially under time pressure.
- Lookalike domains (e.g., rn vs. m, hyphenated variants) or subtle reply-to discrepancies.
- Vendors “following up” from a new contact thread, or unusual payment destinations.
Protection Strategies
- Business owners: Institute a formal vendor bank-change callback process using a phone number on file—not from the email.
- Finance teams: Enforce dual approval for wires and bulk ACH; delay high-value transfers by 24 hours to enable recall if fraud is detected.
- Tech-savvy users: Enforce phishing-resistant MFA (FIDO2/passkeys) on email and accounting systems; monitor for suspicious mailbox rules and OAuth app grants.
- Consumers/freelancers: For large invoices, verify payment instructions via phone before paying.
Tech Support Fraud
Recent Cases and Financial Impact
• FBI IC3 (2023): Tech support fraud losses approached $1 billion, with more than 19,000 victims reported; older adults are disproportionately targeted (FBI).
• FBI Elder Fraud Report (2023): Americans 60+ reported losses exceeding $3.4 billion across fraud types, with an average loss of $33,915; about 14% lost over $100,000 (FBI).
• Refund/repair scams and fake antivirus pop-ups remain common, often leading to remote-access takeover and bank-drain scenarios.
How This Scam Works
- Bait: A pop-up warns “Your computer is infected—call Microsoft/Apple.” Or the victim receives a call from a fake support line.
- Hook: The scammer convinces the victim to install remote-access tools (e.g., AnyDesk) to “fix” the issue.
- Monetization: They request payment for fake services or manipulate online banking sessions to drain funds or set up Zelle/ACH transfers.
Warning Signs
- Unsolicited calls claiming to be Microsoft/Apple/your bank.
- Pop-ups that lock your browser and provide a phone number to call immediately.
- Requests to install remote-access software or to keep the session secret.
Protection Strategies
- Elderly users and caregivers: Post a visible note near the computer: “Microsoft and banks will NOT call you. Do NOT install remote tools. Hang up.”
- All audiences: Close suspicious browser tabs with Task Manager/Activity Monitor; never call numbers shown in pop-ups. Contact the official support site directly.
- Business owners: Block remote-access tool installs; use application allowlists and DNS filtering; train helpdesk to guide users safely off malicious pop-ups.
Cryptocurrency Schemes
Recent Cases and Financial Impact
• Chainalysis (2024): Illicit crypto transaction volume in 2023 was about $24.2 billion; scam revenue alone was roughly $4.6 billion, while ransomware rebounded to over $1.1 billion (Chainalysis).
• IC3 (2023): Investment fraud (often crypto-themed) accounted for the largest reported losses at approximately $4.57 billion (FBI).
• Pig-butchering investment lures increasingly blend romance/social engineering with fake trading dashboards and deepfake endorsements.
How This Scam Works
- Approach: A friendly contact (social media, messaging app, dating site) builds rapport.
- Proof: They show screenshots of “profits” and invite you to a platform with convincing charts.
- Lock-in: Early withdrawals may work to build trust; then requests escalate. Eventually withdrawals are blocked; “taxes/fees” are demanded.
- Exit: The website vanishes; funds are laundered through mixers, mules, or cross-chain hops.
Warning Signs
- New online acquaintances pitching investments, “insider” crypto tips, or guaranteed returns.
- Unregulated platforms with no verifiable company info or customer support.
- Pressure to “act fast,” secrecy, or to move funds off reputable exchanges into unknown wallets.
Protection Strategies
- Consumers and elderly users: Never move money to an investment platform promoted by someone you met online; consult a trusted family member or advisor first.
- Tech-savvy users: Validate domain age, corporate registration, and regulatory status; test withdrawals with trivial amounts before committing funds.
- Business owners: Add procurement/treasury awareness training about fake escrow and crypto invoice fraud; monitor for executive impersonation tied to “strategic investments.”
Romance and Social Engineering Scams (Including Pig-Butchering)
Recent Cases and Financial Impact
• FTC (2023 data): Romance and investment hybrids remain among the highest-loss categories; overall fraud losses topped $10 billion in 2023 (FTC).
• FBI IC3 (2023): Investment fraud losses were about $4.57 billion; many cases begin as “romance” contacts that pivot to high-yield investment pitches (FBI).
• Elderly users suffer outsized losses: Americans 60+ lost over $3.4 billion across fraud categories, with a significant share linked to online social engineering (FBI Elder Fraud Report, 2023).
How This Scam Works
- Grooming: Scammers build trust through daily chats and emotional mirroring.
- Isolation: They dissuade victims from discussing the relationship with friends/family.
- Monetization: “Emergencies,” “investment opportunities,” or “travel/visa” requests escalate; the victim is nudged to move or invest money repeatedly.
Warning Signs
- Refusal to video chat or always having a reason the camera “won’t work.”
- Stories that quickly introduce money needs or investment opportunities.
- Inconsistencies in photos, job details, or travel timelines.
Protection Strategies
- Elderly users and families: Agree on a “no money to online-only contacts” rule; create a check-in routine with a trusted person before sending funds.
- Consumers: Reverse-image search profile photos; do a quick public records or LinkedIn check for claimed employers.
- Business owners: Include social engineering awareness in wellness and HR communications; employees defrauded outside work can become targets for workplace compromise.
The Evolution of Phishing: Email, Smishing, and Vishing
Recent Cases and Financial Impact
• APWG (2023): More than 4.7 million phishing attacks were recorded in 2023, an all-time high (APWG).
• Verizon DBIR 2024: 68% of breaches involve a human element (phishing, stolen credentials, misuse, or error), showing why social engineering remains the top entry point (Verizon).
• Proofpoint 2024: An overwhelming majority of email-borne threats require user action, and many organizations report at least one successful email-based attack annually (Proofpoint).
How This Scam Works
- Email phishing: Credential theft via login lookalikes, MFA fatigue prompts, or OAuth consent phishing.
- Smishing: Texts impersonate parcel carriers, banks, and IRS/state agencies with malicious links.
- Vishing: Call center operations spoof bank or IT support numbers to elicit OTPs or push approvals.
Warning Signs
- Unexpected “security alerts” or invoices with mismatched sender domains or shortened links.
- Texts urging immediate action with tracking links; banks rarely send login links via SMS.
- Calls that ask you to read one-time passcodes aloud or approve push notifications.
Protection Strategies
- All audiences: Navigate directly to websites or apps—do not click links in unsolicited messages.
- Tech-savvy users: Prefer phishing-resistant MFA (FIDO2/passkeys); review app OAuth permissions; rotate passwords with a manager.
- Business owners: Implement DMARC enforcement, secure email gateways, sandboxing, SMS filtering, and just-in-time phishing simulations with positive reinforcement.
Industry Expert Insights
• AI will “right-shift” social engineering: Expect more real-time deepfake voice and video to press for urgent payments, exploit generative text to personalize lures, and bypass basic verification.
• Identity is the new perimeter: Phishing-resistant MFA, device signals, continuous risk scoring, and least-privilege access are outperforming static passwords and one-time training events.
• Faster money movement increases fraud velocity: Real-time payments and cross-border rails demand “confirm payee” protections, mandatory callbacks, and anomaly detection baked into finance workflows.
• Adversaries target the edges: Home offices, personal email/phones, and third-party vendors remain weak points. Vendor email compromise and invoice fraud will continue to rise without strong supplier verification.
Immediate Action Steps
- Set up verification rituals now: For any payment change or urgent transfer, always use a known phone number to confirm. No exceptions.
- Adopt phishing-resistant MFA: Move executives, finance, and IT to passkeys or FIDO2 security keys.
- Enable transaction friction: Require dual approvals and a cooling-off delay for high-value transfers; monitor and recall quickly if needed.
- Harden email and identity: Enforce DMARC, audit mailbox rules, and review OAuth app grants quarterly.
- Block remote tools and macros: Restrict remote-access software installs and risky scripting environments on endpoints.
- Train for deepfake reality: Teach liveness checks, safe words, and out-of-band verification for any video-call payment request.
- For elderly users: Create a one-page “Do Not Do” list near the phone/computer—no remote tools, no gift cards, no crypto kiosks, hang up on urgent money requests.
- For tech-savvy users: Use hardware keys, password managers, DNS filtering, and app permission audits; monitor your credit and freeze where possible.
- For business owners: Run a BEC tabletop exercise; test your vendor callback process and wire recall playbook this quarter.
Conclusion
Fraudsters have learned to move faster than our habits. In 2025, the biggest wins won’t come from a single product, but from simple, consistent rituals: out-of-band verification, phishing-resistant MFA, dual approvals, and the discipline to insert a pause before money moves. With deepfakes, BEC, tech support scams, and crypto schemes evolving in lockstep, upgrading your verification culture today is the highest-ROI security investment you can make. Share these steps with your team and family—then schedule a 30-minute drill to practice them. That half hour can be the difference between a close call and a seven-figure loss.